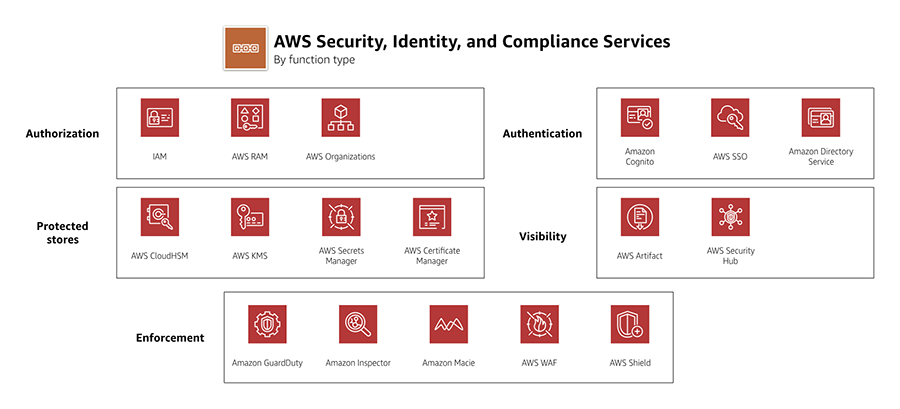
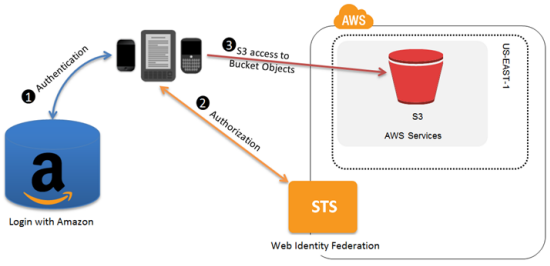
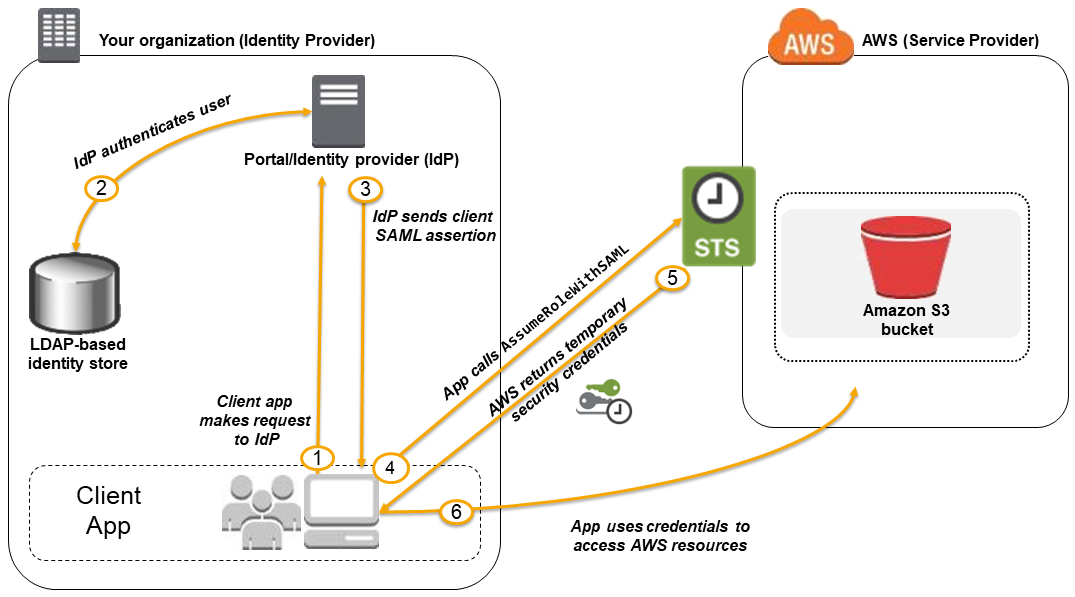
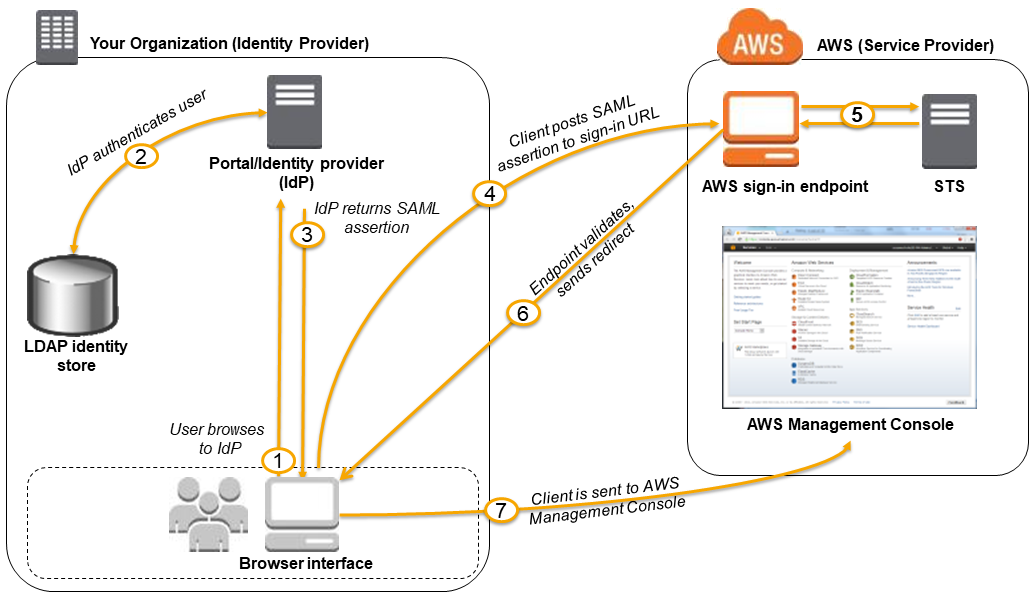
AWS IAM Best Practices
AWS recommends the following AWS Identity and Access Management service – IAM Best Practices to secure AWS resources
Root Account – Don’t use & Lock away access keys
- Do not use the AWS Root account which has full access to all the AWS resources and services including the Billing information.
- Permissions associated with the AWS Root account cannot be restricted.
- Do not generate the access keys, if not required
- If already generated and not needed, delete the access keys.
- If access keys are needed, rotate (change) the access key regularly
- Never share the Root account credentials or access keys, instead create IAM users or Roles to grant granular access
- Enable AWS multifactor authentication (MFA) on the AWS account
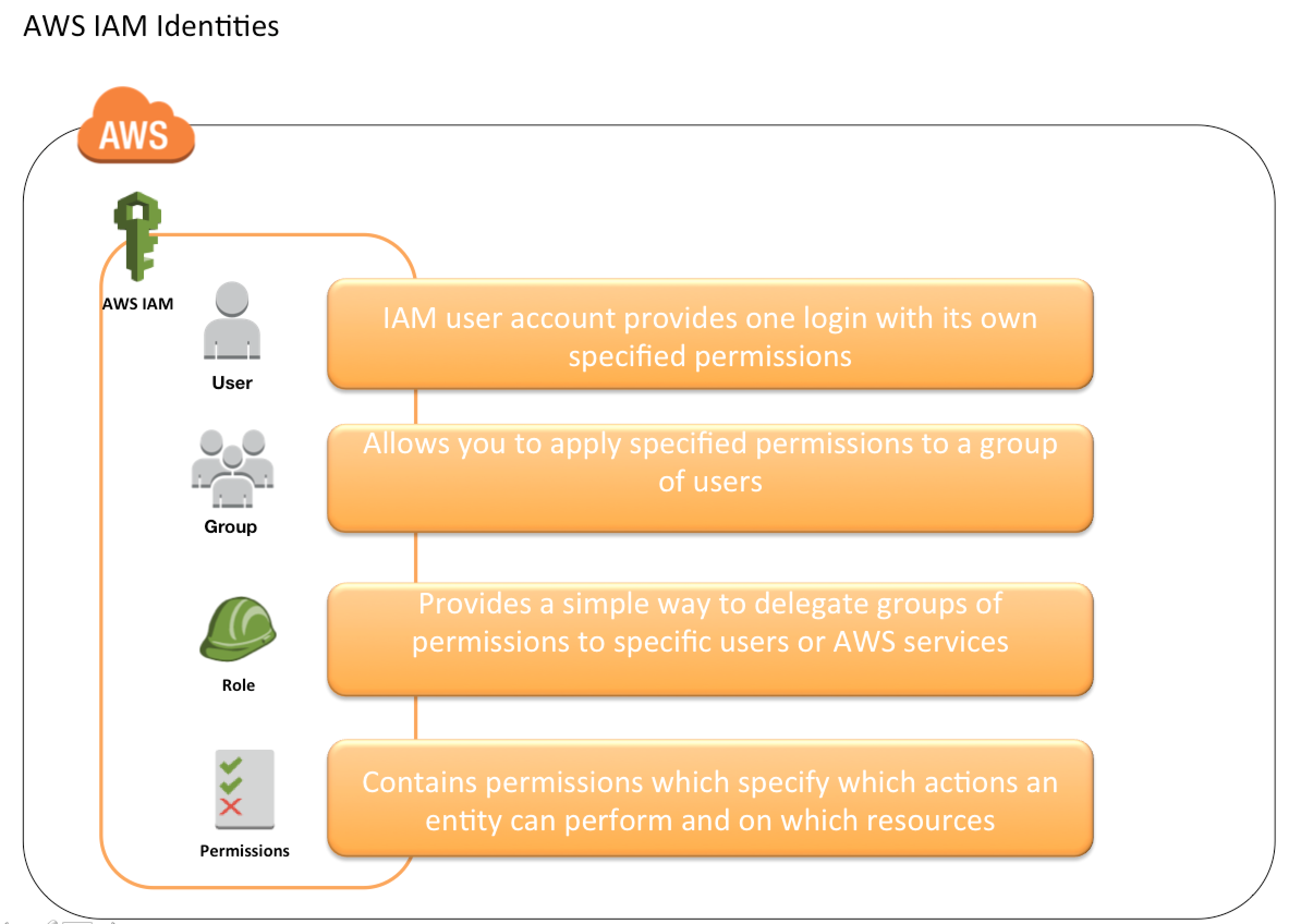
User – Create individual IAM users
- Don’t use the AWS root account credentials to access AWS, and don’t share the credentials with anyone else.
- Start by creating an IAM User with an Administrator role that has access to all resources as the Root except the account’s security credentials.
- Create individual users for anyone who needs access to your AWS account and gives each user unique credentials and grant different permissions.
Groups – Use groups to assign permissions to IAM users
- Instead of defining permissions for individual IAM users, create groups and define the relevant permissions for each group as per the job function, and then associate IAM users to those groups.
- Users in an IAM group inherit the permissions assigned to the group and a User can belong to multiple groups
- It is much easier to add new users, remove users and modify the permissions of a group of users.
Permission – Grant least privilege
- IAM user, by default, is created with no permissions
- Users should be granted LEAST PRIVILEGE as required to perform a task.
- Starting with minimal permissions and adding to the permissions as required to perform the job function is far better than granting all access and trying to then tighten it down.
Passwords – Enforce strong password policy for users
- Enforce users to create strong passwords and enforce them to rotate their passwords periodically.
- Enable a strong password policy to define password requirements forcing users to create passwords with requirements like at least one capital letter, one number, and how frequently it should be rotated.
MFA – Enable MFA for privileged users
- For extra security, Enable MultiFactor Authentication (MFA) for privileged IAM users, who are allowed access to sensitive resources or APIs.
Role – Use temporary credentials with IAM roles
- Use roles for workloads instead of creating IAM user and hardcoding the credentials which can compromise the access and are also hard to rotate.
- Roles have specific permissions and do not have a permanent set of credentials.
- Roles provide a way to access AWS by relying on dynamically generated & automatically rotated temporary security credentials.
- Roles associated with it but dynamically provide temporary credentials that are automatically rotated
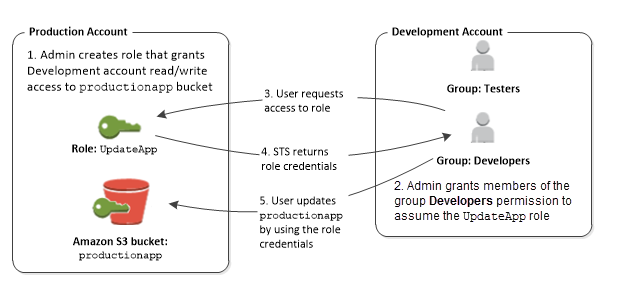
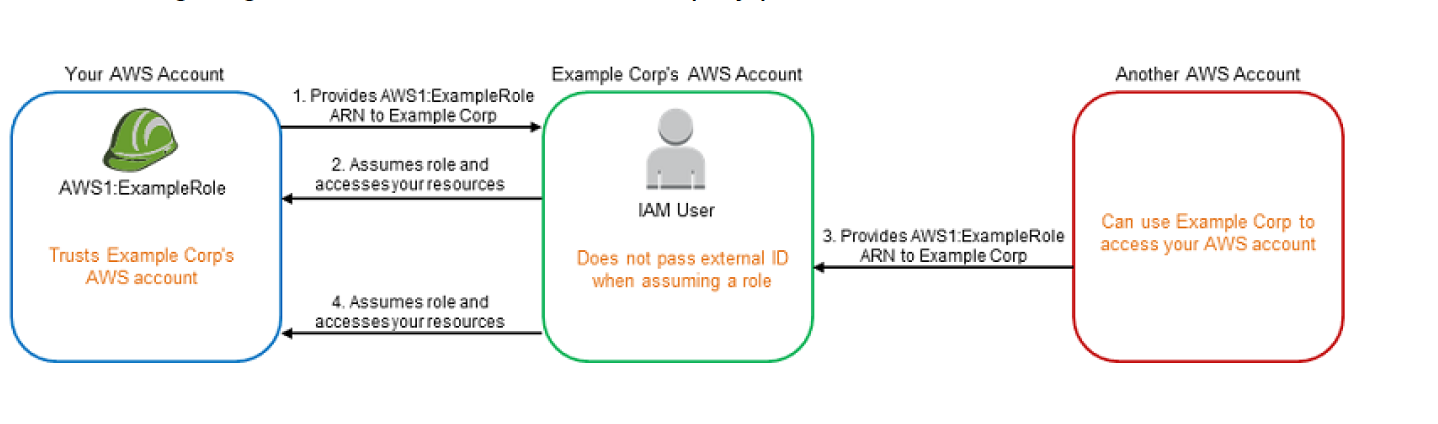
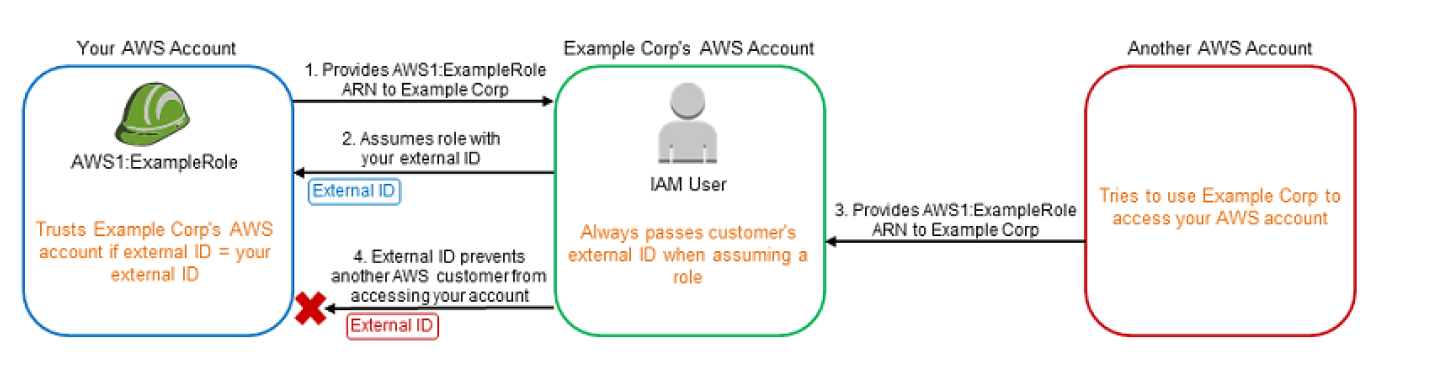
Sharing – Delegate using roles
- Allow users from same AWS account, another AWS account, or externally authenticated users (either through any corporate authentication service or through Google, Facebook etc) to use IAM roles to specify the permissions which can then be assumed by them
- A role can be defined that specifies what permissions the IAM users in the other account are allowed, and from which AWS accounts the IAM users are allowed to assume the role
Rotation – Rotate credentials regularly
- Change your own passwords and access keys regularly and enforce it through a strong password policy. So even if a password or access key is compromised without your knowledge, you limit how long the credentials can be used to access your resources
- Access keys allows creation of 2 active keys at the same time for an user. These can be used to rotate the keys.
Track & Review – Remove unnecessary credentials
- Remove IAM user and credentials (that is, passwords and access keys) that are not needed.
- Use the IAM Credential report that lists all IAM users in the account and the status of their various credentials, including passwords, access keys, and MFA devices and usage patterns to figure out what can be removed
- Passwords and access keys that have not been used recently might be good candidates for removal.
Conditions – Use policy conditions for extra security
- Define conditions under which IAM policies allow access to a resource.
- Conditions would help provide finer access control to the AWS services and resources for e.g. access limited to a specific IP range or allowing only encrypted requests for uploads to S3 buckets etc.
Auditing – Monitor activity in the AWS account
- Enable logging features provided through CloudTrail, S3, CloudFront in AWS to determine the actions users have taken in the account and the resources that were used.
- Log files show the time and date of actions, the source IP for an action, which actions failed due to inadequate permissions, and more.
Use IAM Access Analyzer
- IAM Access Analyzer analyzes the services and actions that the IAM roles use, and then generates a least-privilege policy that you can use.
- Access Analyzer helps preview and analyze public and cross-account access for supported resource types by reviewing the generated findings.
- IAM Access Analyzer helps to validate the policies created to ensure that they adhere to the IAM policy language (JSON) and IAM best practices.
Use Permissions Boundaries
- Use IAM Permissions Boundaries to delegate permissions management within an account
- IAM permissions boundaries help set the maximum permissions that you delegate and that an identity-based policy can grant to an IAM role.
- A permissions boundary does not grant permissions on its own.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Your organization is preparing for a security assessment of your use of AWS. In preparation for this assessment, which two IAM best practices should you consider implementing? Choose 2 answers
- Create individual IAM users for everyone in your organization (May not be needed as can use Roles as well)
- Configure MFA on the root account and for privileged IAM users
- Assign IAM users and groups configured with policies granting least privilege access
- Ensure all users have been assigned and are frequently rotating a password, access ID/secret key, and X.509 certificate (Must be assigned only if using console or through command line)
- What are the recommended best practices for IAM? (Choose 3 answers)
- Grant least privilege
- User the AWS account(root) for regular user
- Use Mutli-Factor Authentication (MFA)
- Store access key/private key in git
- Rotate credentials regularly
- Which of the below mentioned options is not a best practice to securely manage the AWS access credentials?
- Enable MFA for privileged users
- Create individual IAM users
- Keep rotating your secure access credentials at regular intervals
- Create strong access key and secret access key and attach to the root account
- Your CTO is very worried about the security of your AWS account. How best can you prevent hackers from completely hijacking your account?
- Use short but complex password on the root account and any administrators.
- Use AWS IAM Geo-Lock and disallow anyone from logging in except for in your city.
- Use MFA on all users and accounts, especially on the root account. (For increased security, it is recommend to configure MFA to help protect AWS resources)
- Don’t write down or remember the root account password after creating the AWS account.
- Fill the blanks: ____ helps us track AWS API calls and transitions, ____ helps to understand what resources we have now, and ____ allows auditing credentials and logins.
- AWS Config, CloudTrail, IAM Credential Reports
- CloudTrail, IAM Credential Reports, AWS Config
- CloudTrail, AWS Config, IAM Credential Reports
- AWS Config, IAM Credential Reports, CloudTrail