Table of Contents
hide
AWS Network Architecture Patterns
On-premises -> S3 Private Link -> S3 (Without Internet Gateway or S3 Gateway Endpoint)
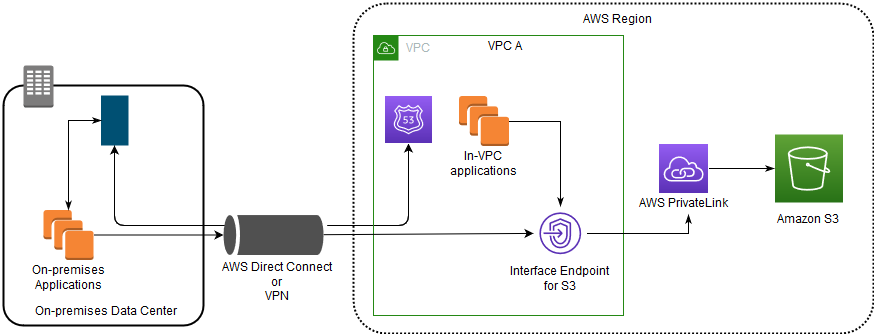
- Interface endpoints in the VPC can route both in-VPC applications and on-premises applications to S3 over the Amazon network.
- On-premises network uses Direct Connect or AWS VPN to connect to VPC.
- On-premises applications in VPC A use endpoint-specific DNS names to access S3 through the S3 interface endpoint.
- On-premises applications send data to the interface endpoint in the VPC through AWS Direct Connect (or AWS VPN). AWS PrivateLink moves the data from the interface endpoint to S3 over the AWS network.
- VPC applications can also send traffic to the interface endpoint. AWS PrivateLink moves the data from the interface endpoint to S3 over the AWS network.
On-premises -> Proxy -> Gateway Endpoint -> S3
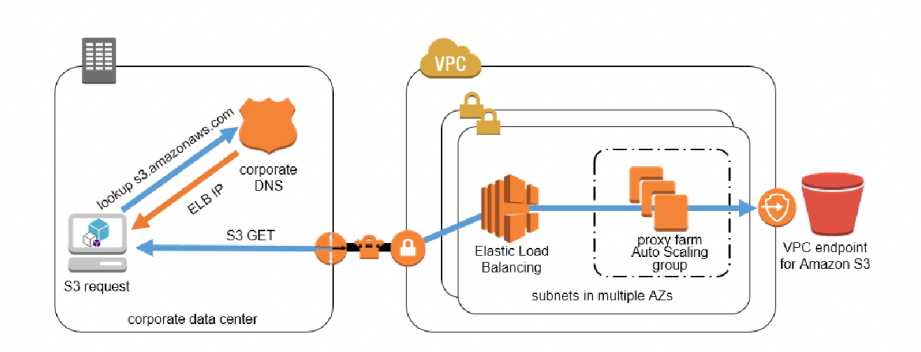
- VPC endpoints are only accessible from EC2 instances inside a VPC, a local instance must proxy all remote requests before they can
utilize a VPC endpoint connection. - Proxy farm proxies S3 traffic to the VPC endpoint. Configure an Auto Scaling group to manage the proxy servers and automatically grow or shrink the number of required instances based on proxy server load.
Direct Connect Gateway + Transit Gateway
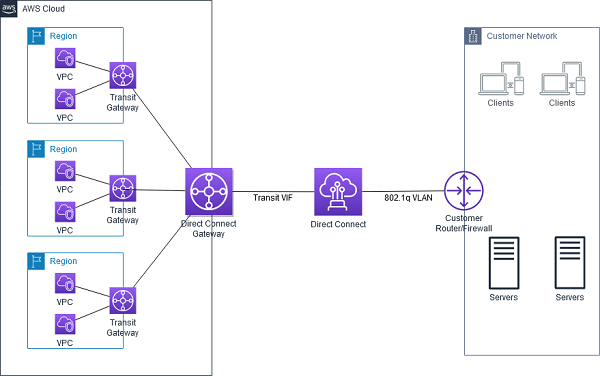
- AWS Direct Connect Gateway does not support transitive routing and has limits on the number of VGWs that can be connected.
- AWS Direct Connect Gateway can be combined with AWS Transit Gateway using transit VIF attachment which enables your network to connect up to three regional centralized routers over a private dedicated connection
- DX Gateway + TGW simplifies the management of connections between a VPC and the on-premises networks over a private connection that can reduce network costs, increase bandwidth throughput, and provide a more consistent network experience than internet-based connections.
- With AWS Transit Gateway connected to VPCs, full or partial mesh connectivity can be achieved between the VPCs.
AWS Direct Connect with VPN as Backup
- Be sure that you use the same virtual private gateway for both Direct Connect and the VPN connection to the VPC.
- If you are configuring a Border Gateway Protocol (BGP) VPN, advertise the same prefix for Direct Connect and the VPN.
- If you are configuring a static VPN, add the same static prefixes to the VPN connection that you are announcing with the Direct Connect virtual interface.
- If you are advertising the same routes toward the AWS VPC, the Direct Connect path is always preferred, regardless of AS path prepending.
AWS Direct Connect + VPN
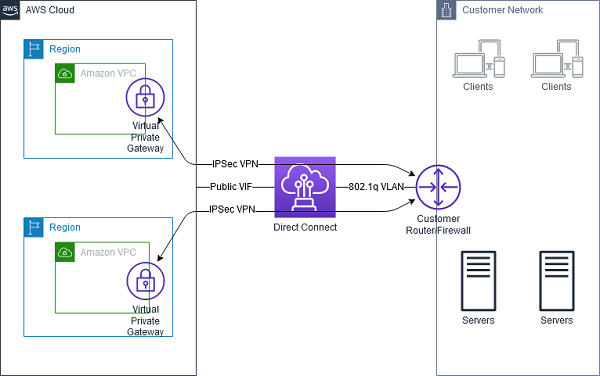
- AWS Direct Connect + VPN combines the benefits of the end-to-end secure IPSec connection with low latency and increased bandwidth of the AWS Direct Connect to provide a more consistent network experience than internet-based VPN connections.
- AWS Direct Connect public VIF establishes a dedicated network connection between the on-premises network to public AWS resources, such as an Amazon virtual private gateway IPsec endpoint.
- A BGP connection is established between the AWS Direct Connect and your router on the public VIF.
-
Another BGP session or a static router will be established between the virtual private gateway and your router on the IPSec VPN tunnel.
AWS Private Link -> NLB -> ALB
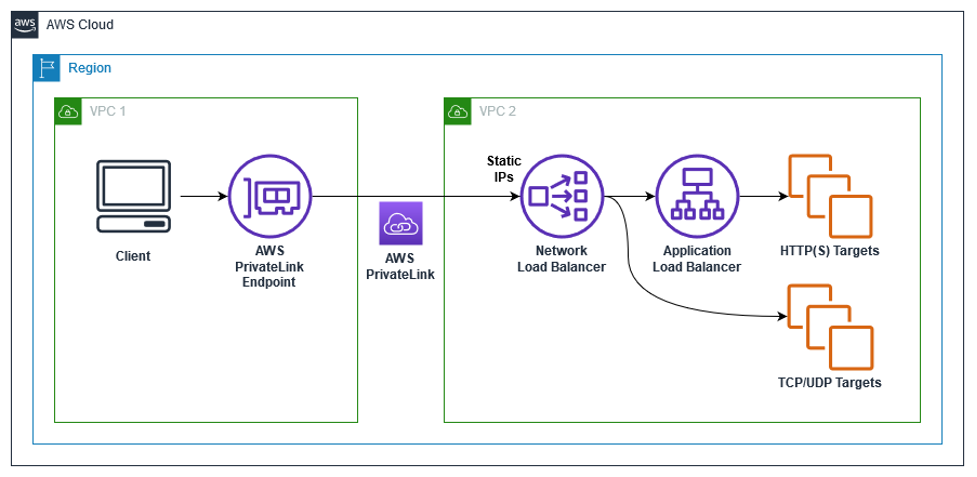
- AWS PrivateLink for ALB allows customers to utilize PrivateLink on NLB and route this traffic to a target ALB to utilize the layer 7 benefits.
- Static NLB IP Addresses for ALB – with one static IP per AZ on NLB allows full control over the IP addresses and enables various use cases as follows:
- Allow listing of IP addresses for firewall rules.
- Pointing a DNS Zone apex to an application fronted by an ALB. Utilizing ALB as a target of NLB, a DNS A-record type can be used to resolve your zone apex to the NLB static IP addresses.
- When legacy clients cannot utilize DNS resulting in a need for hard-coded IP addresses.
Centralized Egress: Transit Gateway + NAT Gateway
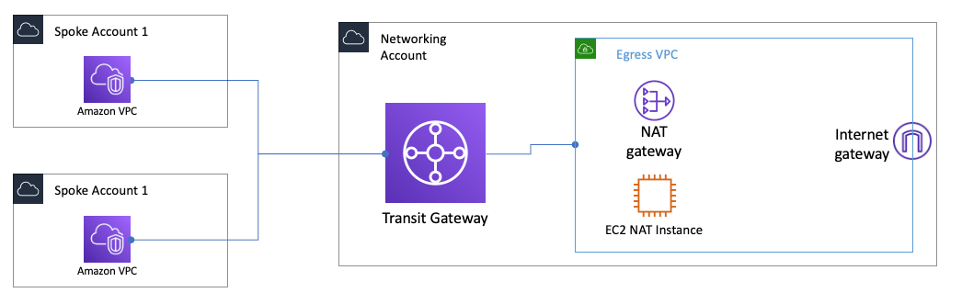
- A separate egress VPC in the network services account can be created to route all egress traffic from the spoke VPCs via a NAT gateway sitting in this VPC using Transit Gateway
- As the NAT gateway has an hourly charge, deploying a NAT gateway in every spoke VPC can become cost prohibitive and centralizing NAT can provide cost benefits
- In some edge cases when huge amounts of data is sent through the NAT gateway from a VPC, keeping the NAT local in the VPC to avoid the Transit Gateway data processing charge might be a more cost-effective option.
- Two NAT gateways (one in each AZ) provide High Availability.
Direct Connect with High Resiliency – 99.9
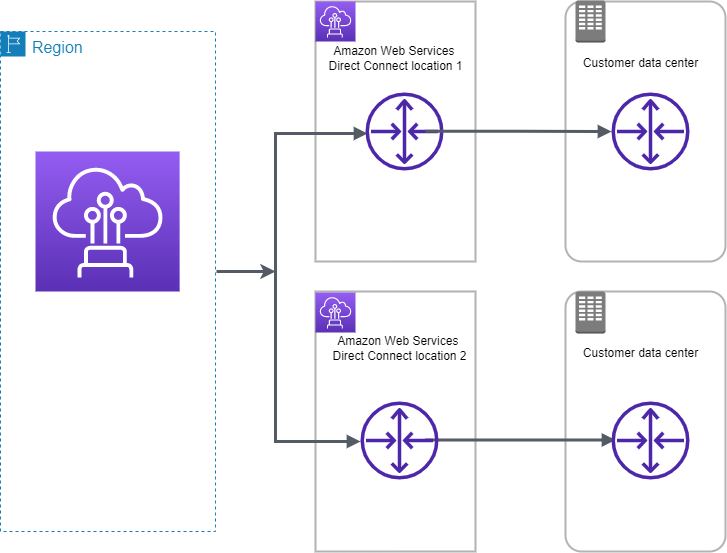
- For critical production workloads that require high resiliency, it is recommended to have one connection at multiple locations.
- ensures resilience to connectivity failure due to a fiber cut or a device failure as well as a complete location failure. You can use AWS Direct Connect gateway to access any AWS Region (except AWS Regions in China) from any AWS Direct Connect location.
Direct Connect with Maximum Resiliency – 99.99
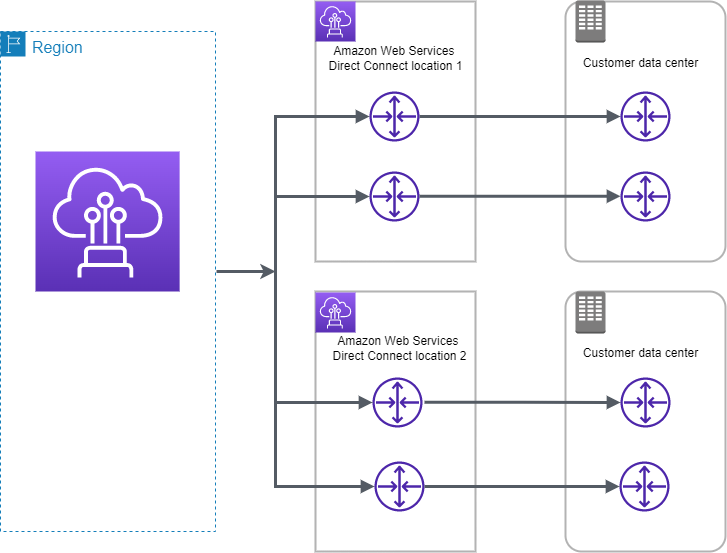
- Maximum resilience is achieved by separate connections terminating on separate devices in more than one location
- ensures resilience to device failure, connectivity failure, and complete location failure.
