Table of Contents
hide
AWS Certified Advanced Networking – Specialty ANS-C01 Exam Learning Path
I recently certified/recertified for the AWS Certified Advanced Networking – Specialty (ANS-C01). Frankly, Networking is something that I am still diving deep into and I just about managed to get through. So a word of caution, this exam is inline or tougher than the professional exams, especially for the reason that some of the Networking concepts covered are not something you can get your hands dirty with easily.
AWS Certified Advanced Networking – Specialty ANS-C01 Exam Content
- AWS Certified Advanced Networking – Specialty (ANS-C01) exam focuses on the AWS Networking concepts. It basically validates
- Design and develop hybrid and cloud-based networking solutions by using AWS
- Implement core AWS networking services according to AWS best practices
- Operate and maintain hybrid and cloud-based network architecture for all AWS services
- Use tools to deploy and automate hybrid and cloud-based AWS networking tasks
- Implement secure AWS networks using AWS native networking constructs and services
Refer to AWS Certified Advanced Networking – Specialty Exam Guide 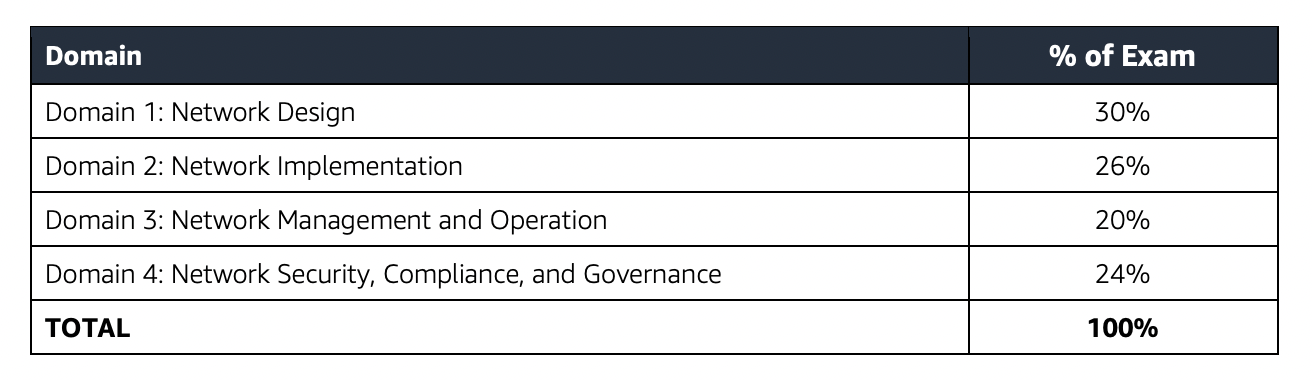
AWS Certified Advanced Networking – Specialty (ANS-C01) Exam Resources
- Online Courses
- Stephane Maarek – AWS Certified Advanced Networking Specialty
- Adrian Cantrill – AWS Certified Advanced Networking – Specialty
- Whizlabs – AWS Certified Advanced Networking Specialty Course
- Practice Tests
AWS Certified Advanced Networking – Specialty (ANS-C01) Exam Summary
-
Specialty exams are tough, lengthy, and tiresome. Most of the questions and answers options have a lot of prose and a lot of reading that needs to be done, so be sure you are prepared and manage your time well.
- ANS-C01 exam has 65 questions to be solved in 170 minutes which gives you roughly 2 1/2 minutes to attempt each question. 65 questions consists of 50 scored and 15 unscored questions.
- ANS-C01 exam includes two types of questions, multiple-choice and multiple-response.
- ANS-C01 has a scaled score between 100 and 1,000. The scaled score needed to pass the exam is 750.
- Each question mainly touches multiple AWS services.
- Specialty exams currently cost $ 300 + tax.
- You can get an additional 30 minutes if English is your second language by requesting Exam Accommodations. It might not be needed for Associate exams but is helpful for Professional and Specialty ones.
- As always, mark the questions for review and move on and come back to them after you are done with all.
- As always, having a rough architecture or mental picture of the setup helps focus on the areas that you need to improve. Trust me, you will be able to eliminate 2 answers for sure and then need to focus on only the other two. Read the other 2 answers to check the difference area and that would help you reach the right answer or at least have a 50% chance of getting it right.
- AWS exams can be taken either remotely or online, I prefer to take them online as it provides a lot of flexibility. Just make sure you have a proper place to take the exam with no disturbance and nothing around you.
- Also, if you are taking the AWS Online exam for the first time try to join at least 30 minutes before the actual time as I have had issues with both PSI and Pearson with long wait times.
AWS Certified Advanced Networking – Specialty (ANS-C01) Exam Topics
- AWS Certified Networking – Specialty (ANS-C01) exam focuses a lot on Networking concepts involving Hybrid Connectivity with Direct Connect, VPN, Transit Gateway, Direct Connect Gateway, and a bit of VPC, Route 53, ALB, NLB & CloudFront.
Networking & Content Delivery
- Virtual Private Cloud – VPC
- Understand VPC, Subnets
- AWS allows extending the VPC by adding a secondary VPC
- Understand Security Groups, NACLs
- VPC Flow Logs
- help capture information about the IP traffic going to and from network interfaces in the VPC and can help in monitoring the traffic or troubleshooting any connectivity issues
- NACLs are stateless and how it is reflected in VPC Flow Logs
- If ACCEPT followed by REJECT, inbound was accepted by Security Groups and ACLs. However, rejected by NACLs outbound
- If REJECT, inbound was either rejected by Security Groups OR NACLs.
- Use
pkt-dstaddrinstead ofdstaddrto track the destination address asdstaddrrefers to the primary ENI address always and not the secondary addresses. - Pattern: VPC Flow Logs -> CloudWatch Logs -> (Subscription) -> Kinesis Data Firehose -> S3/Open Search.
- DHCP Option Sets esp. how to resolve DNS from both on-premises data center and AWS.
- VPC Peering
- helps point-to-point connectivity between 2 VPCs which can be in the same or different regions and accounts.
- know VPC Peering Limitations esp. it does not allow overlapping CIDRs and transitive routing.
- Placement Groups determine how the instances are placed on the underlying hardware
- Cluster Placement Groups & Enhanced Networking with MTU & Jumbo frames can be used for HPC
- VRF – Virtual Routing & Forwarding can be used to route traffic to the same customer gateway from multiple VPCs, that can be overlapping.
- VPC Endpoints
- VPC Gateway Endpoints for connectivity with S3 & DynamoDB i.e. VPC -> VPC Gateway Endpoints -> S3/DynamoDB.
- VPC Interface Endpoints or Private Links for other AWS services and custom hosted services i.e. VPC -> VPC Interface Endpoint OR Private Link -> S3/Kinesis/SQS/CloudWatch/Any custom endpoint.
- S3 gateway endpoints cannot be accessed through VPC Peering, VPN, or Direct Connect. Need HTTP proxy to route traffic.
- S3 Private Link can be accessed through VPC Peering, VPN, or Direct Connect. Need to use an endpoint-specific DNS name.
- VPC endpoint policy can be configured to control which S3 buckets can be accessed and the S3 Bucket policy can be used to control which VPC (includes all VPC Endpoints) or VPC Endpoint can access it.
- Private Link Patterns
- Private links allow connectivity for overlapping CIDRs which VPC peering would not.
- Connections can be initiated in only one direction i.e. consumer to provider
- Provides fine-grained access control and only the endpoint is shared and nothing else.
- Private DNS does not support multiple interface endpoints. Use two endpoints with load balancing with Route 53 weighted policy.
- VPC Network Access Analyzer
- helps identify unintended network access to the resources on AWS.
- Transit Gateway
- helps consolidate the AWS VPC routing configuration for a region with a hub-and-spoke architecture.
- Appliance Mode ensures that network flows are symmetrically routed to the same AZ and network appliance
- Transit Gateway Connect attachment can be used to connect SD-WAN to AWS Cloud. This supports GRE.
- Transit Gateways are regional and Peering can connect Transit Gateways across regions.
- Transit Gateway Network Manager includes events and metrics to monitor the quality of the global network, both in AWS and on-premises.
- VPC Routing Priority
- NAT Gateways
- for HA, Scalable, Outgoing traffic. Does not support Security Groups or ICMP pings.
- times out the connection if it is idle for 350 seconds or more. To prevent the connection from being dropped, initiate more traffic over the connection or enable TCP keepalive on the instance with a value of less than 350 seconds.
- supports Private NAT Gateways for internal communication.
- Virtual Private Network
- to establish connectivity between the on-premises data center and AWS VPC
- Direct Connect
- to establish connectivity between the on-premises data center and AWS VPC and Public Services
- Direct Connect connections – Dedicated and Hosted connections
- Understand how to create a Direct Connect connection
- LOA-CFA provides the details for partners to connect to the AWS Direct Connect location
- Virtual interfaces options – Private Virtual Interface for VPC resources and Public Virtual Interface for Public Resources
- Private VIF is for resources within a VPC
- Public VIF is for AWS public resources
- Private VIF has a limit of 100 routes and Public VIF of 1000 routes. Summarize the routes if you need to configure more.
- Understand setup Private and Public VIF
- Understand High Availability options based on cost and time i.e. Second Direct Connect connection OR VPN connection
- Direct Connect Gateway
- it provides a way to connect to multiple VPCs from an on-premises data center using the same Direct Connect connection.
- can connect to VGW or TGW.
- Understand Active/Passive Direct Connect
- supports MACsec which delivers native, near line-rate, point-to-point encryption ensuring that data communications between AWS and the data center, office, or colocation facility remain protected.
- Understand Route Propagation, propagation priority, BGP connectivity
- BGP prefers the shortest AS PATH to get to the destination. Traffic from the VPC to on-premises uses the primary router. This is because the secondary router advertises a longer AS-PATH.
- AS PATH prepending doesn’t work when the Direct Connect connections are in different AWS Regions than the VPC.
- AS PATH works from AWS to on-premises and Local Pref from on-premises to AWS
- Use Local Preference BGP community tags to configure Active/Passive when the connections are from different regions. The higher tag has a higher preference for 7224:7300 > 7224:7100
- NO_EXPORT works only for Public VIFs
- 7224:9100, 7224:9200, and 7224:9300 apply only to public prefixes. Usually used to restrict traffic to regions. Can help control if routes should propagate to the local Region only, all Regions within a continent, or all public Regions.
- 7224:9100 — Local AWS Region
- 7224:9200 — All AWS Regions for a continent, North America–wide, Asia Pacific, Europe, the Middle East and Africa
- 7224:9300 — Global (all public AWS Regions)
- 7224:8100 — Routes that originate from the same AWS Region in which the AWS Direct Connect point of presence is associated.
- 7224:8200 — Routes that originate from the same continent with which the AWS Direct Connect point of presence is associated.
- No-tag — Global (all public AWS Regions).
- Route 53
- provides a highly available and scalable DNS web service.
- Routing Policies and their use cases Focus on Weighted, Latency, and Failover routing policies.
- supports Alias resource record sets, which enables routing of queries to a CloudFront distribution, Elastic Beanstalk, ELB, an S3 bucket configured as a static website, or another Route 53 resource record set.
- CNAME does not support zone apex or root records.
- Route 53 DNSSEC
- secures DNS traffic, and helps protect a domain from DNS spoofing man-in-the-middle attacks.
- Requirements
- Asymmetric Customer Managed Keys
- us-east-1 with ECC_NIST_P256 spec
- Route 53 Resolver DNS Firewall
- protection for outbound DNS requests from the VPCs and can monitor and control the domains that the applications can query.
- allows you to define allow and deny list.
- can be used for DNS exfiltration.
- supports FirewallFailOpen configuration which determines how Route 53 Resolver handles queries during failures.
- disabled, favors security over availability and blocks queries that it is unable to evaluate properly.
- enabled, favors availability over security and allows queries to proceed if it is unable to properly evaluate them.
- Route 53 Resolver (Hybrid DNS)
- Inbound Endpoint for On-premises -> AWS
- Outbound Endpoint for AWS -> On-premises
- Route 53 DNS Query Logging
- Can be logged to CloudWatch logs, S3, and Kinesis Data Firehose
- Route 53 Resolver rules take precedence over privately hosted zones.
- Route 53 Split View DNS helps to have the same DNS to access a site externally and internally
- Know the Domain Migration process
- CloudFront
- provides a fully managed, fast CDN service that speeds up the distribution of static, dynamic web, or streaming content to end-users.
- supports geo-restriction, WAF & AWS Shield for protection.
- provides Cloud Functions (Edge location) & Lambda@Edge (Regional location) to execute scripts closer to the user.
- supports encryption at rest and end-to-end encryption
- Viewer Protocol Policy and Origin Protocol Policy to enforce HTTPS
- Integrates with ACM and requires certs to be in the us-east-1 region
- Underlying origin can be applied certs from ACM or issued by the third party.
- CloudFront Origin Shield
- helps improve the cache hit ratio and reduce the load on the origin.
- requests from other regional caches would hit the Origin shield rather than the Origin.
- should be placed at the regional cache and not in the edge cache
- should be deployed to the region closer to the origin server
- Global Accelerator
- provides 2 static IPs
- does not support client IP address preservation for NLB and Elastic IP address endpoints.
- does not support IPv6 address
- know CloudFront vs Global Accelerator
- Understand ELB, ALB and NLB
- Differences between ALB and NLB
- ALB provides Content, Host, and Path-based Routing while NLB provides the ability to have a static IP address
- Maintain original Client IP to the backend instances using X-Forwarded-for and Proxy Protocol
- ALB/NLB do not support TLS renegotiation or mutual TLS authentication (mTLS). For implementing mTLS, use NLB with TCP listener on port 443 and terminate on the instances.
- NLB
- also provides local zonal endpoints to keep the traffic within AZ
- can front Private Link endpoints and provide static IPs.
- ALB supports Forward Secrecy, through Security Policies, that provide additional safeguards against the eavesdropping of encrypted data, through the use of a unique random session key.
- Supports sticky session feature (session affinity) to enable the LB to bind a user’s session to a specific target. This ensures that all requests from the user during the session are sent to the same target. Sticky Sessions is configured on the target groups.
- Gateway Load Balancer – GWLB
- helps deploy, scale, and manage virtual appliances, such as firewalls, IDS/IPS systems, and deep packet inspection systems.
- Athena integrates with S3 only and not with CloudWatch logs.
- Transit VPC
- helps connect multiple, geographically disperse VPCs and remote networks in order to create a global network transit center.
- Use Transit Gateway instead now.
- Know CloudHub and its use case
Security
- AWS GuardDuty
- managed threat detection service
- provides Malware protection
- AWS Shield
- managed DDoS protection service
- AWS Shield Advanced provides 24×7 access to the AWS Shield Response Team (SRT), protection against DDoS-related spike, and DDoS cost protection to safeguard against scaling charges.
- WAF as Web Traffic Firewall
- helps protect web applications from attacks by allowing rules configuration that allow, block, or monitor (count) web requests based on defined conditions.
- integrates with CloudFront, ALB, API Gateway to dynamically detect and prevent attacks
- Network Firewall
- provides IDS/IPS – Stateless and Stateful firewall rules – Allow, Deny, Forward
- Used with Private Workspaces
- AWS Inspector
- is a vulnerability management service that continuously scans the AWS workloads for vulnerabilities
Monitoring & Management Tools
- Understand AWS CloudFormation esp. in terms of Network creation.
- Custom resources can be used to handle activities not supported by AWS
- While configuring VPN connections use
depends_onon route tables to define a dependency on other resources as the VPN gateway route propagation depends on a VPC-gateway attachment when you have a VPN gateway.
- AWS Config
- fully managed service that provides AWS resource inventory, configuration history, and configuration change notifications to enable security, compliance, and governance.
- can be used to monitor resource changes e.g. Security Groups and invoke Systems Manager Automation scripts for remediation.
- CloudTrail for audit and governance
Integration Tools
- CloudWatch integration with SNS and Lambda can help in notification
Networking Architecture Patterns
- AWS Certification – Networking Services – Cheat Sheet
- AWS Network Connectivity Options
- AWS Network Architecture Patterns
- DNS Resolution between On-premises and AWS
- Direct Connect + VPN (Security over DX)
- Application VPC -> GWLB -> Transit Gateway -> Inspection VPC OR THIS
- Centralized Egress through NAT & THIS
- ALB -> Private Link -> NLB -> Applications
- Private Link -> NLB -> ALB -> Applications
- File Gateway -> DX -> S3 Interface Endpoint -> S3
- Connectivity Type Selection Summary
- Centralizing VPC Endpoints with Transit Gateway
- Accessing S3 through DX using S3 Interface Endpoint – on-premises -> Direct Connect -> AWS -> S3 Private Link -> S3
- Accessing S3 through DX using S3 Gateway Endpoints – on-premises -> Direct Connect -> AWS -> HTTPS Proxy -> S3 Gateway Endpoint -> S3
- Transit Gateway Connect + SD-WAN + GRE
- Whitepaper: AWS VPC Connectivity Options
- Whitepaper: Building a Scalable and Secure Multi-VPC AWS Network Infrastructure
- Whitepaper: Hybrid Connectivity
- Whitepaper: AWS Single Region Multi VPC Connectivity
AWS Certified Advanced Networking – Specialty (ANS-C01) Exam Day
- Make sure you are relaxed and get some good night’s sleep. The exam is not tough if you are well-prepared.
- If you are taking the AWS Online exam
- Try to join at least 30 minutes before the actual time as I have had issues with both PSI and Pearson with long wait times.
- The online verification process does take some time and usually, there are glitches.
- Remember, you would not be allowed to take the take if you are late by more than 30 minutes.
- Make sure you have your desk clear, no hand-watches, or external monitors, keep your phones away, and nobody can enter the room.
Finally, All the Best 🙂