Google Cloud Armor
- Google Cloud Armor helps protect the applications from multiple types of threats, including distributed denial-of-service (DDoS) attacks and application attacks like cross-site scripting (XSS) and SQL injection (SQLi).
- Google Cloud Armor provides protection only to applications running behind an external load balancer, and several features are only available for external HTTP(S) and TCP/SSL Proxy load balancers.
- Cloud Armor supports applications deployed on Google Cloud, in a hybrid deployment, or in a multi-cloud architecture.
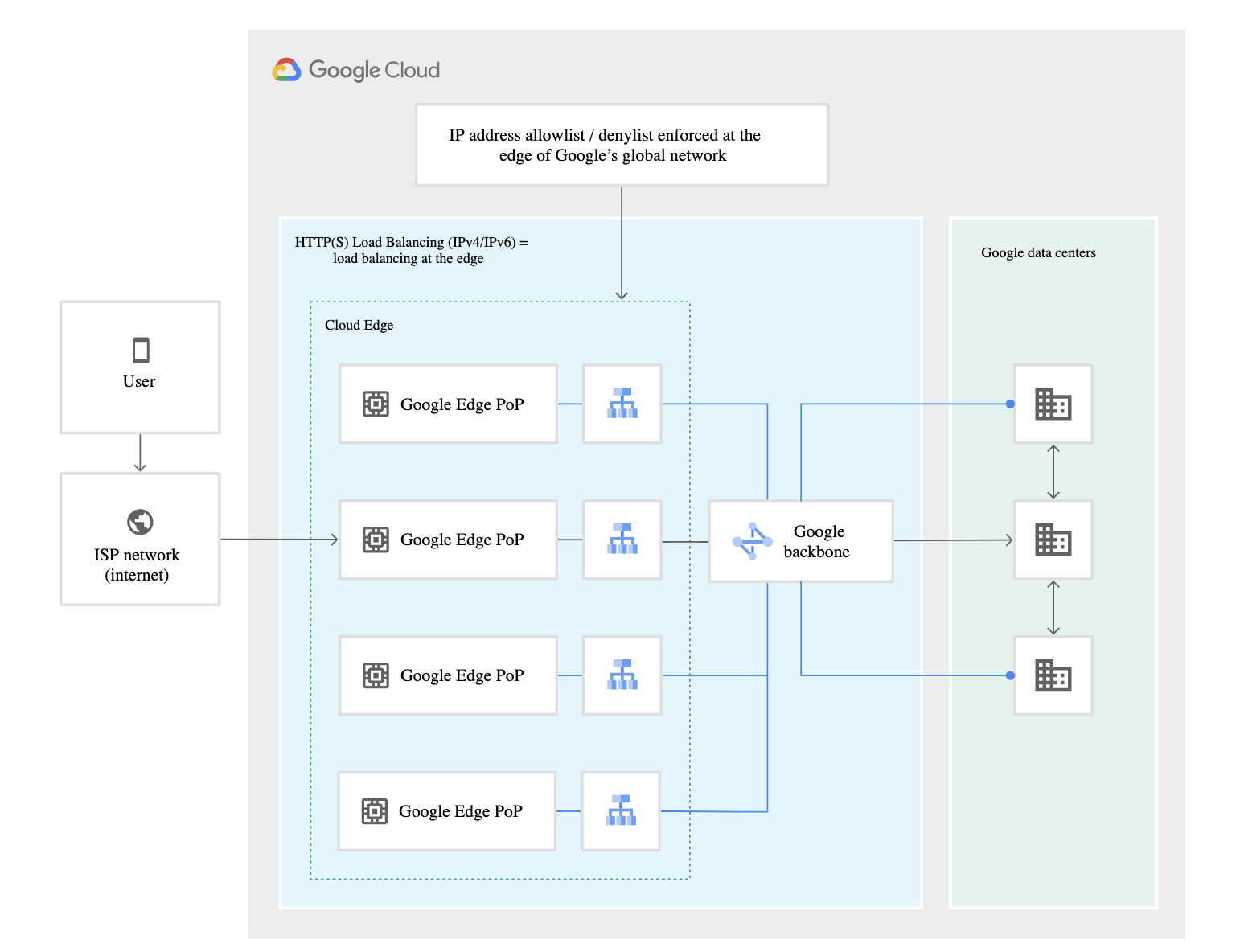
- Cloud Armor is implemented at the edge of Google’s network in Google’s points of presence (PoP).
- Cloud Armor does not support following
- Cloud CDN
- Cloud Storage Buckets
- Internal HTTP/S Load Balancer
- Security policies
- protect applications running behind a load balancer from DDoS and other web-based attacks
- are available only for backend services behind an external HTTP(S) load balancer
- backend service’s load balancing scheme must be
EXTERNAL - backend service’s protocol must be one of
HTTP,HTTPS, orHTTP/2 - backend service can have only one security policy associated with it
- Prioritized rules define configurable match conditions, actions (allow or deny) and order in a security policy
- Rule evaluation order is determined by rule priority, from the lowest number to the highest number
- Security policies are made up of rules that allow or prohibit traffic from IP addresses or ranges defined in the rule
- Preconfigured rules help protect the web applications from common attacks from the internet and help mitigate the OWASP Top 10 risks.
- Adaptive Protection helps protect the applications and services from L7 distributed DDoS attacks by analyzing patterns of traffic to the backend services, detecting and alerting on suspected attacks, and generating suggested WAF rules to mitigate such attacks
- Cloud Armor provides Preview mode that helps evaluate and preview the rules before going live.
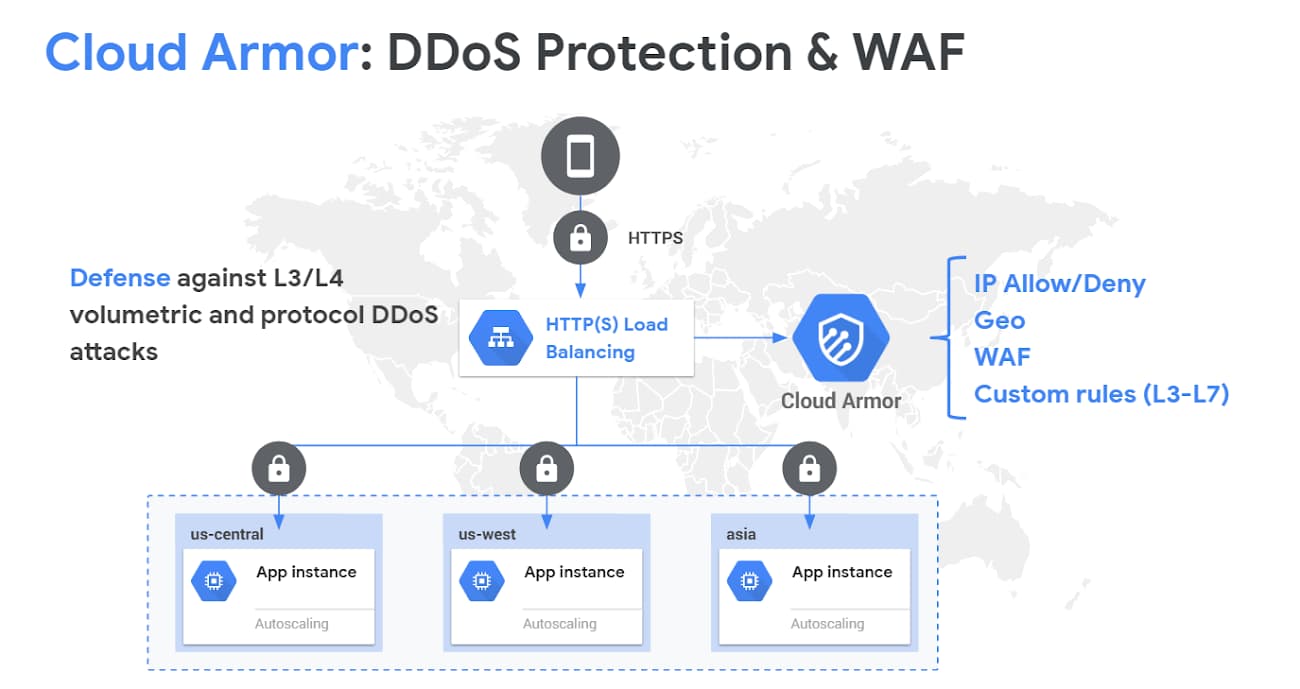
Google Cloud Armor Works
- Cloud Armor provides always-on DDoS protection against network or protocol-based volumetric DDoS attacks for applications behind external HTTP(S), SSL proxy, and TCP proxy load balancers.
- Cloud Armor’s DDoS protection is always-on inline, scaling to the capacity of Google’s global network.
- Cloud Armor is implemented at the edge of Google’s network in Google’s points of presence (PoP).
- Cloud Armor security policies help allow or deny access to the external HTTP(S) load balancer at the Google Cloud edge, as close as possible to the source of incoming traffic.
- Prevents unwelcome traffic from consuming resources or entering the VPC networks
- Backend services behind an external HTTP(S) load balancer also have access to security policies to enforce custom Layer 7 filtering policies, including pre-configured WAF rules to mitigate the OWASP Top 10 web application vulnerability risks.
- Backends to the backend service can be
- VM instances in an instance group,
- zonal network endpoint groups (zonal NEGs), or
- internet network endpoint groups (internet NEGs).
- Google Cloud Armor can be used to protect a hybrid deployment or multi-cloud architecture, the backends must be internet NEGs, or hybrid connectivity NEGs when you use Traffic Director in an on-premises or multi-environment deployment. Google Cloud Armor also protects serverless NEGs when traffic is routed through a load balancer.
GCP Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- GCP services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- GCP exam questions are not updated to keep up the pace with GCP updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Your company offers a popular gaming service. Your instances are deployed with private IP addresses, and external access is granted through a global load balancer. You believe you have identified a potential malicious actor, but aren’t certain you have the correct client IP address. You want to identify this actor while minimizing disruption to your legitimate users. What should you do?
- Create a Cloud Armor Policy rule that denies traffic and review necessary logs.
- Create a Cloud Armor Policy rule that denies traffic, enable preview mode, and review necessary logs.
- Create a VPC Firewall rule that denies traffic, enable logging and set enforcement to disabled, and review necessary logs.
- Create a VPC Firewall rule that denies traffic, enable logging and set enforcement to enabled, and review necessary logs
