Google Cloud – Professional Cloud Developer Certification learning path
Continuing on the Google Cloud Journey, glad to have passed the sixth certification with the Professional Cloud Developer certification.
Google Cloud -Professional Cloud Developer Certification Summary
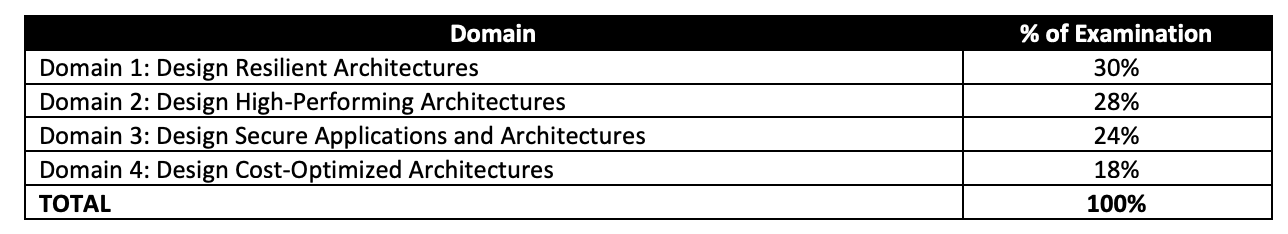
- Had 60 questions to be answered in 2 hours. The number of questions was 50 with the other exams in the same 2 hours.
- Covers a wide range of Google Cloud services mainly focusing on application and deployment services
- Make sure you cover the case studies beforehand. I got ~5-6 questions and it can really be a savior for you in the exams.
- As mentioned for all the exams, Hands-on is a MUST, if you have not worked on GCP before make sure you do lots of labs else you would be absolutely clueless about some of the questions and commands
- I did Coursera and ACloud Guru which is really vast, but hands-on or practical knowledge is MUST.
Google Cloud – Professional Cloud Developer Certification Resources
- Google Cloud – Professional Cloud Developer Exam Guide
- Google Cloud – Professional Cloud Developer Learning Track
- Courses
- Udemy Google Cloud Developer – GCP Professional Certification
- Coursera – Developing Applications with Google Cloud Platform
- Coursera – Getting Started with Google Kubernetes Engine
- Coursera – Architecting with Google Kubernetes Engine: Production
- A Cloud Guru – Google Cloud Certified – Professional Cloud Developer
- Practice tests
- Use Google Free Tier and Qwiklabs as much as possible.
Google Cloud – Professional Cloud Developer Certification Topics
Case Studies
Compute Services
- Compute services like Google Compute Engine and Google Kubernetes Engine are lightly covered more from the security aspects
- Google Compute Engine
- Google Compute Engine is the best IaaS option for compute and provides fine-grained control
- Compute Engine is recommended to be used with Service Account with the least privilege to provide access to Google services and the information can be queried from instance metadata.
- Compute Engine Persistent disks can be attached to multiple VMs in read-only mode.
- Compute Engine launch issues reasons
- Boot disk is full.
- Boot disk is corrupted
- Boot Disk has an invalid master boot record (MBR).
- Quota Errors
- Can be debugged using Serial console
- Preemptible VMs and their use cases. HINT – shutdown script to perform cleanup actions
- Google Kubernetes Engine
- Google Kubernetes Engine, enables running containers on Google Cloud
- Understand GKE containers, Pods, Deployments, Service, DaemonSet, StatefulSets
- Pods are the smallest, most basic deployable objects in Kubernetes. A Pod represents a single instance of a running process in the cluster and can contain single or multiple containers
- Deployments represent a set of multiple, identical Pods with no unique identities. A Deployment runs multiple replicas of the application and automatically replaces any instances that fail or become unresponsive.
- StatefulSets represent a set of Pods with unique, persistent identities and stable hostnames that GKE maintains regardless of where they are scheduled
- DaemonSets manages groups of replicated Pods. However, DaemonSets attempt to adhere to a one-Pod-per-node model, either across the entire cluster or a subset of nodes
- Service is to group a set of Pod endpoints into a single resource. GKE Services can be exposed as ClusterIP, NodePort, and Load Balancer
- Ingress object defines rules for routing HTTP(S) traffic to applications running in a cluster. An Ingress object is associated with one or more Service objects, each of which is associated with a set of Pods
- GKE supports Horizontal Pod Autoscaler (HPA) to autoscale deployments based on CPU and Memory
- GKE supports health checks using
livenessandreadinessprobe- Readiness probes are designed to let Kubernetes know when the app is ready to serve traffic.
- Liveness probes let Kubernetes know if the app is alive or dead.
- Understand Workload Identity for security, which is a recommended way to provide Pods running on the cluster access to Google resources.
- GKE integrates with Istio to provide MTLS feature
- Google App Engine
- Google App Engine is the PaaS option
- Understand how to keep auto-scaling and traffic splitting and migration.
- Know the difference between App Engine Flexible vs Standard
- Cloud Tasks
- is a fully managed service that allows you to manage the execution, dispatch, and delivery of a large number of distributed tasks.
Security Services
- Cloud Identity-Aware Proxy
- Identity-Aware Proxy IAP allows managing access to HTTP-based apps both on Google Cloud and outside of Google Cloud.
- IAP uses Google identities and IAM and can leverage external identity providers as well like OAuth with Facebook, Microsoft, SAML, etc.
- Signed headers using JWT provide secondary security in case someone bypasses IAP.
- Cloud Data Loss Prevention – DLP
- Cloud Data Loss Prevention – DLP is a fully managed service designed to help discover, classify, and protect the most sensitive data.
- provides two key features
- Classification is the process to inspect the data and know what data we have, how sensitive it is, and the likelihood.
- De-identification is the process of removing, masking, redaction, replacing information from data.
- Web Security Scanner
- Web Security Scanner identifies security vulnerabilities in the App Engine, GKE, and Compute Engine web applications.
- scans provide information about application vulnerability findings, like OWASP, XSS, Flash injection, outdated libraries, cross-site scripting, clear-text passwords, or use of mixed content
Networking Services
- Virtual Private Cloud
- Understand Virtual Private Cloud (VPC), subnets, and host applications within them
- Private Access options for services allow instances with internal IP addresses can communicate with Google APIs and services.
- Private Google Access allows VMs to connect to the set of external IP addresses used by Google APIs and services by enabling Private Google Access on the subnet used by the VM’s network interface.
- Cloud Load Balancing
- Google Cloud Load Balancing provides scaling, high availability, and traffic management for your internet-facing and private applications.
Identity Services
- Resource Manager
- Understand Resource Manager the hierarchy Organization -> Folders -> Projects -> Resources
- IAM Policy inheritance is transitive and resources inherit the policies of all of their parent resources.
- Effective policy for a resource is the union of the policy set on that resource and the policies inherited from higher up in the hierarchy.
- Identity and Access Management
- Identify and Access Management – IAM provides administrators the ability to manage cloud resources centrally by controlling who can take what action on specific resources.
- A service account is a special kind of account used by an application or a virtual machine (VM) instance, not a person.
- Understand IAM Best Practices
- Use groups for users requiring the same responsibilities
- Use service accounts for server-to-server interactions.
- Use Organization Policy Service to get centralized and programmatic control over the organization’s cloud resources.
- Domain-wide delegation of authority to grant third-party and internal applications access to the users’ data for e.g. Google Drive etc.
Storage Services
- Cloud Storage
- Cloud Storage is cost-effective object storage for unstructured data and provides an option for long term data retention
- Understand Signed URL to give temporary access and the users do not need to be GCP users HINT: Signed URL would work for direct upload to GCS without routing the traffic through App Engine or CE
- Understand Google Cloud Storage Classes and Object Lifecycle Management to transition objects
- Retention Policies help define the retention period for the bucket, before which the objects in the bucket cannot be deleted.
- Bucket Lock feature allows configuring a data retention policy for a bucket that governs how long objects in the bucket must be retained. The feature also allows locking the data retention policy, permanently preventing the policy from being reduced or removed
- Know Cloud Storage Best Practices esp. GCS auto-scaling performs well if requests ramp up gradually rather than having a sudden spike. Also, retry using exponential back-off strategy
- Cloud Storage can be used to host static websites
- Cloud CDN can be used with Cloud Storage to improve performance and enable caching
- DataStore/FireStore
- Cloud Datastore/Firestore provides a managed NoSQL document database built for automatic scaling, high performance, and ease of application development.
Developer Tools
- Google Cloud Build
- Cloud Build integrates with Cloud Source Repository, Github, and Gitlab and can be used for Continous Integration and Deployments.
- Cloud Build can import source code, execute build to the specifications, and produce artifacts such as Docker containers or Java archives
- Cloud Build build config file specifies the instructions to perform, with steps defined to each task like test, build and deploy.
- Cloud Build supports custom images as well for the steps
- Cloud Build uses a directory named
/workspaceas a working directory and the assets produced by one step can be passed to the next one via the persistence of the/workspacedirectory.
- Google Cloud Code
- Cloud Code helps write, debug, and deploy the cloud-based applications for IntelliJ, VS Code, or in the browser.
- Google Cloud Client Libraries
- Google Cloud Client Libraries provide client libraries and SDKs in various languages for calling Google Cloud APIs.
- If the language is not supported, Cloud Rest APIs can be used.
- Deployment Techniques
- Recreate deployment – fully scale down the existing application version before you scale up the new application version.
- Rolling update – update a subset of running application instances instead of simultaneously updating every application instance
- Blue/Green deployment – (also known as a red/black deployment), you perform two identical deployments of your application
- GKE supports Rolling and Recreate deployments.
- Rolling deployments support
maxSurge(new pods would be created) andmaxUnavailable(existing pods would be deleted)
- Rolling deployments support
- Managed Instance groups support Rolling deployments using the
maxSurge(new pods would be created) andmaxUnavailable(existing pods would be deleted) configurations
- Testing Strategies
- Canary testing – partially roll out a change and then evaluate its performance against a baseline deployment
- A/B testing – test a hypothesis by using variant implementations. A/B testing is used to make business decisions (not only predictions) based on the results derived from data.
Data Services
- Bigtable
- Bigtable is a sparsely populated NoSQL table that can scale to billions of rows and thousands of columns
- Know Bigtable best practices for schema design
- Cloud Pub/Sub
- Understand Cloud Pub/Sub as an asynchronous messaging service
- Know patterns for One to Many, Many to One, and Many to Many
roles/publisherandroles/pubsub.subscriberprovides applications with the ability to publish and consume.
- Cloud SQL
- Cloud SQL is a fully managed service that provides MySQL, PostgreSQL, and Microsoft SQL Server.
- HA configuration provides data redundancy and failover capability with minimal downtime when a zone or instance becomes unavailable due to a zonal outage, or an instance corruption
- Read replicas help scale horizontally the use of data in a database without degrading performance
- Cloud Spanner
- is a fully managed relational database with unlimited scale, strong consistency, and up to 99.999% availability.
- can read and write up-to-date strongly consistent data globally
- Multi-region instances give higher availability guarantees (99.999% availability) and global scale.
- Cloud Spanner’s table interleaving is a good choice for many parent-child relationships where the child table’s primary key includes the parent table’s primary key columns.
Monitoring
- Google Cloud Monitoring or Stackdriver
- provides everything from monitoring, alert, error reporting, metrics, diagnostics, debugging, trace.
- Cloud Monitoring helps gain visibility into the performance, availability, and health of your applications and infrastructure.
- Google Cloud Logging or Stackdriver logging
- Cloud Logging provides real-time log management and analysis
- Cloud Logging allows ingestion of custom log data from any source
- Logs can be exported by configuring log sinks to BigQuery, Cloud Storage, or Pub/Sub.
- Cloud Logging Agent can be installed for logging and capturing application logs.
- Cloud Error Reporting
- counts, analyzes, and aggregates the crashes in the running cloud services
- Cloud Trace
- is a distributed tracing system that collects latency data from the applications and displays it in the Google Cloud Console.
- Cloud Debugger
- is a feature of Google Cloud that lets you inspect the state of a running application in real-time, without stopping or slowing it down
- Debug Logpoints allow logging injection into running services without restarting or interfering with the normal function of the service
- Debug Snapshots help capture local variables and the call stack at a specific line location in your app’s source code
All the Best !!