Google Cloud Identity Aware-Proxy – IAP
- Identity-Aware Proxy IAP allows managing access to HTTP-based apps both on Google Cloud and outside of Google Cloud.
- Identity-Aware Proxy IAP intercepts the web requests sent to the application, authenticates the user making the request using the Google Identity Service, and only lets the requests through if they come from an authorized user. In addition, it can modify the request headers to include information about the authenticated user.
- Identity-Aware Proxy IAP helps establish a central authorization layer for applications accessed by HTTPS to use an application-level access control model instead of relying on network-level firewalls.
- Access policies can be defined centrally and applied to all of the applications and resources.
- IAP policies scale across the organization.
- IAP uses Google identities and IAM, by default but by leveraging Identity Platform a wide range of external identity providers can be used, such as:
- Email/password
- OAuth (Google, Facebook, Twitter, GitHub, Microsoft, etc.)
- SAML
- OIDC
- Phone number
- Custom
- Anonymous
How IAP Works
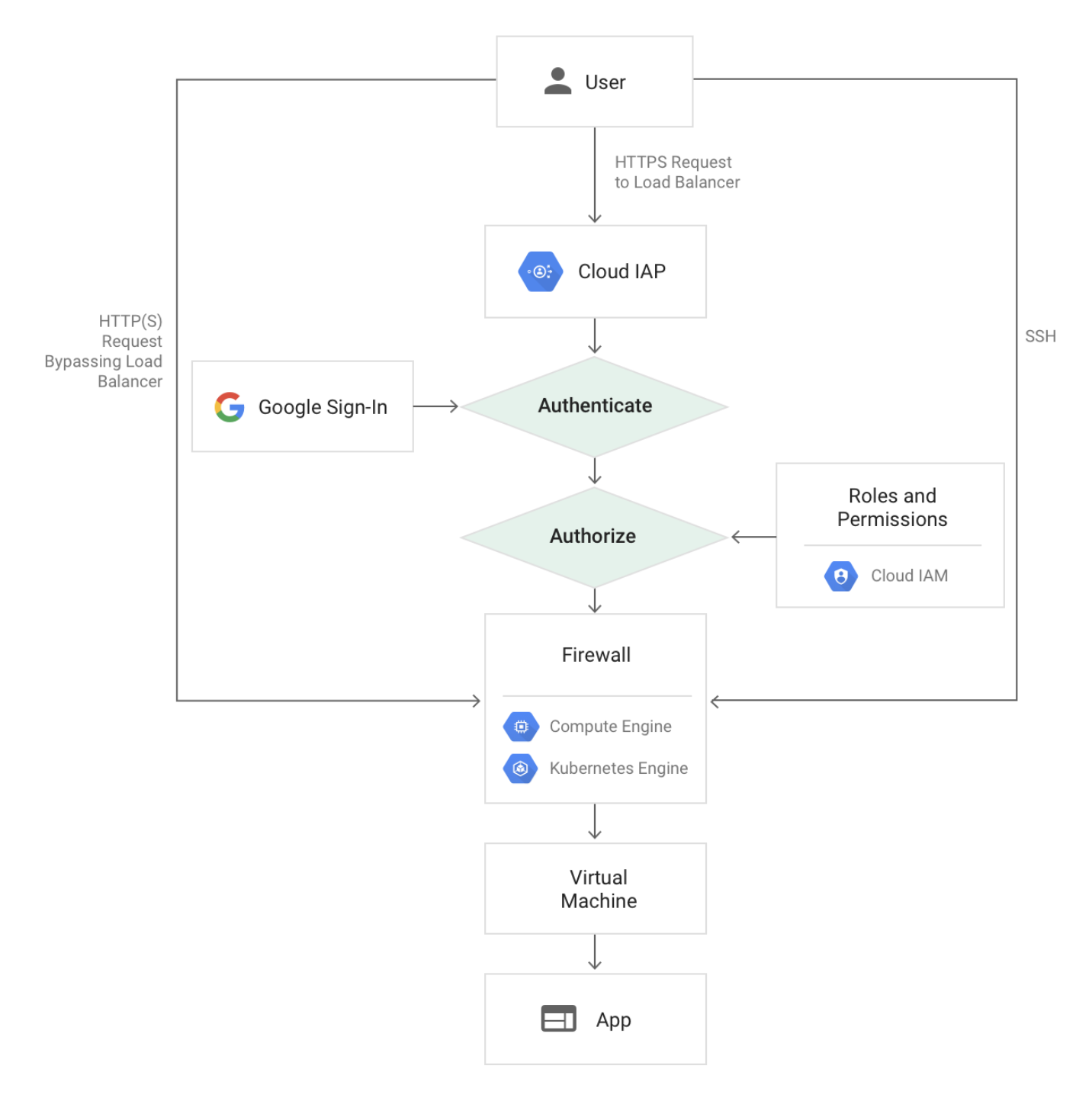
- Only users with the correct IAM role can access application or resource protected by IAP
- Users are subject to the fine-grained access controls implemented by the product in use without requiring a VPN.
- When a user tries to access an IAP-secured resource, IAP performs authentication and authorization checks.
- Authentication
- Requests to the Google Cloud resources come through App Engine, Cloud Load Balancing (HTTPS), or internal HTTP load balancing.
- If IAP is enabled, information about the protected resource is sent to the IAP authentication server which includes information like the project number, the request URL, and any IAP credentials in the request headers or cookies.
- For authentication, the user is directed to an OAuth 2.0 Google Account sign-in flow that stores a token in a browser cookie for future sign-ins.
- If the request credentials are valid, the authentication server uses those credentials to get the user’s identity (email address and user ID).
- The authentication server then uses the identity to check the user’s IAM role and check if the user is authorized to access the resource.
- Authorization
- After authentication, IAP applies the relevant IAM policy to check if the user is authorized to access the requested resource.
- User with IAP-secured Web App User role on the Cloud Console project where the resource exists is authorized to access the application
- When you turn on IAP for a resource, it automatically creates an OAuth 2.0 client ID and secret.
- For on-premises apps, the requests are routed through the IAP connector which forwards the request through a site-to-site connection established with Cloud Interconnect from Google Cloud to the on-premises network.
- Identity-Aware Proxy (IAP) can be configured to use JSON Web Tokens (JWT) to make sure that a request to the app is authorized
- Be default, only headers
x-goog-authenticated-user-{email,id}are passed and can be easily forged and bypass IAP
- It protects App from
- IAP is accidentally disabled;
- Misconfigured firewalls;
- Access from within the project.
- IAP JWT provides a more secure alternative by verifying the header, payload, and signature of the JWT, which is in the HTTP request header
x-goog-iap-jwt-assertion
- Signed headers provide secondary security in case someone bypasses IAP.
IAP Best Practices
- Don’t use a third-party CDN in front of the application. CDNs may cache content and serve cached pages to unauthenticated users.
- Make sure all requests to Compute Engine or GKE are routed through the load balancer:
- Use signed headers for App Engine flexible environment, App Engine standard environment, Compute Engine, and GKE applications.
GCP Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- GCP services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- GCP exam questions are not updated to keep up the pace with GCP updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
Reference
Google_Cloud_Identity-Aware_Proxy
