Google Cloud Resource Manager
Google Cloud Platform – Resource manager help manage resource containers such as organizations, folders, and projects that allow you to group and hierarchically organize other GCP resources
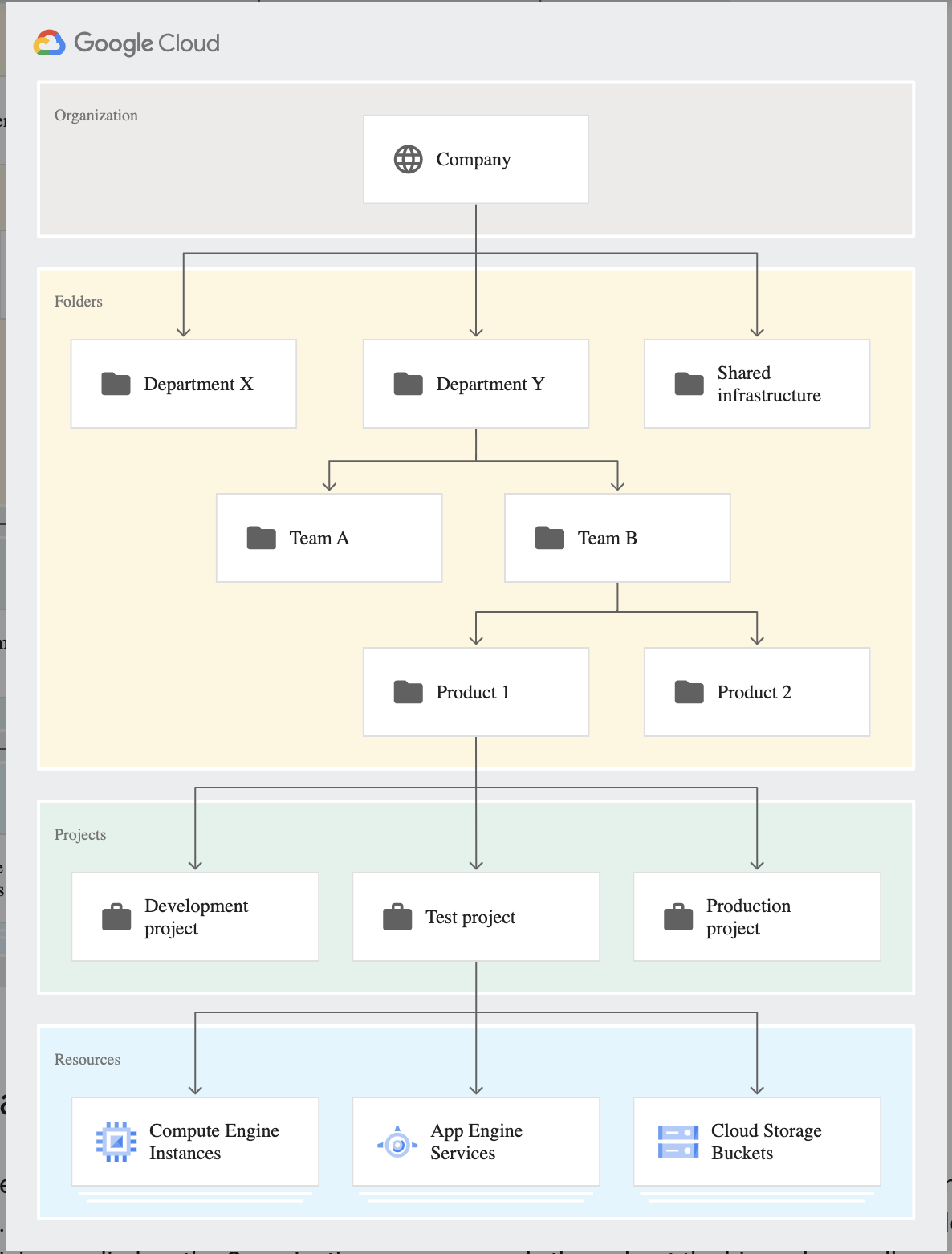
Resource Hierarchy
Organizations
- Organization resource is the root node in the Google Cloud resource hierarchy and is the hierarchical supernode and ancestor of project resources and folders.
- Organization is at the top of the hierarchy and does not have a parent.
- Organization provides central visibility and control over every resource that belongs to an organization
- With an Organization resource, projects belong to the organization instead of the employee who created the project, which means that the projects are no longer deleted when an employee leaves the company; instead, they will follow the organization’s lifecycle on Google Cloud.
- Organization administrators have central control of all resources and can view and manage all of the company’s projects
- IAM access control policies applied to the Organization resource apply throughout the hierarchy on all resources in the organization.
- Roles granted at the organization level are inherited by all projects and folders under the Organization resource
- Organization is not applicable for personal (e.g. Gmail) accounts
- Google Workspace or Cloud Identity account represents a company and is a prerequisite to having access to the Organization resource. It provides identity management, recovery mechanism, ownership, and lifecycle management
- Google Workspace super admin is the individual responsible for domain ownership verification and the contact in cases of recovery.
Folders
- Folders are an additional optional grouping mechanism on top of projects and provide isolation boundaries between projects
- Organization resource is a prerequisite to use folders.
- Folders can be used to model different legal entities, departments, teams, and environments within a company
- Folders allow delegation of administration rights as well as control or limit access to resources within the folder
Projects
- Project resource is the base-level organizing entity
- Organizations and folders may contain multiple projects
- Projects are a core organizational component of GCP
- A project is required to use Google Cloud and forms the basis for creating, enabling, and using all Google Cloud services, managing APIs, enabling billing, adding and removing collaborators, and managing permissions.
- Each project has a name and a unique project ID across Google Cloud
- Project ID cannot be reused even if the project is deleted
- Each project is associated with a billing account.
- Multiple projects can have their usage billed to the same billing account
IAM Policy Inheritance
- Identity and Access Management helps control who (users) has what access (roles) to which resources by setting IAM policies on the resources.
- Resources inherit the policies of the parent node i.e. policy set at the Organization level is inherited by all its child folders and projects, and if a policy set at the project level, it is inherited by all its child resources.
- Most permissive parent policy always overrules more restrictive child policy i.e. There is no way to explicitly remove permission for a lower-level resource that is granted at a higher level in the resource hierarchy.
- The effective policy for a resource is the union of the policy set on the resource and the policy inherited from its ancestors.
- Permission inheritance is transitive i.e. resources inherit policies from the project, which inherit policies from the organization.
- IAM policy hierarchy follows the same path as the Google Cloud resource hierarchy i.e. if the resource hierarchy is changed for e.g. moving a project from one folder to the other, the policy hierarchy changes as well.
Organization Policy Service
- Organization Policy Service gives centralized and programmatic control over the organization’s cloud resources
- Organization Policy Service benefits
- Centralize control to configure restrictions on how the organization’s resources can be used.
- Define and establish guardrails for the development teams to stay within compliance boundaries.
- Help project owners and their teams move quickly without the worry of breaking compliance.
- Organization policy is set on a resource hierarchy node, all descendants of that node inherit the organization policy by default. i.e. organization policy set at the root organization node will pass down the defined restriction through all descendant folders, projects, and service resources.
Restricting Identities by Domain
- Resource Manager provides a domain restriction constraint that can be used in organization policies to limit resource sharing based on domain.
- This constraint allows restricting the set of identities allowed to be used in Identity and Access Management policies
- Organization policies can use this constraint to limit resource sharing to a specified set of one or more Google Workspace domains, and exceptions can be granted on a per-folder or per-project basis.
- Domain restriction constraint is not retroactive. Once a domain restriction is set, this limitation will apply to IAM policy changes made from that point forward, and not to any previous changes.
GCP Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- GCP services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- GCP exam questions are not updated to keep up the pace with GCP updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Google Cloud Platform resources are managed hierarchically using organization, folders, and projects. When Cloud Identity and Access Management (IAM) policies exist at these different levels, what is the
effective policy at a particular node of the hierarchy?- The effective policy is determined only by the policy set at the node
- The effective policy is the union of the policy set at the node and policies inherited from its ancestors
- The effective policy is the policy set at the node and restricted by the policies of its ancestors
- The effective policy is the intersection of the policy set at the node and policies inherited from its ancestors
- An Organization has setup an IAM policy at the organization level, the folder level, the project level, and on the resource level. They want to understand what policy takes effect on the entity. What would be the
correct option?- Effective policy for a resource is the Intersection of the policy set on the resource and the policy inherited from its ancestors
- Effective policy for a resource is the policy inherited from its ancestors overriding the policy defined on the resource
- Effective policy for a resource is the union of the policy set on the resource and the policy inherited from its ancestors
- Effective policy for a resource is the policy defined overriding the policy inherited from its ancestors
- Several employees at your company have been creating projects with Cloud Platform and paying for it with their personal credit
cards, which the company reimburses. The company wants to centralize all these projects under a single, new billing account.
What should you do?- Contact cloud-billing@google.com with your bank account details and request a corporate billing account for your company.
- Create a ticket with Google Support and wait for their call to share your credit card details over the phone.
- In the Google Platform Console, go to the Resource Manager and move all projects to the root Organization.
- In the Google Cloud Platform Console, create a new billing account and set up a payment method.