Certified Kubernetes Security Specialist CKS Learning Path
With Certified Kubernetes Security Specialist CKS certification, I have recertified the triad of Kubernetes certification. After knowing how to use and administer Kubernetes, the last piece was to understand the security intricacies and CKS preparation does provide you a deep dive into it.
- CKS is more of an open-book test, where you have access to the official Kubernetes documentation exam, but it focuses more on hands-on experience.
- CKS focuses on securing container-based applications and Kubernetes platforms during build, deployment, and runtime.
- Unlike AWS and GCP certifications, you would be required to solve, debug actual problems, and provision resources on a live Kubernetes cluster.
- Even though it is an open book test, you need to know where the information is.
- Trust me, if you are not prepared this time is not going to be sufficient.
CKS Exam Pattern
- CKS exam curriculum includes these general domains and their weights on the exam:
- Cluster Setup – 10%
- Cluster Hardening – 15%
- System Hardening – 15%
- Minimize Microservice Vulnerabilities – 20%
- Supply Chain Security – 20%
- Monitoring, Logging and Runtime Security – 20%
- CKS exam has been upgraded and requires you to solve 15-20 questions in 2 hours. I got 16 questions.
- CKS was already upgraded to use the k8s 1.28 version. But it keeps on being upgraded with new Kubernetes versions.
- You are allowed to open another browser tab which can be from kubernetes.io or other product documentation like Falco. Do not open any other windows.
- Exam questions can be attempted in any order and don’t have to be sequential. So be sure to move ahead and come back later.
CKS Exam Preparation and Tips
- I used the courses from KodeKloud CKS for practicing and it would be good enough to cover what is required for the exam.
- Prepare yourself with the imperative commands as much as you can. This will help cut down the time required to solve half of the questions.
- Each exam question carries weight so be sure you attempt the exams with higher weights before focusing on the lower ones. So target the ones with higher weights and quicker solutions like debugging ones.
- CKS exam provides 6-8 different preconfigured K8s clusters. Each question refers to a different Kubernetes cluster, and the context needs to be switched. Be sure to execute the
kubectl use contextcommand, which is available with every question and you just need to copy-paste it. - Check for the namespace mentioned in the question, to find resources and create resources. Use the
-n <namespace> - You would be performing most of the interaction from the client node. However, pay attention to the node (master or worker) you need to execute the exams and make sure you return back to the base node.
- With CKS is important to move the master node for any changes to the cluster
kube-apiserver. - SSH to nodes and gaining root access is allowed if needed.
- Read carefully the Information provided within the questions with the i mark. They would provide very useful hints in addressing the question and save time. for e.g., namespaces to look into for a failed pod, what has already been created like configmap, secrets, network policies so that you do not create the same.
- Make sure you know the imperative commands to create resources, as you won’t have much time to create and edit YAML files.
- If you need to edit further use
--dry-run=client -o yamlto get a headstart with the YAML spec file and edit the same. - I personally use
alias kk=kubectlto avoid typingkubectl
CKS Resources
- Go through the CKS Curriculum
- Linux Foundation CKS Course and CKS Certification Bundle
- KodeKloud – Mumshad Mannambeth Certified Kubernetes Security Specialist (CKS) with Practice Tests
- Excellent course which covers the right topics required for the CKS
- It also provides hands-on labs for each of the topics, giving you actual experience working on the Kubernetes cluster.
- Make sure to practice the labs, as long as you don’t need to refer to the hints and can do most of it without documentation.
- Udemy Kubernetes CKS 2021 Complete Course – Theory – Practice
- Cover Kubernetes Security Overview
- Practice CKS Exercises
- Cover Kubernetes tutorials which provide a good hands-on guide
- Cover kubectl cheatsheet for commands
- Cover Tasks from Kubernetes documentation
CKS Key Topics
Cluster Setup – 10%
- Practice CKS Exercises – Cluster Setup
- Securing a Cluster covers a lot of these features
- Use Network security policies to restrict cluster level access
- Understand Network Policies
- Use Network security policies to restrict cluster level access
- Exam tip: Know how to create Network Policies using proper selectors
- Use CIS benchmark to review the security configuration of Kubernetes components (etcd, kubelet, kubedns, kubeapi)
- Center of Internet Security – CIS defines security best practices for Kubernetes and can help evaluate and recommendation for the fixes.
- Aqua Security kube-bench is a free tool that can help evaluate the k8s cluster for CIS rules.
- Exam tip: Know how to read the CIS report, identify failures, map it to the recommendation, and fix the same.
- Properly set up Ingress objects with security control
- Ingress endpoint can be configured with TLS endpoint
- Exam tip: Know how to create a TLS secret and associate the same with the Ingress
- Protect node metadata and endpoints
- Authentication using Certificates and Service Accounts
- Authorization using Node and RBAC
- Exam tip: Know how to create Service Accounts, Roles, and Cluster Roles and associate them together using Role Binding and Cluster Role Binding.
- Exam tip: Know to create Service Accounts with automount disabled using the
automountServiceAccountTokenflag.
- Minimize use of, and access to, GUI elements
- Kubernetes Dashboard is a GUI component that needs to be secured.
- Verify platform binaries before deploying
- Exam tip: Know how to verify platform binaries digest using
sha
- Exam tip: Know how to verify platform binaries digest using
Cluster Hardening – 15%
- Practice CKS Exercises – Cluster Harding
- Restrict access to Kubernetes API
- Use Role-Based Access Controls to minimize exposure
- Exam tip: Know how to create Service Accounts, Roles, and Cluster Roles and associate them together using Role Binding and Cluster Role Binding.
- Exercise caution in using service accounts e.g. disable defaults, minimize permissions on newly created ones.
- Exam tip: Know how to create Service Accounts, Roles, and Cluster Roles and associate them together using Role Binding and Cluster Role Binding.
- Exam tip: Know
automountServiceAccountTokencan be used to prevent the service account from being auto-mounted.
- Update Kubernetes frequently
- Kubernetes supports N to N-2 versions and it is recommended to upgrade the components
- Exam tip: Know how to upgrade a Kubernetes cluster (although it did not appear on my exam)
System Hardening – 15%
- Practice CKS Exercises – System Harding
- Minimize host OS footprint (reduce attack surface)
- Control access using SSH, disable root and password-based logins
- Remove unwanted packages and ports
- Minimize IAM roles
- IAM roles are usually with Cloud providers and relate to the least privilege access principle.
- Minimize external access to the network
- External access can be controlled using Network Policies through egress policies.
- Appropriately use kernel hardening tools such as AppArmor, seccomp
- Runtime classes provided by gvisor and kata containers can help provide further isolation of the containers
- Secure Computing – Seccomp tool helps control syscalls made by containers
- AppArmor can be configured for any application to reduce its potential host attack surface and provide a greater in-depth defense.
- PodSecurityPolicies – PSP enables fine-grained authorization of pod creation and updates.
-
Apply host updates
-
Install minimal required OS fingerprint
-
Identify and address open ports
-
Remove unnecessary packages
-
Protect access to data with permissions
-
- Exam tip: Know how to load AppArmor profiles, and enable them for the pods. AppArmor is in beta and needs to be enabled using
container.apparmor.security.beta.kubernetes.io/<container_name>: <profile_ref>
Minimize Microservice Vulnerabilities – 20%
- Practice CKS Exercises – Minimize Microservice Vulnerabilities
- Setup appropriate OS-level security domains e.g. using PSP, OPA, security contexts.
- Pod Security Contexts help define security for pods and containers at the pod or at the container level. Capabilities can be added at the container level only.
- Pod Security Policies enable fine-grained authorization of pod creation and updates and is implemented as an optional admission controller.
- Open Policy Agent helps enforce custom policies on Kubernetes objects without recompiling or reconfiguring the Kubernetes API server.
- Admission controllers
- can be used for validating configurations as well as mutating the configurations.
- Mutating controllers are triggered before validating controllers.
- Allows extension by adding custom controllers using MutatingAdmissionWebhook and ValidatingAdmissionWebhook.
- Exam tip: Know how to configure Pod Security Context, Pod Security Policies
- Manage Kubernetes secrets
- Exam Tip: Know how to read secret values, create secrets and mount the same on the pods.
- Use container runtime sandboxes in multi-tenant environments (e.g. gvisor, kata containers)
- Exam tip: Know how to create a Runtime and associate it with a pod using
runtimeClassName
- Exam tip: Know how to create a Runtime and associate it with a pod using
- Implement pod to pod encryption by use of mTLS
- Practice manage TLS certificates in a Cluster
- Service Mesh Istio can be used to establish MTLS for Intra pod communication.
- Istio automatically configures workload sidecars to use mutual TLS when calling other workloads. By default, Istio configures the destination workloads using
PERMISSIVEmode. WhenPERMISSIVEmode is enabled, a service can accept both plain text and mutual TLS traffic. In order to only allow mutual TLS traffic, the configuration needs to be changed toSTRICTmode. - Exam tip: No questions related to mTLS appeared in the exam
Supply Chain Security – 20%
- Practice CKS Exercises – Supply Chain Security
- Minimize base image footprint
- Remove unnecessary tools. Remove shells, package manager & vi tools.
- Use slim/minimal images with required packages only. Do not include unnecessary software like build tools and utilities, troubleshooting, and debug binaries.
- Build the smallest image possible – To reduce the size of the image, install only what is strictly needed
- Use distroless, Alpine, or relevant base images for the app.
- Use official images from verified sources only.
-
Secure your supply chain: whitelist allowed registries, sign and validate images
- Work with images securely using a private repository
- Consider before using public images as you cannot control what’s inside them
- Configure the Kubernetes cluster to pull the images from a private registry instead of an external registry.
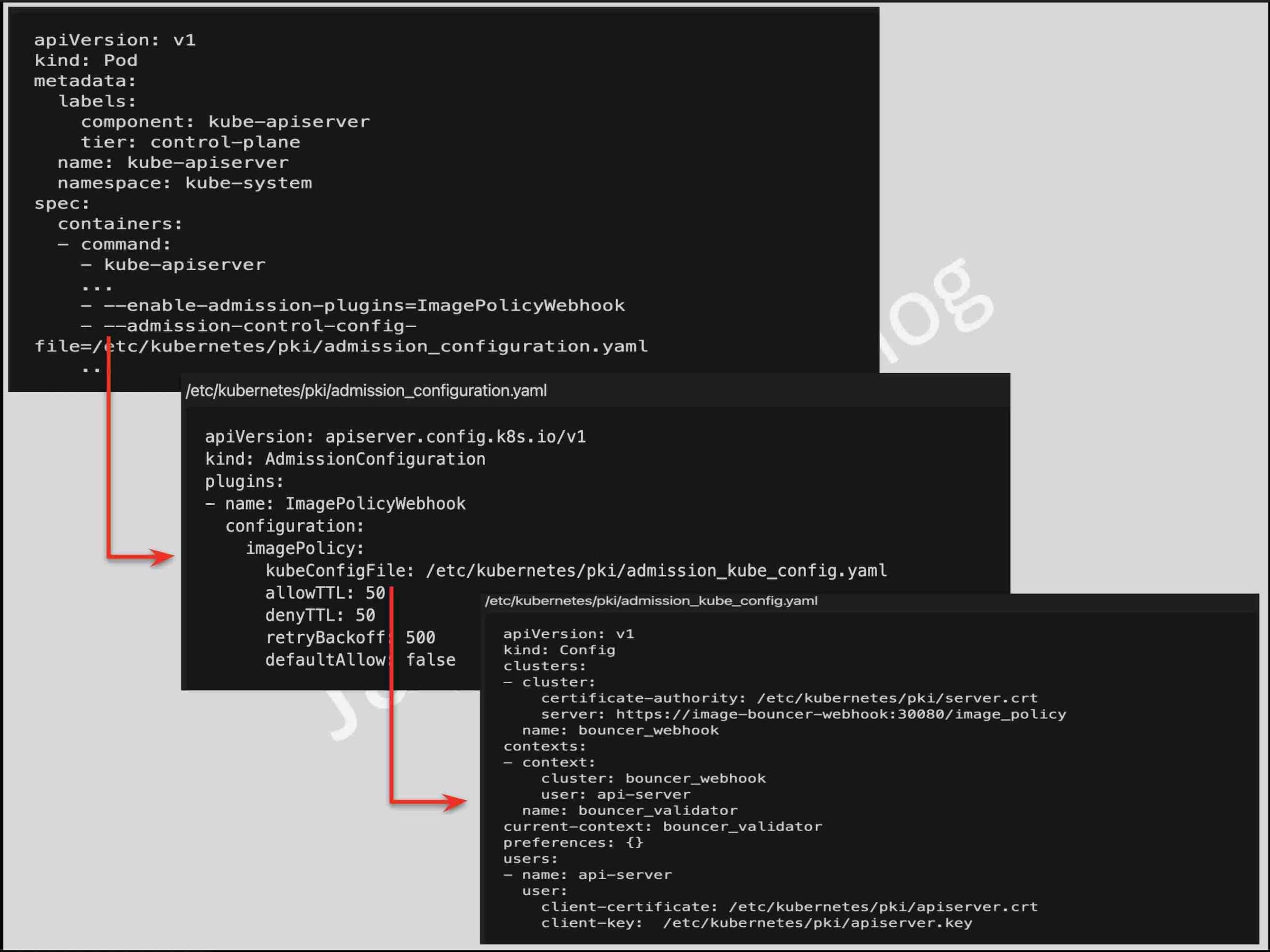
- Using ImagePolicyWebhook admission Controller to whitelist allowed image registries to sign and validate images.
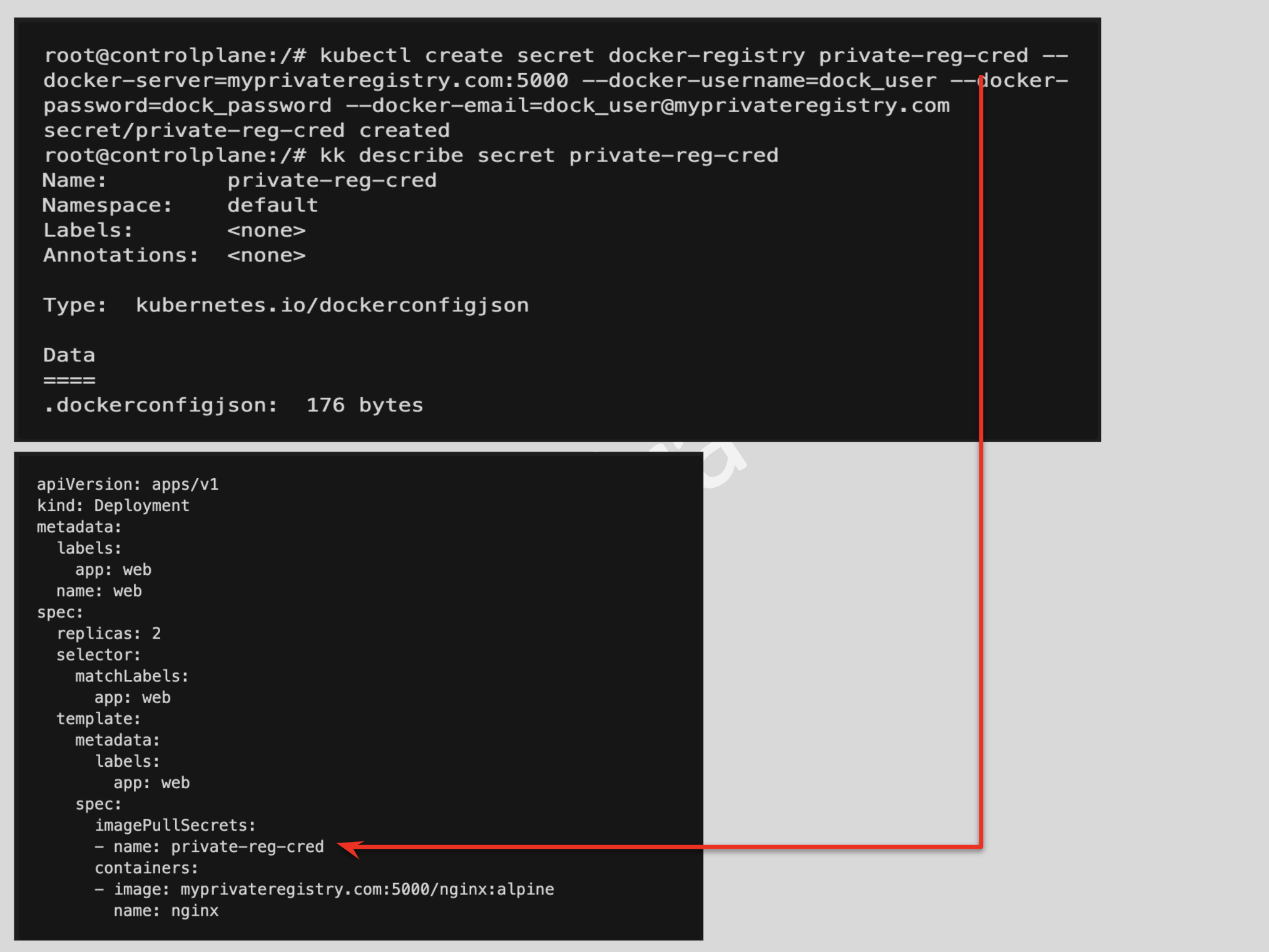
- Task @ Pulling Image from Private Registry
- Use static analysis of user workloads (e.g.Kubernetes resources, Docker files)
- Tools like Kubesec can be used to perform a static security risk analysis of the configurations files.
- Scan images for known vulnerabilities
- Aqua Security Trivy & Anchore can be used for scanning vulnerabilities in the container images.
- Exam Tip: Know how to use the Trivy tool to scan images for vulnerabilities. Also, remember to use the
--severityfor e.g.--severity=CRITICALflag for filtering a specific category.
Monitoring, Logging and Runtime Security – 20%
- Practice CKS Exercises – Monitoring, Logging, and Runtime Security
- Perform behavioral analytics of syscall process and file activities at the host and container level to detect malicious activities
- Detect threats within a physical infrastructure, apps, networks, data, users, and workloads
- Detect all phases of attack regardless of where it occurs and how it spreads
- Perform deep analytical investigation and identification of bad actors within the environment
- Tools like
straceand Aqua SecurityTraceecan be used to check the syscalls. However, with a number of processes, it would be tough to track and monitor all and they do not provide alerting. - Tools like Falco & Sysdig provide deep, process-level visibility into dynamic, distributed production environments and can be used to define rules to track, monitor, and alert on activities when a certain rule is violated.
- Exam Tip: Know how to use Falco, define new rules, enable logging. Make use of the falco_rules.local.yaml file for overrides. (I did not get questions for Falco in my exam).
- Tools like
- Ensure immutability of containers at runtime
- Immutability prevents any changes from being made to the container or to the underlying host through the container.
- It is recommended to create new images and perform a rolling deployment instead of modifying the existing running containers.
- Launch the container in read-only mode using the
--read-onlyflag from thedocker runor by using thereadOnlyRootFilesystemoption in Kubernetes. - PodSecurityContext and PodSecurityPolicy can be used to define and enforce container immutability
ReadOnlyRootFilesystem– Requires that containers must run with a read-only root filesystem (i.e. no writable layer).Privileged– determines if any container in a pod can enable privileged mode. This allows the container nearly all the same access as processes running on the host.
- Task @ Configure Pod Container Security Context
- Exam Tip: Know how to define a PodSecurityPolicy to enforce rules. Remember, Cluster Roles and Role Binding needs to be configured to provide access to the PSP to make it work.
- Use Audit Logs to monitor access
- Kubernetes auditing is handled by the
kube-apiserverwhich requires defining an audit policy file. - Auditing captures the stages as RequestReceived -> (Authn and Authz) -> ResponseStarted (-w) -> ResponseComplete (for success) OR Panic (for failures)
- Exam Tip: Know how to configure audit policies and enable audit on the
kube-apiserver. Make sure thekube-apiserveris up and running. - Task @ Kubernetes Auditing
- Kubernetes auditing is handled by the
CKS Articles
- Securing a Cluster
- 11 ways not to get hacked
- GKE Best Practices for Building Containers
- Security Best Practices (A bit older but still parts are relevant)
CKS General information and practices
- The exam can be taken online from anywhere.
- Make sure you have prepared your workspace well before the exams.
- Make sure you have a valid government-issued ID card as it would be checked.
- You are not allowed to have anything around you and no one should enter the room.
- The exam proctor will be watching you always, so refrain from doing any other activities. Your screen is also always shared.
- Copy + Paste works fine.
- You will have an online notepad on the right corner to note down. I hardly used it, but it can be useful to type and modify text instead of using VI editor.
All the Best …

Good post! Can you clarify the sentence:
> With CKS is important to move the master node for any changes to the cluster kube-apiserver
Hi martijn, for any changes that require you to check the master setting like apiserver or controller or scheduler, make sure you perform these changes by SSHing to the master node. Added the missing article to the sentence.
Thank you for detailed information! 🙂