Table of Contents
hide
AWS VPC – Virtual Private Cloud
- AWS VPC – Virtual Private Cloud is a virtual network dedicated to the AWS account. It is logically isolated from other virtual networks in the AWS cloud.
- VPC allows the users complete control over their virtual networking environment, including the selection of their own IP address range, creation of subnets, and configuration of route tables and network gateways.
- VPC allows you to use both IPv4 and IPv6 in your VPC for secure and easy access to resources and applications.
- VPC is a regional service and it spans all of the AZs in the Region. Availability zones (AZ) are multiple, isolated locations within each Region.
- VPC Sizing
- VPC needs a set of IP addresses in the form of a Classless Inter-Domain Routing (CIDR) block for e.g, 10.0.0.0/16, which allows 2^16 (65536) IP address to be available
- Allowed CIDR block size is between
- /28 netmask (minimum with 2^4 – 16 available IP address) and
- /16 netmask (maximum with 2^16 – 65536 IP address)
- CIDR block from private (non-publicly routable) IP address can be assigned
- 10.0.0.0 – 10.255.255.255 (10/8 prefix)
- 172.16.0.0 – 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 – 192.168.255.255 (192.168/16 prefix)
- It’s possible to specify a range of publicly routable IP addresses; however, direct access to the Internet is not currently supported from publicly routable CIDR blocks in a VPC
CIDR block once assigned to the VPC cannot be modified.NOTE – You can now resize VPC. Read AWS blog post.- Each VPC is separate from any other VPC created with the same CIDR block even if it resides within the same AWS account
- Connection between your VPC and corporate or home network can be established, however, the CIDR blocks should be not be overlapping for e.g. VPC with CIDR 10.0.0.0/16 can communicate with 10.1.0.0/16 corporate network but the connections would be dropped if it tries to connect to 10.0.37.0/16 corporate network cause of overlapping IP addresses.
- VPC allows you to set tenancy options for the Instances launched in it. By default, the tenancy option is shared. If the dedicated option is selected, all the instances within it are launched on dedicated hardware overriding the individual instance tenancy setting.
- Deletion of the VPC is possible only after terminating all instances within the VPC and deleting all the components with the VPC e.g. subnets, security groups, network ACLs, route tables, Internet gateways, VPC peering connections, and DHCP options
- VPC Peering provides a networking connection between two VPCs (same or different account and region) that enables routing of traffic between them using private IPv4 addresses or IPv6 addresses.
- NAT Gateway enables instances in a private subnet to connect to the Internet but prevents the Internet from initiating connections with the instances.
- VPC endpoints enable the creation of a private connection between VPC to supported AWS services and VPC endpoint services powered by PrivateLink using its private IP address.
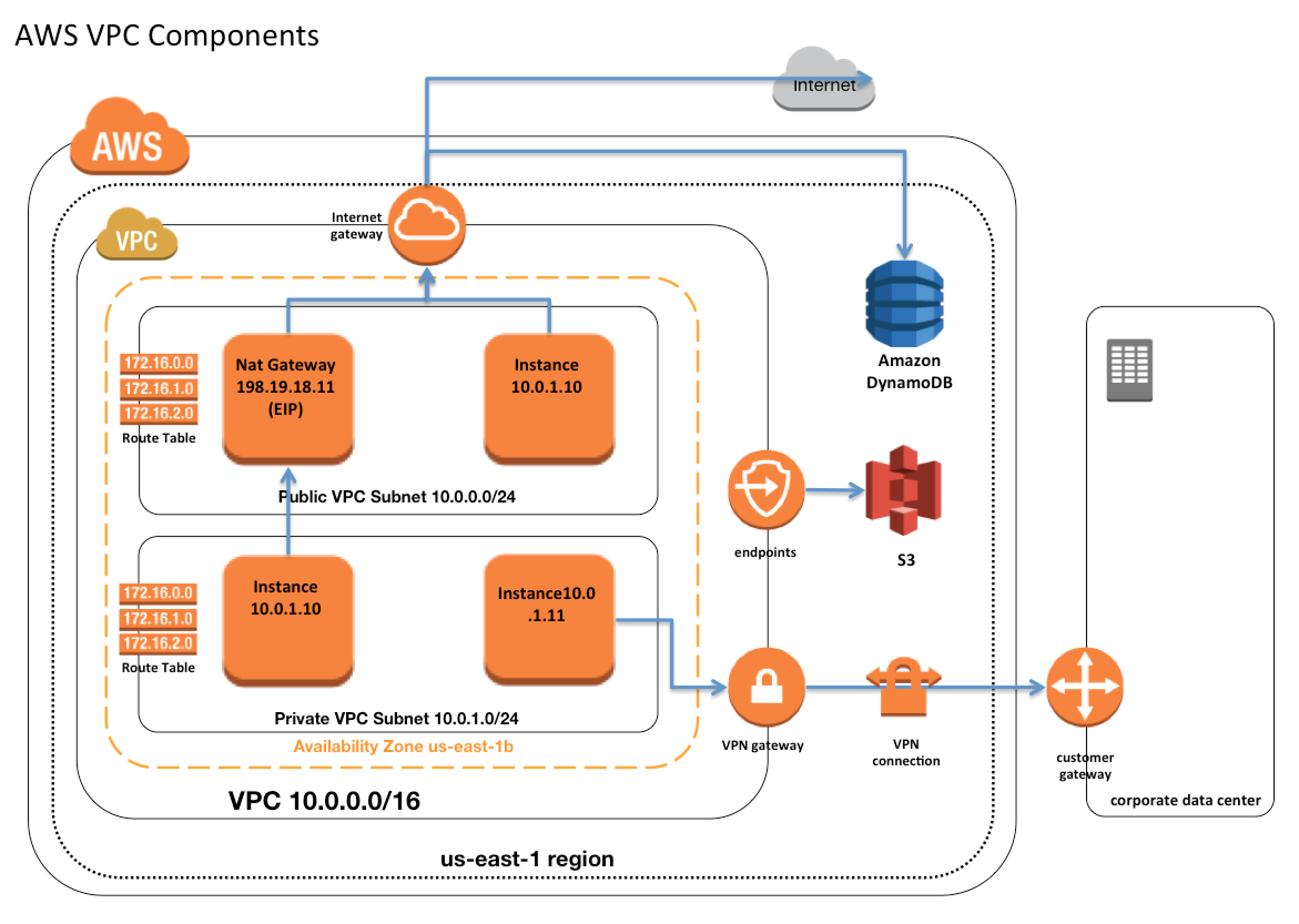
Subnets
- Subnet spans a single Availability Zone, distinct locations engineered to be isolated from failures in other AZs, and cannot span across AZs
- Subnet can be configured with an Internet gateway to enable communication over the Internet, or virtual private gateway (VPN) connection to enable communication with your corporate network
- Subnet can be Public or Private and it depends on whether it has Internet connectivity i.e. is able to route traffic to the Internet through the IGW
- Instances within the Public Subnet should be assigned a Public IP or Elastic IP address to be able to communicate with the Internet
- For Subnets not connected to the Internet, but has traffic routed through Virtual Private Gateway only is termed as VPN-only subnet
- Subnets can be configured to Enable assignment of the Public IP address to all the Instances launched within the Subnet by default, which can be overridden during the creation of the Instance
- Subnet Sizing
- CIDR block assigned to the Subnet can be the same as the VPC CIDR, in this case you can launch only one subnet within your VPC
- CIDR block assigned to the Subnet can be a subset of the VPC CIDR, which allows you to launch multiple subnets within the VPC
- CIDR block assigned to the subnet should not be overlapping
- CIDR block size allowed is between
- /28 netmask (minimum with 2^4 – 16 available IP address) and
- /16 netmask (maximum with 2^16 – 65536 IP address)
- AWS reserves 5 IPs address (first 4 and last 1 IP address) in each Subnet which are not available for use and cannot be assigned to an instance. for e.g. for a Subnet with a CIDR block 10.0.0.0/24 the following five IPs are reserved
- 10.0.0.0: Network address
- 10.0.0.1: Reserved by AWS for the VPC router
- 10.0.0.2: Reserved by AWS for mapping to Amazon-provided DNS
- 10.0.0.3: Reserved by AWS for future use
- 10.0.0.255: Network broadcast address. AWS does not support broadcast in a VPC, therefore the address is reserved.
- Subnet Routing
- Each Subnet is associated with a route table that controls the traffic.
- Subnet Security
- Subnet security can be configured using Security groups and NACLs
- Security groups work at the instance level, and NACLs work at the subnet level
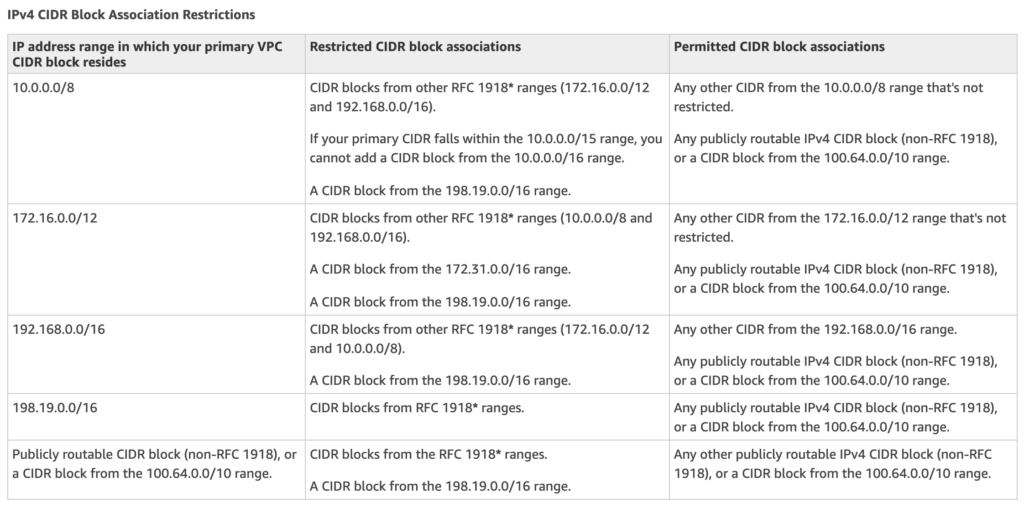
VPC & Subnet Sizing
- VPC supports IPv4 and IPv6 addressing and has different CIDR block size limits for each
- IPv6 CIDR block can be optionally associated with the VPC
- VPC IPv4 CIDR block cannot be modified once created i.e. cannot increase or decrease the size of an existing CIDR block.
- However, secondary CIDR blocks can be associated with the VPC to extend the VPC
- Limitations
- allowed block size is between a
/28netmask and/16netmask. - CIDR block must not overlap with any existing CIDR block that’s associated with the VPC.
- CIDR block must not be the same or larger than the CIDR range of a route in any of the VPC route tables for e.g. for a CIDR block 10.0.0.0/24, can only associate smaller CIDR blocks like 10.0.0.0/25
- allowed block size is between a
IP Addresses
Instances launched in the VPC can have Private, Public, and Elastic IP addresses assigned to them and are properties of ENI (Network Interfaces)
- Private IP Addresses
- Private IP addresses are not reachable over the Internet, and can be used for communication only between the instances within the VPC
- All instances are assigned a private IP address, within the IP address range of the subnet, to the default network interface
- Primary IP address is associated with the network interface for its lifetime, even when the instance is stopped and restarted and is released only when the instance is terminated
- Additional Private IP addresses, known as secondary private IP address, can be assigned to the instances and these can be reassigned from one network interface to another
- Public IP address
- Public IP addresses are reachable over the Internet, and can be used for communication between instances and the Internet, or with other AWS services that have public endpoints
- Public IP address assignment to the Instance depends if the Public IP Addressing is enabled for the Subnet.
- Public IP address can also be assigned to the Instance by enabling the Public IP addressing during the creation of the instance, which overrides the subnet’s public IP addressing attribute
- Public IP address is assigned from AWS pool of IP addresses and it is not associated with the AWS account and hence is released when the instance is stopped and restarted or terminated.
- Elastic IP address
- Elastic IP addresses are static, persistent public IP addresses that can be associated and disassociated with the instance, as required
- Elastic IP address is allocated to the VPC and owned by the account unless released.
- A Network Interface can be assigned either a Public IP or an Elastic IP. If you assign an instance, that already has a Public IP, an Elastic IP, the public IP is released
- Elastic IP addresses can be moved from one instance to another, which can be within the same or different VPC within the same account
- Elastic IPs are charged for non-usage i.e. if it is not associated or associated with a stopped instance or an unattached Network Interface
Elastic Network Interface (ENI)
- Each Instance is attached to a default elastic network interface (Primary Network Interface eth0) and cannot be detached from the instance
- ENI can include the following attributes
- Primary private IP address
- One or more secondary private IP addresses
- One Elastic IP address per private IP address
- One public IP address, which can be auto-assigned to the network interface for eth0 when you launch an instance, but only when you create a network interface for eth0 instead of using an existing ENI
- One or more security groups
- A MAC address
- A source/destination check flag
- A description
- ENI’s attributes follow the ENI as it is attached or detached from an instance and reattached to another instance. When an ENI is moved from one instance to another, network traffic is redirected to the new instance.
- Multiple ENIs can be attached to an instance and is useful for use cases:
- Create a management network.
- Use network and security appliances in your VPC.
- Create dual-homed instances with workloads/roles on distinct subnets.
- Create a low-budget, high-availability solution.
Route Tables
- Route table defines rules, termed as routes, which determine where network traffic from the subnet would be routed
- Each VPC has an implicit router to route network traffic
- Each VPC has a Main Route table and can have multiple custom route tables created
- Each Subnet within a VPC must be associated with a single route table at a time, while a route table can have multiple subnets associated with it
- Subnet, if not explicitly associated to a route table, is implicitly associated with the main route table
- Every route table contains a local route that enables communication within a VPC which cannot be modified or deleted
- Route priority is decided by matching the most specific route in the route table that matches the traffic
- Route tables need to be updated to define routes for Internet gateways, Virtual Private gateways, VPC Peering, VPC Endpoints, NAT Devices, etc.
Internet Gateways – IGW
- An Internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in the VPC and the Internet.
- IGW imposes no availability risks or bandwidth constraints on the network traffic.
- An Internet gateway serves two purposes:
- To provide a target in the VPC route tables for Internet-routable traffic,
- To perform network address translation (NAT) for instances that have been NOT been assigned public IP addresses.
- Enabling Internet access to an Instance requires
- Attaching Internet gateway to the VPC
- Subnet should have route tables associated with the route pointing to the Internet gateway
- Instances should have a Public IP or Elastic IP address assigned
- Security groups and NACLs associated with the Instance should allow relevant traffic
NAT
- NAT device enables instances in a private subnet to connect to the Internet or other AWS services, but prevents the Internet from initiating connections with the instances.
- NAT devices do not support IPv6 traffic, use an egress-only Internet gateway instead.
Refer to My Blog Post about VPC NAT
Egress-only Internet gateway
- Egress-only Internet gateway works as a NAT gateway, but for IPv6 traffic
- Egress-only Internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows outbound communication over IPv6 from instances in the VPC to the Internet, and prevents the Internet from initiating an IPv6 connection with the instances.
- An egress-only Internet gateway is for use with IPv6 traffic only. To enable outbound-only Internet communication over IPv4, use a NAT gateway instead.
- VPC sharing allows multiple AWS accounts to create their application resources, such as EC2 instances, RDS databases, Redshift clusters, and AWS Lambda functions, into shared, centrally-managed VPCs.
- In this model, the account that owns the VPC (owner) shares one or more subnets with other accounts (participants) that belong to the same organization from AWS Organizations.
- After a subnet is shared, the participants can view, create, modify, and delete their application resources in the subnets shared with them. Participants cannot view, modify, or delete resources that belong to other participants or the VPC owner.
VPC Endpoints
- VPC endpoint enables the creation of a private connection between VPC to supported AWS services and VPC endpoint services powered by PrivateLink using its private IP address
- Endpoints do not require a public IP address, access over the Internet, NAT device, a VPN connection, or AWS Direct Connect.
- Traffic between VPC and AWS service does not leave the Amazon network
- Endpoints are virtual devices, that are horizontally scaled, redundant, and highly available VPC components that allow communication between instances in the VPC and AWS services without imposing availability risks or bandwidth constraints on your network traffic.
- Endpoints currently do not support cross-region requests, ensure that the endpoint is created in the same region as the S3 bucket
- AWS currently supports the following types of Endpoints
Refer to My Blog Post about VPC Endpoint
VPC Peering
- A VPC peering connection is a networking connection between two VPCs that enables the routing of traffic between them using private IPv4 addresses or IPv6 addresses.
- VPC peering connection is a one-to-one relationship between two VPCs and can be established between your own VPCs, or with a VPC in another AWS account in the same or different region.
- VPC peering helps instances in either VPC can communicate with each other as if they are within the same network using AWS’s existing infrastructure of a VPC to create a peering connection; it is neither a gateway nor a VPN connection and does not rely on a separate piece of physical hardware.
- VPC peering does not have any separate charges. However, there are data transfer charges.
Refer to My Blog Post about VPC Peering
VPC VPN Connections
Refer to My Blog Post about AWS VPC VPN Connections
VPC Security
- In a VPC, both Security Groups and Network ACLs (NACLS) together help to build a layered network defense.
- Security groups – Act as a virtual firewall for associated instances, controlling both inbound and outbound traffic at the instance level
- Network access control lists (NACLs) – Act as a firewall for associated subnets, controlling both inbound and outbound traffic at the subnet level
Security Groups & NACLs
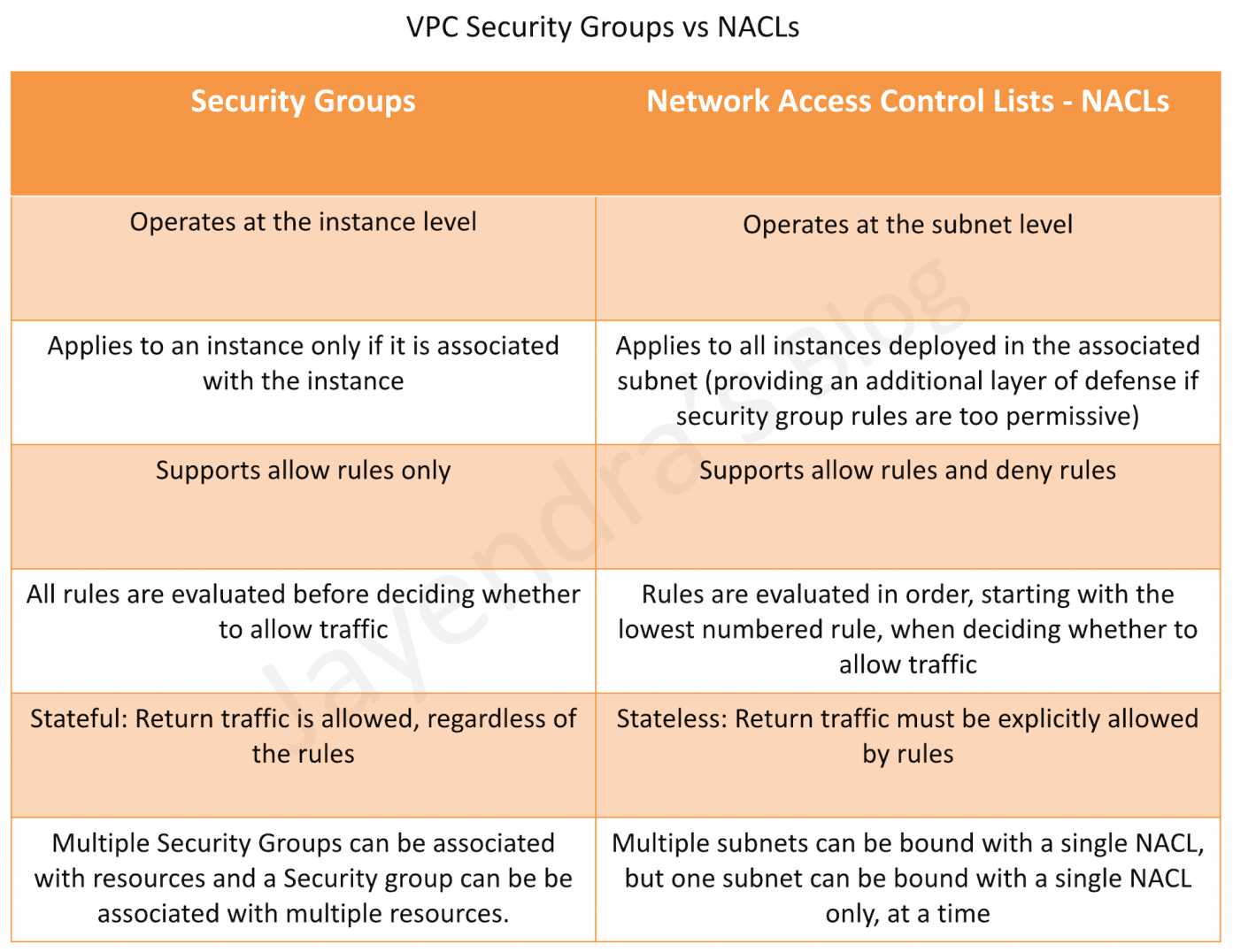
Refer to My Blog Post about AWS Security Group vs NACLs
VPC Flow logs
- VPC Flow Logs help capture information about the IP traffic going to and from network interfaces in the VPC and can help in monitoring the traffic or troubleshooting any connectivity issues.
- Flow log data can be published to CloudWatch Logs, S3, and Kinesis Data Firehose.
- Flow log can be created for the entire VPC, subnets, or each network interface. If enabled, for the entire VPC or subnet all the network interfaces within that resource are monitored.
- Flow log can be configured to capture the type of traffic (accepted traffic, rejected traffic, or all traffic).
- Flow logs do not capture real-time log streams for network interfaces.
- Flow log data is collected outside of the path of the network traffic, and therefore does not affect network throughput or latency.
- Flow logs can be created for network interfaces that are created by other AWS services; for e.g., ELB, RDS, ElastiCache, Redshift, and WorkSpaces.
- Flow logs do not capture the following traffic
- Traffic generated by instances when they contact the Amazon DNS server.
- Traffic generated by a Windows instance for Amazon Windows license activation.
- Traffic to and from 169.254.169.254 for instance metadata
- Traffic to and from 169.254.169.123 for the Amazon Time Sync Service.
- DHCP traffic.
- Mirrored traffic.
- Traffic to the reserved IP address for the default VPC router.
- Traffic between an endpoint network interface and a Network Load Balancer network interface.
- Troubleshooting traffic flow
- If ACCEPT followed by REJECT, inbound was accepted by Security Groups and ACLs. However, rejected by NACLs outbound
- If REJECT, inbound was either rejected by Security Groups OR NACLs.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- You have a business-to-business web application running in a VPC consisting of an Elastic Load Balancer (ELB), web servers, application servers and a database. Your web application should only accept traffic from predefined customer IP addresses. Which two options meet this security requirement? Choose 2 answers
- Configure web server VPC security groups to allow traffic from your customers’ IPs (Web server is behind the ELB and customer IPs will never reach web servers)
- Configure your web servers to filter traffic based on the ELB’s “X-forwarded-for” header (get the customer IPs and create a custom filter to restrict access. Refer link)
- Configure ELB security groups to allow traffic from your customers’ IPs and deny all outbound traffic (ELB will see the customer IPs so can restrict access, deny all is basically have no rules in outbound traffic, implicit, and its stateful so would work)
- Configure a VPC NACL to allow web traffic from your customers’ IPs and deny all outbound traffic (NACL is stateless, deny all will not work)
- A user has created a VPC with public and private subnets using the VPC Wizard. The VPC has CIDR 20.0.0.0/16. The private subnet uses CIDR 20.0.0.0/24. Which of the below mentioned entries are required in the main route table to allow the instances in VPC to communicate with each other?
- Destination : 20.0.0.0/24 and Target : VPC
- Destination : 20.0.0.0/16 and Target : ALL
- Destination : 20.0.0.0/0 and Target : ALL
- Destination : 20.0.0.0/16 and Target : Local
- A user has created a VPC with two subnets: one public and one private. The user is planning to run the patch update for the instances in the private subnet. How can the instances in the private subnet connect to the internet?
- Use the internet gateway with a private IP
- Allow outbound traffic in the security group for port 80 to allow internet updates
- The private subnet can never connect to the internet
- Use NAT with an elastic IP
- A user has launched an EC2 instance and installed a website with the Apache webserver. The webserver is running but the user is not able to access the website from the Internet. What can be the possible reason for this failure?
- The security group of the instance is not configured properly.
- The instance is not configured with the proper key-pairs.
- The Apache website cannot be accessed from the Internet.
- Instance is not configured with an elastic IP.
- A user has created a VPC with public and private subnets using the VPC wizard. Which of the below mentioned statements is true in this scenario?
- AWS VPC will automatically create a NAT instance with the micro size
- VPC bounds the main route table with a private subnet and a custom route table with a public subnet
- User has to manually create a NAT instance
- VPC bounds the main route table with a public subnet and a custom route table with a private subnet
- A user has created a VPC with public and private subnets. The VPC has CIDR 20.0.0.0/16. The private subnet uses CIDR 20.0.1.0/24 and the public subnet uses CIDR 20.0.0.0/24. The user is planning to host a web server in the public subnet (port 80) and a DB server in the private subnet (port 3306). The user is configuring a security group of the NAT instance. Which of the below mentioned entries is not required for the NAT security group?
- For Inbound allow Source: 20.0.1.0/24 on port 80
- For Outbound allow Destination: 0.0.0.0/0 on port 80
- For Inbound allow Source: 20.0.0.0/24 on port 80
- For Outbound allow Destination: 0.0.0.0/0 on port 443
- A user has created a VPC with CIDR 20.0.0.0/24. The user has used all the IPs of CIDR and wants to increase the size of the VPC. The user has two subnets: public (20.0.0.0/25) and private (20.0.0.128/25). How can the user change the size of the VPC?
- The user can delete all the instances of the subnet. Change the size of the subnets to 20.0.0.0/32 and 20.0.1.0/32, respectively. Then the user can increase the size of the VPC using CLI
- It is not possible to change the size of the VPC once it has been created (NOTE – You can now increase the VPC size. Read Post)
- User can add a subnet with a higher range so that it will automatically increase the size of the VPC
- User can delete the subnets first and then modify the size of the VPC
- A user has created a VPC with the public and private subnets using the VPC wizard. The VPC has CIDR 20.0.0.0/16. The public subnet uses CIDR 20.0.1.0/24. The user is planning to host a web server in the public subnet (port 80) and a DB server in the private subnet (port 3306). The user is configuring a security group for the public subnet (WebSecGrp) and the private subnet (DBSecGrp). Which of the below mentioned entries is required in the web server security group (WebSecGrp)?
- Configure Destination as DB Security group ID (DbSecGrp) for port 3306 Outbound
- Configure port 80 for Destination 0.0.0.0/0 Outbound
- Configure port 3306 for source 20.0.0.0/24 InBound
- Configure port 80 InBound for source 20.0.0.0/16
- A user has created a VPC with CIDR 20.0.0.0/16. The user has created one subnet with CIDR 20.0.0.0/16 by mistake. The user is trying to create another subnet of CIDR 20.0.0.1/24. How can the user create the second subnet?
- There is no need to update the subnet as VPC automatically adjusts the CIDR of the first subnet based on the second subnet’s CIDR
- The user can modify the first subnet CIDR from the console
- It is not possible to create a second subnet as one subnet with the same CIDR as the VPC has been created
- The user can modify the first subnet CIDR with AWS CLI
- A user has setup a VPC with CIDR 20.0.0.0/16. The VPC has a private subnet (20.0.1.0/24) and a public subnet (20.0.0.0/24). The user’s data centre has CIDR of 20.0.54.0/24 and 20.1.0.0/24. If the private subnet wants to communicate with the data centre, what will happen?
- It will allow traffic communication on both the CIDRs of the data centre
- It will not allow traffic with data centre on CIDR 20.1.0.0/24 but allows traffic communication on 20.0.54.0/24
- It will not allow traffic communication on any of the data centre CIDRs
- It will allow traffic with data centre on CIDR 20.1.0.0/24 but does not allow on 20.0.54.0/24 (as the CIDR block would be overlapping)
- A user has created a VPC with public and private subnets using the VPC wizard. The VPC has CIDR 20.0.0.0/16. The private subnet uses CIDR 20.0.0.0/24 . The NAT instance ID is i-a12345. Which of the below mentioned entries are required in the main route table attached with the private subnet to allow instances to connect with the internet?
- Destination: 0.0.0.0/0 and Target: i-a12345
- Destination: 20.0.0.0/0 and Target: 80
- Destination: 20.0.0.0/0 and Target: i-a12345
- Destination: 20.0.0.0/24 and Target: i-a12345
- A user has created a VPC with CIDR 20.0.0.0/16 using the wizard. The user has created a public subnet CIDR (20.0.0.0/24) and VPN only subnets CIDR (20.0.1.0/24) along with the VPN gateway (vgw-12345) to connect to the user’s data centre. The user’s data centre has CIDR 172.28.0.0/12. The user has also setup a NAT instance (i-123456) to allow traffic to the internet from the VPN subnet. Which of the below mentioned options is not a valid entry for the main route table in this scenario?
- Destination: 20.0.1.0/24 and Target: i-12345
- Destination: 0.0.0.0/0 and Target: i-12345
- Destination: 172.28.0.0/12 and Target: vgw-12345
- Destination: 20.0.0.0/16 and Target: local
- A user has created a VPC with CIDR 20.0.0.0/16. The user has created one subnet with CIDR 20.0.0.0/16 in this VPC. The user is trying to create another subnet with the same VPC for CIDR 20.0.0.1/24. What will happen in this scenario?
- The VPC will modify the first subnet CIDR automatically to allow the second subnet IP range
- It is not possible to create a subnet with the same CIDR as VPC
- The second subnet will be created
- It will throw a CIDR overlaps error
- A user has created a VPC with CIDR 20.0.0.0/16 using the wizard. The user has created both Public and VPN-Only subnets along with hardware VPN access to connect to the user’s data centre. The user has not yet launched any instance as well as modified or deleted any setup. He wants to delete this VPC from the console. Will the console allow the user to delete the VPC?
- Yes, the console will delete all the setups and also delete the virtual private gateway
- No, the console will ask the user to manually detach the virtual private gateway first and then allow deleting the VPC
- Yes, the console will delete all the setups and detach the virtual private gateway
- No, since the NAT instance is running
- A user has created a VPC with the public and private subnets using the VPC wizard. The VPC has CIDR 20.0.0.0/16. The public subnet uses CIDR 20.0.1.0/24. The user is planning to host a web server in the public subnet (port 80) and a DB server in the private subnet (port 3306). The user is configuring a security group for the public subnet (WebSecGrp) and the private subnet (DBSecGrp). Which of the below mentioned entries is required in the private subnet database security group (DBSecGrp)?
- Allow Inbound on port 3306 for Source Web Server Security Group (WebSecGrp)
- Allow Inbound on port 3306 from source 20.0.0.0/16
- Allow Outbound on port 3306 for Destination Web Server Security Group (WebSecGrp.
- Allow Outbound on port 80 for Destination NAT Instance IP
- A user has created a VPC with a subnet and a security group. The user has launched an instance in that subnet and attached a public IP. The user is still unable to connect to the instance. The internet gateway has also been created. What can be the reason for the error?
- The internet gateway is not configured with the route table
- The private IP is not present
- The outbound traffic on the security group is disabled
- The internet gateway is not configured with the security group
- A user has created a subnet in VPC and launched an EC2 instance within it. The user has not selected the option to assign the IP address while launching the instance. Which of the below mentioned statements is true with respect to the Instance requiring access to the Internet?
- The instance will always have a public DNS attached to the instance by default
- The user can directly attach an elastic IP to the instance
- The instance will never launch if the public IP is not assigned
- The user would need to create an internet gateway and then attach an elastic IP to the instance to connect from internet
- A user has created a VPC with public and private subnets using the VPC wizard. Which of the below mentioned statements is not true in this scenario?
- VPC will create a routing instance and attach it with a public subnet
- VPC will create two subnets
- VPC will create one internet gateway and attach it to VPC
- VPC will launch one NAT instance with an elastic IP
- A user has created a VPC with the public subnet. The user has created a security group for that VPC. Which of the below mentioned statements is true when a security group is created?
- It can connect to the AWS services, such as S3 and RDS by default
- It will have all the inbound traffic by default
- It will have all the outbound traffic by default
- It will by default allow traffic to the internet gateway
- A user has created a VPC with CIDR 20.0.0.0/16 using VPC Wizard. The user has created a public CIDR (20.0.0.0/24) and a VPN only subnet CIDR (20.0.1.0/24) along with the hardware VPN access to connect to the user’s data centre. Which of the below mentioned components is not present when the VPC is setup with the wizard?
- Main route table attached with a VPN only subnet
- A NAT instance configured to allow the VPN subnet instances to connect with the internet
- Custom route table attached with a public subnet
- An internet gateway for a public subnet
- A user has created a VPC with public and private subnets using the VPC wizard. The user has not launched any instance manually and is trying to delete the VPC. What will happen in this scenario?
- It will not allow to delete the VPC as it has subnets with route tables
- It will not allow to delete the VPC since it has a running route instance
- It will terminate the VPC along with all the instances launched by the wizard
- It will not allow to delete the VPC since it has a running NAT instance
- A user has created a public subnet with VPC and launched an EC2 instance within it. The user is trying to delete the subnet. What will happen in this scenario?
- It will delete the subnet and make the EC2 instance as a part of the default subnet
- It will not allow the user to delete the subnet until the instances are terminated
- It will delete the subnet as well as terminate the instances
- Subnet can never be deleted independently, but the user has to delete the VPC first
- A user has created a VPC with CIDR 20.0.0.0/24. The user has created a public subnet with CIDR 20.0.0.0/25 and a private subnet with CIDR 20.0.0.128/25. The user has launched one instance each in the private and public subnets. Which of the below mentioned options cannot be the correct IP address (private IP) assigned to an instance in the public or private subnet?
- 20.0.0.255
- 20.0.0.132
- 20.0.0.122
- 20.0.0.55
- A user has created a VPC with CIDR 20.0.0.0/16. The user has created public and VPN only subnets along with hardware VPN access to connect to the user’s datacenter. The user wants to make so that all traffic coming to the public subnet follows the organization’s proxy policy. How can the user make this happen?
- Setting up a NAT with the proxy protocol and configure that the public subnet receives traffic from NAT
- Setting up a proxy policy in the internet gateway connected with the public subnet
- It is not possible to setup the proxy policy for a public subnet
- Setting the route table and security group of the public subnet which receives traffic from a virtual private gateway
- A user has created a VPC with CIDR 20.0.0.0/16 using the wizard. The user has created a public subnet CIDR (20.0.0.0/24) and VPN only subnets CIDR (20.0.1.0/24) along with the VPN gateway (vgw-12345) to connect to the user’s data centre. Which of the below mentioned options is a valid entry for the main route table in this scenario?
- Destination: 20.0.0.0/24 and Target: vgw-12345
- Destination: 20.0.0.0/16 and Target: ALL
- Destination: 20.0.1.0/16 and Target: vgw-12345
- Destination: 0.0.0.0/0 and Target: vgw-12345
- Which two components provide connectivity with external networks? When attached to an Amazon VPC which two components provide connectivity with external networks? Choose 2 answers
- Elastic IPs (EIP) (Does not provide connectivity, public IP address will do as well)
- NAT Gateway (NAT) (Not Attached to VPC and still needs IGW)
- Internet Gateway (IGW)
- Virtual Private Gateway (VGW)
- You are attempting to connect to an instance in Amazon VPC without success You have already verified that the VPC has an Internet Gateway (IGW) the instance has an associated Elastic IP (EIP) and correct security group rules are in place. Which VPC component should you evaluate next?
- The configuration of a NAT instance
- The configuration of the Routing Table
- The configuration of the internet Gateway (IGW)
- The configuration of SRC/DST checking
- If you want to launch Amazon Elastic Compute Cloud (EC2) Instances and assign each Instance a predetermined private IP address you should:
- Assign a group or sequential Elastic IP address to the instances
- Launch the instances in a Placement Group
- Launch the instances in the Amazon virtual Private Cloud (VPC)
- Use standard EC2 instances since each instance gets a private Domain Name Service (DNS) already
- Launch the Instance from a private Amazon Machine image (AMI)
- A user has recently started using EC2. The user launched one EC2 instance in the default subnet in EC2-VPC Which of the below mentioned options is not attached or available with the EC2 instance when it is launched?
- Public IP address
- Internet gateway
- Elastic IP
- Private IP address
- A user has created a VPC with CIDR 20.0.0.0/24. The user has created a public subnet with CIDR 20.0.0.0/25. The user is trying to create the private subnet with CIDR 20.0.0.128/25. Which of the below mentioned statements is true in this scenario?
- It will not allow the user to create the private subnet due to a CIDR overlap
- It will allow the user to create a private subnet with CIDR as 20.0.0.128/25
- This statement is wrong as AWS does not allow CIDR 20.0.0.0/25
- It will not allow the user to create a private subnet due to a wrong CIDR range
- A user has created a VPC with CIDR 20.0.0.0/16 with only a private subnet and VPN connection using the VPC wizard. The user wants to connect to the instance in a private subnet over SSH. How should the user define the security rule for SSH?
- Allow Inbound traffic on port 22 from the user’s network
- The user has to create an instance in EC2 Classic with an elastic IP and configure the security group of a private subnet to allow SSH from that elastic IP
- The user can connect to a instance in a private subnet using the NAT instance
- Allow Inbound traffic on port 80 and 22 to allow the user to connect to a private subnet over the Internet
- A company wants to implement their website in a virtual private cloud (VPC). The web tier will use an Auto Scaling group across multiple Availability Zones (AZs). The database will use Multi-AZ RDS MySQL and should not be publicly accessible. What is the minimum number of subnets that need to be configured in the VPC?
- 1
- 2
- 3
- 4 (2 public subnets for web instances in multiple AZs and 2 private subnets for RDS Multi-AZ)
- Which of the following are characteristics of Amazon VPC subnets? Choose 2 answers
- Each subnet maps to a single Availability Zone
- A CIDR block mask of /25 is the smallest range supported
- Instances in a private subnet can communicate with the Internet only if they have an Elastic IP.
- By default, all subnets can route between each other, whether they are private or public
- Each subnet spans at least 2 Availability zones to provide a high-availability environment
- You need to design a VPC for a web-application consisting of an Elastic Load Balancer (ELB). a fleet of web/application servers, and an RDS database The entire Infrastructure must be distributed over 2 availability zones. Which VPC configuration works while assuring the database is not available from the Internet?
- One public subnet for ELB one public subnet for the web-servers, and one private subnet for the database
- One public subnet for ELB two private subnets for the web-servers, two private subnets for RDS
- Two public subnets for ELB two private subnets for the web-servers and two private subnets for RDS
- Two public subnets for ELB two public subnets for the web-servers, and two public subnets for RDS
- You have deployed a three-tier web application in a VPC with a CIDR block of 10.0.0.0/28. You initially deploy two web servers, two application servers, two database servers and one NAT instance tor a total of seven EC2 instances. The web, application and database servers are deployed across two availability zones (AZs). You also deploy an ELB in front of the two web servers, and use Route53 for DNS Web traffic gradually increases in the first few days following the deployment, so you attempt to double the number of instances in each tier of the application to handle the new load unfortunately some of these new instances fail to launch. Which of the following could the root caused? (Choose 2 answers) [PROFESSIONAL]
- The Internet Gateway (IGW) of your VPC has scaled-up adding more instances to handle the traffic spike, reducing the number of available private IP addresses for new instance launches.
- AWS reserves one IP address in each subnet’s CIDR block for Route53 so you do not have enough addresses left to launch all of the new EC2 instances.
- AWS reserves the first and the last private IP address in each subnet’s CIDR block so you do not have enough addresses left to launch all of the new EC2 instances.
- The ELB has scaled-up. Adding more instances to handle the traffic reducing the number of available private IP addresses for new instance launches
- AWS reserves the first four and the last IP address in each subnet’s CIDR block so you do not have enough addresses left to launch all of the new EC2 instances.
- A user wants to access RDS from an EC2 instance using IP addresses. Both RDS and EC2 are in the same region, but different AZs. Which of the below mentioned options help configure that the instance is accessed faster?
- Configure the Private IP of the Instance in RDS security group (Recommended as the data is transferred within the the Amazon network and not through internet – Refer link)
- Security group of EC2 allowed in the RDS security group
- Configuring the elastic IP of the instance in RDS security group
- Configure the Public IP of the instance in RDS security group
- In regards to VPC, select the correct statement:
- You can associate multiple subnets with the same Route Table.
- You can associate multiple subnets with the same Route Table, but you can’t associate a subnet with only one Route Table.
- You can’t associate multiple subnets with the same Route Table.
- None of these.
- You need to design a VPC for a web-application consisting of an ELB a fleet of web application servers, and an RDS DB. The entire infrastructure must be distributed over 2 AZ. Which VPC configuration works while assuring the DB is not available from the Internet?
- One Public Subnet for ELB, one Public Subnet for the web-servers, and one private subnet for the DB
- One Public Subnet for ELB, two Private Subnets for the web-servers, and two private subnets for the RDS
- Two Public Subnets for ELB, two private Subnet for the web-servers, and two private subnet for the RDS
- Two Public Subnets for ELB, two Public Subnet for the web-servers, and two public subnets for the RDS
- You have an Amazon VPC with one private subnet and one public subnet with a Network Address Translator (NAT) server. You are creating a group of Amazon Elastic Cloud Compute (EC2) instances that configure themselves at startup via downloading a bootstrapping script from Amazon Simple Storage Service (S3) that deploys an application via GIT. Which setup provides the highest level of security?
- Amazon EC2 instances in private subnet, no EIPs, route outgoing traffic via the NAT
- Amazon EC2 instances in public subnet, no EIPs, route outgoing traffic via the Internet Gateway (IGW)
- Amazon EC2 instances in private subnet, assign EIPs, route outgoing traffic via the Internet Gateway (IGW)
- Amazon EC2 instances in public subnet, assign EIPs, route outgoing traffic via the NAT
- You have launched an Amazon Elastic Compute Cloud (EC2) instance into a public subnet with a primary private IP address assigned, an internet gateway is attached to the VPC, and the public route table is configured to send all Internet-based traffic to the Internet gateway. The instance security group is set to allow all outbound traffic but cannot access the Internet. Why is the Internet unreachable from this instance?
- The instance does not have a public IP address
- The Internet gateway security group must allow all outbound traffic.
- The instance security group must allow all inbound traffic.
- The instance “Source/Destination check” property must be enabled.
- You have an environment that consists of a public subnet using Amazon VPC and 3 instances that are running in this subnet. These three instances can successfully communicate with other hosts on the Internet. You launch a fourth instance in the same subnet, using the same AMI and security group configuration you used for the others, but find that this instance cannot be accessed from the internet. What should you do to enable Internet access?
- Deploy a NAT instance into the public subnet.
- Assign an Elastic IP address to the fourth instance
- Configure a publically routable IP Address in the host OS of the fourth instance.
- Modify the routing table for the public subnet.
- You have a load balancer configured for VPC, and all back-end Amazon EC2 instances are in service. However, your web browser times out when connecting to the load balancer’s DNS name. Which options are probable causes of this behavior? Choose 2 answers
- The load balancer was not configured to use a public subnet with an Internet gateway configured
- The Amazon EC2 instances do not have a dynamically allocated private IP address
- The security groups or network ACLs are not property configured for web traffic.
- The load balancer is not configured in a private subnet with a NAT instance.
- The VPC does not have a VGW configured.
- When will you incur costs with an Elastic IP address (EIP)?
- When an EIP is allocated.
- When it is allocated and associated with a running instance.
- When it is allocated and associated with a stopped instance.
- Costs are incurred regardless of whether the EIP is associated with a running instance.
- A company currently has a VPC with EC2 Instances. A new instance being launched, which will host an application that works on IPv6. You need to ensure that this instance can initiate outgoing traffic to the Internet. At the same time, you need to ensure that no incoming connection can be initiated from the Internet on to the instance. Which of the following would you add to the VPC for this requirement?
- A NAT Instance
- A NAT Gateway
- An Internet Gateway
- An egress-only Internet gateway
Hi Jayendra,
Your site seems to be a very good source of information for people working on AWS. I believe the sample questions are for AWS Architect Associate Exam. I found few of the answers a bit different that it should have been. Can you help me some explanation.
For e.g. the 1st question on this page :
You have a business-to-business web application running in a VPC consisting of an Elastic Load Balancer (ELB), web servers, application servers and a database. Your web application should only accept traffic from predefined customer IP addresses. Which two options meet this security requirement? Choose 2 answers
I believe the answer should have been B and C.
Option D seems wrong because if I configure NACL to restrict inbound connection from ELB then how the request will go from ELB to instances. Same case for option A too.
Please correct me if I am wrong.
Hi GP
Thanks for the feedback. You are correct. It should not be NACL cause even through NACL can be configured to allow web traffic from Customer IPs it should still allow Outbound traffic on ephermal ports.. A is wrong as the web servers do not accept traffic from Customers but from the ELB. So it should be using X-Forward-for which can give you the actual customer IP address and Security groups with just the customer IP address and deny all outdound as it is stateful.
Hello, I have been studying this question and going back and forth on if A or C is more correct.
I think C is wrong. C uses security group at the ELB level to restrict inbound traffic, it is a better solution. BUT DENY all outbound traffic will not allow ELB to send traffic to the Webserver listener. From AWS document “Be sure to review the security group rules to ensure that they allow traffic on the listener and health check ports for the new load balancer.”
http://docs.aws.amazon.com/elasticloadbalancing/latest/classic/elb-security-groups.html .
A is not the best answer but it is not wrong. If the web traffic is passing through the ELB, then web server VPC security group should only allow the ELB as inbound. This configuration is allowing Web servers directly receiving traffic from customer by-pass the ELB.
ELB is open to all and passing the Client IP address to the instances behind it which can then check the client IP address.
With A, you can’t add IPs to the instances can instance will have only the ELB IP address as the origin of the request
C. ELB security groups to allow traffic from your customers’ IPs and deny all outbound traffic.
SGs are stateless and also SGs only “Allow” don’t “Deny”
SGs are stateless (I meant that in my comment)
Added the reason for the answer selection. SG are stateful.
Also as the Web Server are behind ELB the only way to restrict is either at ELB or use custom filter on Web Server
Hi Jayendra,
Would you able to help to ans this question? I believe B and E , please suggest. Thank you.
A company has configured and peered two VPCs: VPC-1 and VPC-2. VPC-1 contains only
private subnets, and VPC-2 contains only public subnets. The company uses a single AWS
Direct Connect connection and private virtual interface to connect their on-premises
network with VPC-1. Which two methods increases the fault tolerance of the connection to
VPC-1? Choose 2 answers
A. Establish a hardware VPN over the internet between VPC-2 ana the on-premises
network.
B. Establish a hardware VPN over the internet between VPC-1 and the on-premises
network.
C. Establish a new AWS Direct Connect connection and private virtual interface in the
same region as VPC-2.
D. Establish a new AWS Direct Connect connection and private virtual interface in adifferent AWS region than VPC-1.
E. Establish a new AWS Direct Connect connection and private virtual interface in the
same AWS region as VPC-1
I got the same question in the SA Exam. B is for sure the answer as establishing a VPN connection to the same VPC is the recommended solution.. However, I was not able to get to the other correct option and marked E as the second answer by the process of elimination. Direct Connect does not work across region so eliminating D. Also Direct Connect does not work with VPC Peering so eliminating VPC-2 options A & C.
why cant it be C
http://www.slideshare.net/AmazonWebServices/arc402-double-redundancy-with-aws-direct-connect
only catch is direct connect will have to go through a different co-location facilty as mentioned in the slide 15
C is with a different VPC i.e. VPC 2 which is peering with VPC 1 but peering will not allow you to access VPC 1 resources.
Right Jayendra…C is with different VPC…so C is not correct answer..
Which two methods increases the fault tolerance of the connection to
VPC-1?..I think only two option is correct..B and E.
Yup … only B & E mentioned @ Direct Connect Blog Post
Hi Jayendra,
For question number 2 , I believe the answer should be Destination : 20.0.0.0/16 and Target : Local which is not available of any option. Destination should be CIDR of VPC not CIDR of private subnet. You can not add the CIRD of private subnet where target is ‘Local’.
Please correct me if I am wrong.
Thanks.
with regards,
Tarun
Good catch, the CIDR block should be VPC CIDR block 20.0.0.0/16 with local as the target.
“Every route table contains a local route that enables communication within a VPC. You cannot modify or delete this route”
Corrected the answer.
Hi Jay,
Regarding question no 8; shouldn’t it be C.
According to aws-
“When you create each subnet, you provide the VPC ID and the CIDR block you want for the subnet. After you create a subnet, you can’t change its CIDR block”
Thanks Vivek, #C is correct as After you create a subnet, its CIDR block cannot be changed through any means and has to be deleted and recreated.
the question is “How can the user create the second subnet?”
so the answer is about the second subnet being attempted. not the first one.
Question 25: Which two components provide connectivity with external networks?
“When attached to an Amazon VPC”
This would be tricky. All of them are valid.
Que 25. I think it is mentioned that “with externak network” so C&D correct.. because other two i.e. A&B provide connection to reach C&D…
NAT still requires IGW for allowing instances in Private subnet to connect to Internet also it is not attached to VPC
Also, EIP, IGW, VGW are all attached to a VPC, however EIP does not provide connectivity and a public IP address can be used as well.
Question(24)
can you check this one again , i believe it should be (C) Destination: 20.0.1.0/16 and Target: vgw-12345 as when destination is VPN then will be sent to the VPN Gateway.
D is the right answer as it needs to reach out to all the destination through the VPN gateway.
Refer to the Scenario
Yeah you are right !
thanks for sharing , man this blog i believe became the #1 source for anyone who wants to prepare for the AWS Certificate
Hi Jayandra
I don’t understand q#5. Can you please explain ?
Thanks
K.Senthilkumar
The Question is targeting the security group configuration for NAT. NAT is basically to allow outgoing internet access for instances in the private group. You would configure the NAT and have outbound configurations enabled for http(80)/https(443) calls usually for package downloads.
#C is incorrect as the instance is in Public Subnet and handled through Internet Gateway and needs to configured for the instance.
Thanks a lot for the blog post. These are really very helpful. For NAT only outbound rule is required no inbound rules, as its for traffic to go out to Internet, not come in. So no inbound rule should be required. Even answer A should not be required along with C. What do you say?
NAT should allow inbound from the instances from the private subnet instances. So A is required.
Pls help me to understand Q – 5. A user has created a VPC with public and private subnets using the VPC wizard. Which of the below mentioned statements is true in this scenario?
I think C option should be correct But it shows option B is correct.
With VPC wizard, with public and private subnets it used to create NAT instance, and you did not did need to create NAT instance.
Pls elaborate que #20 answer….
VPC with Public and Private subnet created with Wizard used to create a NAT instance and hence it was not allowed to delete the VPC as it needs to be empty. The scenarios are bit changed now with the introduction of NAT Gateway. Refer Scenario 2
>>VPC with Public and Private subnet created with Wizard used to create a NAT gateway
did you meant to say ‘used to create a NAT *instance*’?
Yup the older Nat instance, edited the reply.
Currently it is allowing to delete Custom VPC with Public and Private subnet with not instance and with NAT Gateway…
In Question, if we consider, there are Public and Private subnets and assume that no NAT gateway created, that means NAT instance is created to connect for internet for public subnet, if so than it will not allow us to delete custom vpc….
pls correct me if wrong…
Correct, as previously NAT Gateway, which was introduced recently and is a managed service by AWS, did not exist and you had to create a NAT instance, which is basically a EC2 instance only. In that case, AWS did not allow you to delete the VPC.
So here as mentioned VPC was created with wizard and no instance is there, so it should allow to delete VPC..as i have checked….
So, “C” is the right answer… “It will terminate the VPC along with all the instances launched by the wizard”
pls suggest…
As mentioned the questions refers to previous implementation and is outdated, but AWS exam as not updated with the new features as far as i have experienced.
When creating a VPC using Wizard, previously, an NAT instance was created by AWS.
So previously, as it was a normal EC2 instance AWS did not allow to delete the VPC.
With the introduction of NAT Gateway, AWS creates a managed NAT gateway and deletes it when you delete a VPC.
Hi Jayendra
Is the NAT gateway deleted or detached on VPC deletion?
You need to delete the Gateways and Instances, without which it will not allow you delete the VPC.
Refer VPC Delete
Ok.
. thank you for giving such gr8 gt8 gr8 !!! Material…. and help….
Hi Jayendra,
Question 6:
A user has created a VPC with CIDR 20.0.0.0/24. The user has used all the IPs of CIDR and wants to increase the size of the VPC. The user has two subnets: public (20.0.0.0/28. and private (20.0.1.0/28
Since VPC CIDR is 20.0.0.0/24, private subnet 20.0.1.0/28 cannot be part of the VPC, right? Network part of the VPC is “20.0.0”, so 20.0.1 is not part of VPC.
Did you meant to say the subnets CIDR are 20.0.0.0/25 are 20.0.0.128/25?
Thanks Satish, yup the questions seems wrongly framed as the private subnet cannot be part of the defined VPC CIDR block. Updated the questions with the correct CIDR range.
Hi Jayendra,
Many THANKS to you for publishing these useful blog posts.
A small suggestion:
I found questions at the end of blog post very helpful. Instead of highlighting answers in each question, may be it is useful to post the correct answers (like Q1: A, D. Q2: B, etc.) in the end. Users can do the questions and then compare their answers after doing all questions — this way they know how many correct answers they got and gauge if they are ready for the certification exam. Seeing answers while reading the question influences users’s judgement on answer choice.
Cheers,
Satish
Actually agree on the suggestion. I was thinking of show answer button, but the main problem is the time and effort to revamp around 100 posts 🙂
Will try to do it for new posts.
Awesome! I think doing the new way for new posts should be good enough.
Could you please explain question 9?
The question targets the communication between VPC and an On Premises Data Center, where the CIDR block should not be overlapping.
To be more specific :
20.0.54.0/24 (2^8 adderesses) has a clash with 20.0.0.0/16 (2^16 addresses) vpc
Hi Jayendra – Firstly, thanks for all your excellent posts. It is really a very good synopsis.
Quick check on question no -29
In my opinion it should be – “C” . Can you please re-confirm?
A user has created a VPC with CIDR 20.0.0.0/24. The user has created a public subnet with CIDR 20.0.0.0/25. The user is trying to create the private subnet with CIDR 20.0.0.128/25. Which of the below mentioned statements is true in this scenario?
a, It will not allow the user to create the private subnet due to a CIDR overlap
b. It will allow the user to create a private subnet with CIDR as 20.0.0.128/25
c. This statement is wrong as AWS does not allow CIDR 20.0.0.0/25
d. It will not allow the user to create a private subnet due to a wrong CIDR range
Hi Rudra,
I will allow you to create the subnets with the CIDR block 20.0.0.0/25 as it would cover the IPs from 20.0.0.0 to 20.0.0.127.
20.0.0.128/25 would have the IPs from 20.0.0.128 to 20.0.0.255 which is non overlapping.
A user has created a VPC with public and private subnets using the VPC wizard. The user has not launched any instance manually and is trying to delete the VPC. What will happen in this scenario?
It will not allow to delete the VPC as it has subnets with route tables
It will not allow to delete the VPC since it has a running route instance
It will terminate the VPC along with all the instances launched by the wizard
It will not allow to delete the VPC since it has a running NAT instance
Question does not talk about launching of NAT instance. With this how come option D is correct answer?
This is an old question before the Nat Gateway was introduce where if you created a vpc with wizard it used too create NAT instance as well. Not valid anymore.
Question 1:
Correct answer is A & B. Here is my explanation for the same.
A is obviously correct as security group can be configured to accept traffic from predefined customer IPs
You can leverage AWS WAF to configure your webserver and filter the traffic based of HTTP header passed by load balancer. Hence #B is correct
The security group can be configured to only allow the inbound or outbound traffic. When you allow certain inbound traffic in security group, the outbound traffic is automatically allowed because of the stateful nature. Hence #C is wrong
In case if you deny all outbound traffic in NACL it will accept the inbound traffic but outbound hence #D is wrong.
Security Group can be configured to accept traffic from predefined customer IPs, but this does not work when the instances are behind an ELB as the instances do not get the Client IPs but the ELB IP.
Hi, Jayendrapatil
I am confused by Question 8:
A user has created a VPC with the public and private subnets using the VPC wizard. The VPC has CIDR 20.0.0.0/16. The public subnet uses CIDR 20.0.1.0/24. The user is planning to host a web server in the public subnet (port 80) and a DB server in the private subnet (port 3306). The user is configuring a security group for the public subnet (WebSecGrp) and the private subnet (DBSecGrp). Which of the below mentioned entries is required in the web server security group (WebSecGrp)?
A – Configure Destination as DB Security group ID (DbSecGrp) for port 3306 Outbound
B – Configure port 80 for Destination 0.0.0.0/0 Outbound
C – Configure port 3306 for source 20.0.0.0/24 InBound
D – Configure port 80 InBound for source 20.0.0.0/16
To me, it looks there’s nothing you need to do. Since the DB server and the WebServer is in the save VPC, they can reach each other by default. ( and by default, the outbound rule for security group is that you can reach all)
So in this scenario, the only thing you need to remember to do with the WebSecGrp is to open the 80 (and 443 for https) to the public internet.
With wizard creation, outbound is not open by default. Refer Link
Thanks!
Inbound and outbound is open by default.
Not when you create a new security group. But for Default it is.
Hi Jayendra,
First of all, thanks a ton for the material – extremely useful!
Can you explain Q#5?
“VPC bounds the main route table with a private subnet and a custom route table with a public subnet”. Are we trying to say that for a subnet to be private, we need to edit the route table?
And why is option C not the right answer? While creating a NAT instance is unrelated, it is not incorrect
Regards,
NMD
This is more of a question for VPC created through the Wizard. Refer VPC Creation Scenario
The way it is implemented is the :-
Main Route Table which points to NAT is associated with the Subnets. As there is no internet access, they are private.
Also, any new subnet created are by default associated with the Main Route Table making them private.
Custom Route table is associated with Internet Gateway with the Subnets associated being public.
Any new subnets created need to be explicitly associated with the Custom Route table to make it public
For NAT, it is created by the wizard depending upon the selection used.
I wasn’t aware of the scenarios while creating VPC using the wizard. Thank you!
I have created VPCs manually and I see that a default routing table is created but no subnets are associated it with automatically. Shouldn’t C be the correct answer?
Hi Jayendra,
I am not sure why d is correct answer. Because as I understand none of the CIDRs are overlapping.
20.0.1.0/24 – 256 hosts – 20.0.1.0-20.0.1.255
20.0.0.0/24 – 256 hosts – 20.0.0.0-20.0.0.255
20.0.54.0/24 – 256 hosts – 20.0.54.0-20.0.54.255
20.1.0.0/24 – 256 hosts – 20.1.0.0-20.1.0.255
Can you just double check?
10. A user has setup a VPC with CIDR 20.0.0.0/16. The VPC has a private subnet (20.0.1.0/24) and a public subnet (20.0.0.0/24). The user’s data centre has CIDR of 20.0.54.0/24 and 20.1.0.0/24. If the private subnet wants to communicate with the data centre, what will happen?
It will allow traffic communication on both the CIDRs of the data centre
It will not allow traffic with data centre on CIDR 20.1.0.0/24 but allows traffic communication on 20.0.54.0/24
It will not allow traffic communication on any of the data centre CIDRs
It will allow traffic with data centre on CIDR 20.1.0.0/24 but does not allow on 20.0.54.0/24 (as the CIDR block would be overlapping)
The VPC CIDR block should have an non overlapping IP addressess. As the VPC CIDR block is 20.0.0.0/16, so the range is 20.0.0.1 ~ 20.0.255.254 and would overlap with the 20.0.54.0/24
Hi Jay: So you mean the datacenter’s ID overlap will check with VPC’s CIDR , not only subnet’s CIDR?
Thats right. The check is with VPC’s CIDR.
For Question ‘1’ you mean using X-Forwarded-For from Apache level on webserver right ?
Yup. Please refer to AWS Documentation @ https://aws.amazon.com/premiumsupport/knowledge-center/log-client-ip-load-balancer-apache/
Hi – re: Q 32. Can you explain why it is 4 and not 2.
‘cos I was confused once I read: “You can have your Web servers in two VPC’s and configure the RDS servers to use those as well. You just need to configure RDS to be “not publicly accessible” to fulfill the needs of this scenario.”
On: http://cloudtrainingnotebook.blogspot.com/2016/10/aws-saa-study-list-rds.html
For Multi-AZ RDS to not be publicly accessible it needs 2 private subnets. Also for Web Tier to be hosted on the Multiple AZs you would need atleast instances to be hosted on 2 different public subnets. Hence the answer would be 4.
Thanks Jayendra 🙂
Why we can’t put both RDS and web tier in same private subnets? In this case two private subnets would be enough, what do you think?
Website needs to be in public, as there is no ELB or other service mentioned.
Hi Jayendra,
You mentioned “ENI has the following attributes”
This can be confusing, because we can think that all attributes should be set at the same time.
The correct statement is “ENI can include the following attributes”
Thanks Tarek, updated the statement …
Q1
Can we consider option D ,as NACL is stateless ,so DENY will work.
Also option C is talking about security group which is stateless , Deny will not work.
Security group are stateful and just need inbound rule.
NACLs are stateless so you need to define rules for both inbound and outbound. hence D would not work.
Hi Jayendra,
Question No.6. We are talking about configuring the Security group of NAT instance. NAT instance will not permit any inbound traffic from internet. It’s always outbound. So, the answer would be A & C as they are not required for NAT security group.
If it would have been a security group of the web server then A is required for DB to Web connectivity.
Please correct if i’m wrong …
Regards
Vivek
for NAT instance it should
allow Inbound from private subnets to them to communicate to internet – For Inbound allow Source: 20.0.1.0/24 on port 80
allow outbound to Internet as it needs to reach internet – For Outbound allow Destination: 0.0.0.0/0 on port 80 and port 443
It does not require, For Inbound allow Source: 20.0.0.0/24 on port 80, as the public subnets already have access to Internet. So #C is not required.
Refer AWS documentation – NAT SG
For Question 18, isn’t the answer B and C?
Which question is this for ? Q 18 is a single choice.
Question 18 Isn’t there is two not true statement? A and D ?
Refer VPC Scenario 2. Actually a NAT gateway is created. But before NAT gateway, as NAT instance was created by AWS.
For Question 19, how would option D would be right choice? when VPC is created it does not create the NAT instance automatically right?
Sorry, above question is for Question 21 in this page.
Check VPC Scenario 2 as a NAT is created when you create a VPC from Wizard.
Q:34 and 38
You need to design a VPC for a web-application consisting of an ELB a fleet of web application servers, and an RDS DB. The entire infrastructure must be distributed over 2 AZ. Which VPC configuration works while assuring the DB is not available from the Internet?
A.One Public Subnet for ELB, one Public Subnet for the web-servers, and one private subnet for the DB
B.One Public Subnet for ELB, two Private Subnets for the web-servers, and two private subnets for the RDS
C.Two Public Subnets for ELB, two private Subnet for the web-servers, and two private subnet for the RDS
D.Two Public Subnets for ELB, two Public Subnet for the web-servers, and two public subnets for the RDS
I am confused as to why we need two subnets for ELB. ELB do not belong any subnet. Elbs can be associated with multiple subnets. But ELB itself belongs to amazon infrastructure and scaled for you. So I don’t understand why we need sub nets for ELB.
Also why can’t we have only two private subnets (in two AZs) each having one web server and one DB server.. Please explain.
Once again great questions here. A big thank you
ELB is a managed service whose scalability is maintained by AWS. However, underlying it still launches instances to handle the traffic which is scaled accordingly. When you configure ELB you need to specify public Subnets (in case of external load balancer), in which the ELB instances would be launched.
If you specific a Single Subnet and that AZ goes down, the ELB is non functional even though you have your underlying instances in multiple AZs. So the best practice is to have multiple subnets associated with ELB.
ELBs themselves do not launch instances. Scalability Groups do, but they are not referenced in the question. The Availability Zones configured for the ELB (and their corresponding subnets) are where the Web Servers reside. I could see 6 subnets as being a viable choice if you could associate ELBs to (for example) Subnet1 and Subnet2, and independently have the EC2 instances running in subnets 3 and 4, but that will not work – not even with cross zone load balancing enabled. So the correct answer (which is not included here as an option) is two private subnets for the web-servers and two private subnets for RDS. The ELB will be configured to send traffic to the two private Web Server subnets, but is not itself independently associated with a subnet.
Dear sir,
I would like to ask ” you have posted this blog last 2 to 3 years ago, some changes has been done by AWS, so if I’m preparing my AWS exam with the help of you most informative blog, how I can distinguish changes done by AWS in syllabus.”
Kindly guide me sir.
Thank you so much.
Usually there are minor changes on the AWS side and the thing that changes are limitations or quota limits. So over 95% of the blog is still relevant.
I relish, cause I discovered exactly what I was taking a look for.
You have ended my 4 day long hunt! God Bless you man. Have a nice day.
Bye
Q14. A user has created a VPC with CIDR 20.0.0.0/16 using the wizard. The user has created both Public and VPN-Only subnets along with hardware VPN access to connect to the user’s data centre. The user has not yet launched any instance as well as modified or deleted any setup. He wants to delete this VPC from the console. Will the console allow the user to delete the VPC?
a. Yes, the console will delete all the setups and also delete the virtual private gateway
b. No, the console will ask the user to manually detach the virtual private gateway first and then allow deleting the VPC
c. Yes, the console will delete all the setups and detach the virtual private gateway
d. No, since the NAT instance is running
I think the answer should be b because we must detach or delete all gateways and resources that are associated with the VPC before you can delete it.
(Deletion of the VPC is possible only after terminating all instances within the VPC, and deleting all the components with the VPC for e.g. subnets, security groups, network ACLs, route tables, Internet gateways, VPC peering connections, and DHCP options)
Please explain.
As there are no other components within the VPC, the console will delete all the setups.
The user has created both Public and VPN-Only subnets along with hardware VPN access.
Subnets has been created here.
Deletion of the VPC is possible only after terminating all instances within the VPC, and deleting all the components with the VPC for e.g. SUBNETS
We can delete the VPC. Refer http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/working-with-vpcs.html#VPC_Deleting
You can delete your VPC at any time. However, you must terminate all instances in the VPC first. When you delete a VPC using the VPC console, we delete all its components, such as subnets, security groups, network ACLs, route tables, internet gateways, VPC peering connections, and DHCP options.
If you have a VPN connection, you don’t have to delete it or the other components related to the VPN (such as the customer gateway and virtual private gateway). If you plan to use the customer gateway with another VPC, we recommend that you keep the VPN connection and the gateways. Otherwise, your network administrator must configure the customer gateway again after you create a new VPN connection.
For Qn #10, shouldn’t the answer be ‘a’ instead of ‘d’.
Here is how I see it.
Private subnet 20.0.1.0/24 means it’s range is 20.0.1.0 to 20.0.1.255
Likewise data center range would be 20.0.54.0 to 20.0.54.255 (for 20.0.54.0/24) and 20.1.0.0 to 20.1.0.255 (for 20.1.0.0/24)
As such there is no overlap here.
VPC CIDR block and not the subnet should have an non overlapping IP addresses. As the VPC CIDR block is 20.0.0.0/16, so the range is 20.0.0.1
~ 20.0.255.254 and would overlap with the 20.0.54.0/24.
For question 30:
Can you please explain how CIDR 20.0.0.0/25 and 20.0.0.128/25 are not overlapping.
I will allow you to create the subnets with the CIDR block 20.0.0.0/25 as it would cover the IPs from 20.0.0.0 to 20.0.0.127.
20.0.0.128/25 would have the IPs from 20.0.0.128 to 20.0.0.255 which is non overlapping.
Thanks Jayendra.
I was able to check the ip address range for these CIDR blocks using online tool.
Can you guide me to some documentation that can explain why 20.0.0.0/25 is resolving to the range 20.0.0.0 to 20.0.0.127.
sorry , Not very clear on the CIDR block concepts.
Refer – https://www.lifewire.com/cidr-classless-domain-routing-818375
CIDR calculation is simple. The IP address is broken in 2^8 i.e. 0 – 255. 25 is the variable part of the address. 32 – 25 = 7 i.e. 2^7 = 128 addresses. hence 0 – 127.
thanks Jayendra…got it 🙂
another point that gets typically missed out and is misunderstood is, what is the starting IP of the range. It is the number mentioned .0 or .128 so the range starts with that number. So that would translate into: 0 – 127 (.0/25) or 128 – 255 (.128/25)
Hi Jayendra
for the below question. I am trying to understand the concepts better.. can you please provide some details or resource/link i can dig further? I am trying to understand this networking concept better & I do understand it could be an overwhelming topic but trying to understand this better at least at a high level.
my understanding is –
20.0.0.0/16 could span a range – 20.0.0.1 – 20.0.255.244
how will 20.0.54.0/24 overlap with this?
A user has setup a VPC with CIDR 20.0.0.0/16. The VPC has a private subnet (20.0.1.0/24) and a public subnet
(20.0.0.0/24). The user’s data centre has CIDR of 20.0.54.0/24 and 20.1.0.0/24. If the private subnet wants to
communicate with the data centre, what will happen?
20.0.0.0/16 is superset and 20.0.54.0/24 would be a part of it.
20.0.0.0/16 would translate to 20.0.[0-255].[0-255]
#43 and EIP will always incur a cost.
EIP is not charged if its in use. If you get it allocated but do not use it, you will be charged.
https://aws.amazon.com/premiumsupport/knowledge-center/elastic-ip-charges/
Hi Jayendra,
For question # 4 – Why option D is not right. You would need either an elastic IP or an Public IP to access the internet, right?
For question # 8 – Why option B is not right? You need to open port 80 to 0.0.0.0/0 for outbound connection to the Internet, right?
Thanks
I am also thinking there should be an EIP assigned to the instance in order for external reach it.
Can you explain Mr. Jayendra? Thank you very much.
for #4 – EIP is not mandatory and you can actually use Public IP as well for accessing the website. However, with security group on configured properly your site would be unreachable.
Hi Jayendra,
regarding new update that VPC can be resize, so Q7 should have no correct answer as per my understanding, please correct me
https://aws.amazon.com/blogs/aws/catching-up-on-some-recent-aws-launches-and-publications/
Thanks Hassan, its the latest AWS enhancement. Have updated the blog post.
Hi Jayendra, I got this question in AWS Dev Assoc exam today and am not sure of the answer. The question states that a set up is made with a public subnet and a private subnet with NAT in the public subnet, however the instance in private subnet still do not get connected to internet and we are asked to find which one will fix the issue:
a. Assign elastic IP to private subnet
b. Create secondary network instance..followed by something else can’t remember
c. deactive some checks on incoming/outgoing traffic (not the exact words)
d. Another option (can’t remember fullly) but talks about creating secondary network instance followed by some other things.
Any comments?
Should the disable Source/Destination question.
Refer to my NAT post – Question 1
Great! Thanks. I marked the right answer by means of eliminating the others.
Q30- I did not understand why is answer C correct – it will allow to create private subnet 20.0.0.128/25?. 128 is last ip within this subnet group mask /25and aws reserves first 3 and last ip. Request clarification. Thanks
For Q30. the answer B is marked as the correct answer. Are you referring to the same question ?
Yes Jayendra i am referring to B answer
Q30 -Answer is B – It will allow to create private subnet CIDR 20.0.0.128/25. My point is that it can allow private subnet up to 20.0.0.127/25.
It can allow 20.0.0.128/25, which will give it 128 IP addresses from 20.0.0.128 to 20.0.0.255.
Can you please explain in detail about question 10?
VPC CIDR block should have an non overlapping IP addresses. As the VPC CIDR block is 20.0.0.0/16, so the range is 20.0.0.1
~ 20.0.255.254 and would overlap with the 20.0.54.0/24, hence the traffic would not be allowed.
HI Jaynendra
Thanks for yours valuable inputs . However these questons are created by you or its originally came acorss exam.
pls confirm. beccause for associate exam few quesitions seems very tough and should be asked in professional exam.
br//Arbind
The ones with larger prose are professional ones for sure and are tough involving multiple services. You can concentrate on smaller ones.
Hello Jayendra,
Can you justify the answer for Question number 34.
Because i am suggesting answer would be B.
Even though ELB is a managed service, AWS launches an EC2 instance in an AZ for routing the traffic. If the AZ goes down the ELB is going to go down as well. If you attach 2 AZs to ELB, AWS launches ELB instances in the 2 AZs, which can route traffic traffic.
Hello Jayendra,
Can we have two public subnets where we can have ELBs and WebServers and two private subnets for RDS instances, since we need to assure only the DB is not available from the Internet.
You can have that combination as well as the requirement is for database only, however that is no a part of the answer.
Agree with you, I just wanna know the possibility, Jayendra. Thanks Much
Hello Jayendra,
Could you please help explain question 5? Via VPC wizard, the default subnet is public subnet, right? Why the answer is B, not D?
Thank you
Claire
They are not public by default. It creates a public and private subnet, which are associated with custom and main route table.
Refer VPC Scenario 2
A custom route table associated with the public subnet. This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC over IPv4, and an entry that enables instances in the subnet to communicate directly with the Internet over IPv4.The main route table associated with the private subnet. The route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC over IPv4, and an entry that enables instances in the subnet to communicate with the Internet through the NAT gateway over IPv4.The idea is when you create a subnet, it is by default associated with the main route table. And it is best to have the main route table not exposed to IGW so that the subnet is private by default.
Many thank for your help.
It’s a great website that you can learn AWS and get AWS certifications.
Thanks.
Thanks Kai, happy to help ..
question 14, 20 and 21 seems a bit confusing . Can u please clarify my doubts?
In the answer q 14 , you say that “Yes, the console will delete all the setups and detach the virtual private gateway”
in q20 you say that “A NAT instance configured to allow the VPN subnet instances to connect with the internet” is not present when the VPC is setup with the wizard.
but in q21 u say that “It will not allow to delete the VPC since it has a running NAT instance”
In all the questions the setup seems to be the same (viz. a public subnet and a private net).
Please clarify my doubts .
Thanks
q-14, is using VPC public and VPN subnets.
q-20 is also using VPC public and VPN subnets and a NAT instance is not created in this setup. Refer Scenario 3
q-21 is refering VPC with public and private subnets where a NAT instance was created before to allow instances in private subnet to reach internet. Refer scenario 2
Hi Jayendra, You mentioned in Q14 VPG is attached. While testing it shows that we need to detach the VPG first and then delete VPC. But your correct answer says it will directly delete VPC and it will detach VPG automatically.
Also could you please help little more to understand the use cases on VPG, VPN endpoints, Customer Gateway and VPC endpoints?
As per the previous AWS documentation, deletion was possible but might have been updated since. Text as below –
VGW and CGW are required to establish VPN connections between your premises and AWS VPC. VGW is on AWS side while CGW is on your side.
VPC endpoints help resources in AWS connect to AWS resources like S3 and DynamoDB through AWS internal network instead of internet providing low cost, high speed as well as security by keeping your resources private.
Hi Jay,
Can you please help me in calculating IP’s in a particular CIDR block as i am not able to solve the questions which includes calculation of IP’s or solving overlapping IP’s. I am preparing for Solution Architect Associate level exam and my exam is in the next week please help me.
Refer to https://www.lifewire.com/cidr-classless-domain-routing-818375 which provides a simple understanding. You just need to understand how many ips are available and whats the range.
Refer to https://www.lifewire.com/cidr-classless-domain-routing-818375 which provides a simple understanding. You just need to understand how many ips are available and whats the range.
why are webservers in privare subnet?
which question ?
in q.23 why 20.0.0.255 is not in private subnet??
the last ip address is reserved.
q18-> VPC will launch one NAT instance with an elastic IP. the question is which is not correct. So VPC wont create NAT instance right? or i am missing something?
VPC wizard used to create a NAT instance before the NAT gateway. So this statement is true.
Hi Jay,
Q: VPC has IPv6 enabled. To initiate outbound only IPv6 traffic from a private subnet, you need to route it through:
Answer: Egress only Internet gateway.
can you please help me understand this.
I thought its through nat gateway.
Hi, Can you please simplify explanation of how to identify the CIDR block overlapping scenarios. I see there are lot of questions mentioned here. I think I lack in some understanding which is why I cannot identity what IP range overlaps in a certain CIDR block.
Can you please explain, or direct me to any simplified explanation?
Sure will try to add a new topic on the same.
where’s 36.A’s link?
Here you go @ https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/USER_WorkingWithSecurityGroups.html#USER_WorkingWithSecurityGroups.Authorizing
Thank you very much
Hello Jayendra,
This is my 1st thread in this blog. So not sure if I have posted in correctly. Could you please respond when you get a chance.
I am getting the below error while attaching an EIP to an instance in North Virginia. But do not see this error in Mumbai region. FYI my VPC and Security group is default for the EC2.
“Network vpc-aab25fd0 is not attached to any internet gateway”
Thanks in advance for looking into it.
Cheeers,
Bhabani
Attached an Internet Gateway (IGW) to the VPC. Seems to be missing.
But its a default VPC. Do you still need an IGW for a default VPC?
Ah!!!! I realize by mistake I have deleted the defaulted IGW for that region. But not sure why even they allow to delete the default IGW or even the default VPC in the first place itself.
And one more thing I observed. Although they are allowing to delete the default security group, IGW and Route table but you can not delete the default NACL. Why is it so Jayandra ???
for question no 20 ,i think custom route table for public subnet should be a right answer .Please clarify
Question checks for components not present. Custom route table is created and associated with the public subnet.
Hi,
Thanks for this helpful blog.
Shouldn’t the answer for question 4 be the option ‘d’ and not ‘a’
A user has launched an EC2 instance and installed a website with the Apache webserver. The webserver is running but the user is not able to access the website from the Internet. What can be the possible reason for this failure?
a.The security group of the instance is not configured properly.
bThe instance is not configured with the proper key-pairs.
c.The Apache website cannot be accessed from the Internet.
d.Instance is not configured with an elastic IP.
Regards,
Sheldon
The website can still work if the Instance has an Public IP. Elastic IP is not mandatory.
Hi Jayendra,
Thanks for this helpful blog.
Below is still correct?
CIDR block from private (non-publicly routable) IP address can be assigned
172.16.0.0 – 172.31.255.255 (172.16/12 prefix)
Thanks,
Rajesh
Thats right there are limited sets of private IP ranges that you can assigned as a part of RFC standards.
for query 10, why 20.0.54.0/24 is overlapping?
o, I found the answer in previous comments.
Hi jayendrapatil,
Greater blog.
Q35: why choice 4 is correct. ELB doesn’t scale up. to me 5 and 2 are the correct answers. Would you 3xplain?
Thanks
Farzin
Hi Farzin, refer to ELB documentation.
ELB does need ip addressess and if it requires more if it scales.
thanks for your reply.
1. Does it apply to ELB classic only? The link you sent is just talks about classic.
2. Does it create a new ENI once it scales out?
Thanks,
it applies to ALB as well as they scale as per the traffic as well.
also: Why #2 is not correct? I know was receive 5 ip, however just one for DNS.
AWS reserves 5 IP address, so its partial information.
#35
jayendrapatil, yes, ELB needs CIDR block with at least a /27 bitmask, then here it is difficult to count it as right answer, because elb and its associated instances should be in same subnet, but the question is the subnet is only defined /28. 16-7-5=4 left instances buffer. only e is the right one.
Thats right Aaron, however given 2 options are needed that is the only one that makes sense.
thanks for your reply.
1. Does it apply to ELB classic only? The link you sent is just talks about classic.
2. Does it create a new ENI once it scales out?
Thanks,
Hi Jayednrapatil, thanks for your usefull blog.
I see that you mentioned the below point in IP Address section of VPC components.
“A Network Interface can be assigned either a Public IP or an Elastic IP. If you assign an instance, already having an Public IP, an Elastic IP, the public IP is released”
What i observed is if i assign elastic ip to the secondary private address of an instance the public ip associated with primary private address remains unchanged. In this case an instance can have both public and elastic ip as well.
Thanks.
As you are assigning the elastic ip to another network interface, both would co-exist. The statement is for a single network interface.
Hi Jayendra,
I think for ques-4 the answer a is valid but d also could be a reason as if an instance is having any service running on it but not associated with an Elastic(public ) IP so in that case it would not be accessible to the user on internet in anyway.
Please correct me if I am wrong.
It can be publicly available using a public ip as well. Elastic IP is not mandatory.
Dear sir please correct question no 17 as i think answer is c
Instance can be launched without a public/elastic ip with just the private ip.
As i test it question no 17 answer is b please i need your feekback
Its just that option d is more complete. The question does not mention its a public subnet. So whether a internet gateway exists is doubtful.
Hi,
for question 38 – if we this option , will that be a correct answer?
You need to design a VPC for a web-application consisting of an ELB a fleet of web application servers, and an RDS DB. The entire infrastructure must be distributed over 2 AZ. Which VPC configuration works while assuring the DB is not available from the Internet?
Answer:
Two Public Subnets for ELB, two public Subnet for the web-servers, and two private subnet for the RDS
The option would work. You need to choose the best option. If this is the only workable option, you can select this.
However, public subnets are not needed.
Which of the following is used to build network segment?
1. VPC
2.Security Group
3. NACLs
4. DR
Answer is 1,2,3 or 1,3 ?
DR is Disaster recovery ??? might be just a course lesson quiz to answer that but then 1,2,3 are the only valid ones.
Thanks Jayendra sir for best blogs and sharing point wise knowledge to AWS aspirants. You are Rockstar!
I am little confused with question 14
A user has created a VPC with CIDR 20.0.0.0/16 using the wizard. The user has created both Public and VPN-Only subnets along with hardware VPN access to connect to the user’s data centre. The user has not yet launched any instance as well as modified or deleted any setup. He wants to delete this VPC from the console. Will the console allow the user to delete the VPC?
How VPC can be deleted if it has NAT running instance? In question 21 it has different answer. which one is correct?
Q. 14 is without the Private Subnet and does not create a NAT instance. Q.21 is with Private and would create a NAT instance when created with Wizard.
Hi Jayendra sir. thanks for writing such a best blog.
My question is realted with 14 and 21.
Whether VPC can be deleted using wizard with deletion of all setup and detaching VPG or it will be blocked because of running NAT instance?
answers are different in 14 and 21. Please throw some light.
The Scenario is different for 14 and 21. VPN one does not create a NAT Instance.
Hi Jayendra,
I believe this statement under VPC Internet Gateway should be “To perform network address translation (NAT) for instances that have NOT been assigned public IP addresses”.
Thanks Bhargav, corrected the same.
Hi Jay,
Can u please explain Q:41
B as the instance needs to either have a public IP or Elastic IP address to be reachable from internet.
Hi Jayendra,
Regarding below question : I believe the answer is the private subnet should be able to connect to both the subnets on premise. Please let me know if I am wrong.
10. A user has setup a VPC with CIDR 20.0.0.0/16. The VPC has a private subnet (20.0.1.0/24) and a public subnet (20.0.0.0/24).
The user’s data centre has CIDR of 20.0.54.0/24 and 20.1.0.0/24. If the private subnet wants to communicate with the data centre, what will happen?
It will allow traffic communication on both the CIDRs of the data centre
It will not allow traffic with data centre on CIDR 20.1.0.0/24 but allows traffic communication on 20.0.54.0/24
It will not allow traffic communication on any of the data centre CIDRs
It will allow traffic with data centre on CIDR 20.1.0.0/24 but does not allow on 20.0.54.0/24 (as the CIDR block would be overlapping)
Logic :
20.0.1.0/24 = 20.0.1.0/20.0.1.255
20.0.54.0/24 = 20.0.54.0/54.255
20.1.0.0/24 = 20.1.0.0/20.1.0.255
VPC CIDR should not overlap and not the individual Subnets.
Confirm that the on-premises and VPC private networks are not overlapping, because overlapping subnets can cause routing issues over the VPN tunnel.Hi Jayendra,
Stuck with this-
1. SIngle VPC- CIDR created and working – 10.253.242.0/24
2. New CIDR created- 10.253.243.0/24
Problem-
The instances deployed in the new CIDR (diff private subnets) cannot access Internet or VPC endpoints like S3. Old instances in old CIDR are perfectly fine.
Checked and validated the following-
1. IGW is present in the public subnet (mgmt)
2. NAT GW is created and routes configured in each private subnet
3. SGs allow all outbound traffic to 0.0.0.0
What can be the issue?