EC2 Network Features
EC2 Network covers a lot of features for low latency access, High Performance Computing, Enhanced Networking, etc.
EC2 and VPC
- All the EC2 instance types can be launched in a VPC
- Instance types C4, M4 & T2 are available in VPC only and cannot be launched in EC2-Classic
- Launching an EC2 instance within a VPC provides the following benefits
- Assign static private IP addresses to instances that persist across starts and stops
- Assign multiple IP addresses to the instances
- Define network interfaces, and attach one or more network interfaces to the instances
- Change security group membership for the instances while they’re running
- Control the outbound traffic from the instances (egress filtering) in addition to controlling the inbound traffic to them (ingress filtering)
- Add an additional layer of access control to the instances in the form of network access control lists (ACL)
- Run the instances on single-tenant dedicated hardware
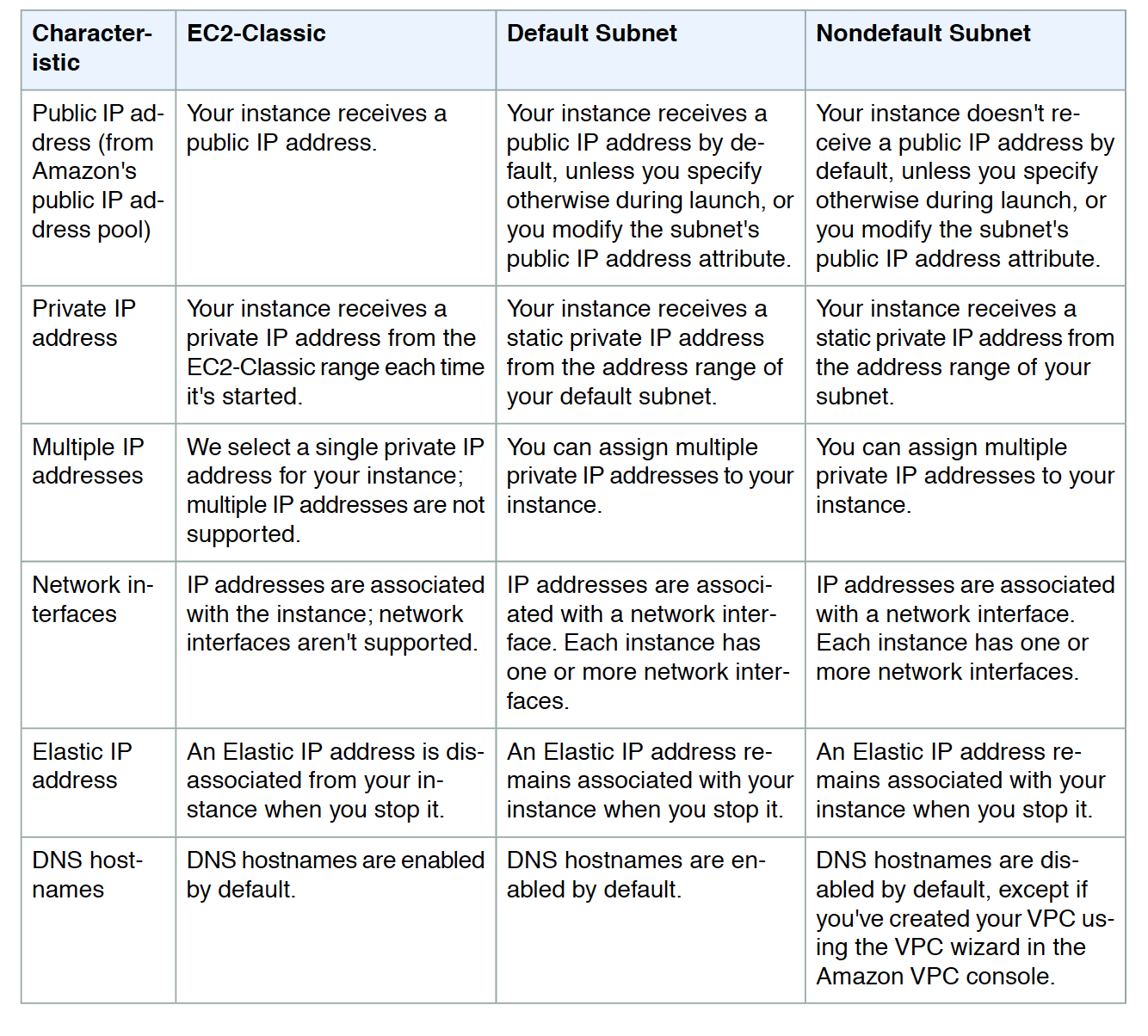
EC2 Instance IP Addressing
- Private IP address & Internal DNS Hostnames
- Private IP address is the IP address that’s not reachable over the internet and can be resolved only within the network
- When an instance is launched, the default network interface
eth0is assigned a private IP address and an internal DNS hostname, which resolves to the private IP address and can be used for communication between the instances in the same network only - Private IP address and DNS hostname cannot be resolved outside the network that the instance is in.
- Private IP address behaviour
- remains associated with the instance when it is stopped or rebooted
- is disassociated only when the instance is terminated
- An instance when launched can be assigned a private IP address or EC2 will automatically assign an IP address to the instance within the address range of the subnet
- Additional private IP addresses, known as secondary private IP addresses can also be assigned. Unlike primary private IP addresses, secondary private IP addresses can be reassigned from one instance to another.
- Public IP address and External DNS hostnames
- A public IP address is reachable from the Internet
- Each instance assigned a public IP address is also given an External DNS hostname.
- External DNS hostname resolves to the public IP address outside the network and to the private IP address within the network.
- Public IP address is associated with the primary Private IP address through NAT
- Within a VPC, an instance may or may not be assigned a public IP address depending upon the subnet Assign Public IP attribute
- Public IP address assigned to the pool is from the public IP address pool and is assigned to the instance, and not to the AWS account. It cannot be reused once disassociated and is released back to the pool
- Public IP address behaviour
- cannot be manually associated or disassociated with an instance
- is released when an instance is stopped or terminated.
- a new public IP address is assigned when a stopped instance is started
- is released when an instance is assigned an Elastic IP address
- is not assigned if there is more than one network interface attached to the instance
- Multiple Private IP addresses
- In EC2-VPC, multiple private IP addresses can be specified to the instances.
- This can be useful in the following cases
- Host multiple websites on a single server by using multiple SSL certificates on a single server and associating each certificate with a specific IP address.
- Operate network appliances, such as firewalls or load balancers, that have multiple private IP addresses for each network interface.
- Redirect internal traffic to a standby instance in case the instance fails, by reassigning the secondary private IP address to the standby instance.
- Multiple IP addresses work with Network Interfaces
- Secondary IP address can be assigned to any network interface, which can be attached or detached from an instance
- Secondary IP address must be assigned from the CIDR block range of the subnet for the network interface
- Security groups apply to network interfaces and not to IP addresses
- Secondary private IP addresses can be assigned and unassigned to ENIs attached to running or stopped instances.
- Secondary private IP addresses that are assigned to a network interface can be reassigned to another one if you explicitly allow it.
- Primary private IP addresses, secondary private IP addresses, and any associated Elastic IP addresses remain with the network interface when it is detached from an instance or attached to another instance.
- Although the primary network interface cannot be moved from an instance, the secondary private IP address of the primary network interface can be reassigned to another network interface.
Elastic IP Addresses
- An Elastic IP address is a static IP address designed for dynamic cloud computing.
- An elastic IP address can help mask the failure of an instance or software by rapidly remapping the address to another instance in the account.
- The elastic IP address is associated with the AWS account and it remains associated with the account until released explicitly
- An elastic IP address is NOT associated with a particular instance
- When an instance is launched in the default VPC, it is assigned 2 IP addresses, a private and a public IP address, which are mapped to the private IP address through NAT
- An instance launched in a non-default VPC is assigned only a private IP address unless a public address is specifically requested or the subnet public IP attribute is enabled
- When an Elastic IP address is assigned to an instance, the public IP address is disassociated with the instance
- For an instance, without a public IP address, to communicate to the internet it must be assigned an Elastic IP address
- When the Elastic IP address is dissociated the public IP address is assigned back to the instance. However, if a secondary network interface is attached to the instance, the public IP address is not automatically assigned
- Elastic IP addresses are not charged when associated with a running instance
- Amazon imposes a small hourly fee for an unused Elastic IP address to ensure efficient use of Elastic IP addresses. So charges would be applied, if it is not associated or associated with an instance in a stopped state or associated with an unattached network interface.
- All AWS accounts are limited to 5 EIPs (soft limit) because public (IPv4) Internet addresses are a scarce public resource
Elastic Network Interfaces (ENI)
- Elastic Network Interfaces (ENIs) are virtual network interfaces that can be attached to the instances running in a VPC only
- ENI consists of the following
- A primary private IP address.
- One or more secondary private IP addresses
- One Elastic IP address per private IP address.
- One public IP address, which can be auto-assigned to the elastic network interface for
eth0when an instance is launched, but only when an elastic network interface for eth0 is created instead of using an existing network interface - One or more security groups
- A MAC address
- A source/destination check flag
- A description
- ENI can be created without being attached to an instance
- ENI can be attached to an instance, detached from that instance and attached to another instance. Attributes of an ENI like elastic IP address, private IP address follow the ENI and when moved from one instance to another instance & all traffic to the ENI will be routed to the new instance.
- An instance in VPC always has a default primary ENI attached (eth0) with a private IP address assigned from the VPC range and cannot be detached
- Additional ENI (eth1-ethn) can be attached to the instance and the number varies depending upon the instance type
- Most important difference between eth0 and eth1 is that eth0 cannot be dynamically attached or detached from a running instance.
- Primary ENIs (eth0) is created automatically when an EC2 instance is launched and are also deleted automatically when the instance is terminated unless the administrator has changed a property of the ENI to keep it alive afterwards.
- Multiple elastic network interfaces are useful for use cases:
- Create a management network
- Primary ENI eth0 handles backend with more restrictive control
- Secondary ENI eth1 handles the public facing traffic
- Licensing authentication
- Fixed MAC address associated with a license authentication
- Use network and security appliances in your VPC
- configure a third-party network and security appliances (load balancers, NAT, proxy) with the secondary ENI
- Create dual-homed instances with workloads/roles on distinct subnets.
- Create a low-budget, high-availability solution
- If one of the instances serving a particular function fails, its elastic network interface can be attached to a replacement or hot standby instance pre-configured for the same role in order to rapidly recover the service
- As the interface maintains its private IP, EIP, and MAC address, network traffic will begin flowing to the standby instance as soon as it is attached to the replacement instance
- Create a management network
- ENI Best Practices
- ENI can be attached to an instance when it’s running (hot attach), when it’s stopped (warm attach), or when the instance is being launched (cold attach).
- Primary (eth0) interface can’t be detached
- Secondary (ethN) ENI can be detached when the instance is running or stopped.
- ENI in one subnet can be attached to an instance in another subnet, but the same AZ and same VPC
- When launching an instance from the CLI or API, both the primary (eth0) and additional elastic network interfaces can be specified
- Launching an Amazon Linux or Microsoft Windows Server instance with multiple network interfaces automatically configures interfaces, private IP addresses, and route tables on the operating system of the instance.
- A warm or hot attach of an additional ENI may require bringing up the second interface manually, configure the private IP address, and modify the route table accordingly.
- Instances running Amazon Linux or Microsoft Windows Server automatically recognize the warm or hot attach and configure themselves.
- Attaching another ENI to an instance is not a method to increase or double the network bandwidth to or from the dual-homed instance.
Placement Groups
- EC2 Placement groups determine how the instances are placed on the underlying hardware.
- AWS now provides three types of placement groups
- Cluster – clusters instances into a low-latency group in a single AZ
- Partition – spreads instances across logical partitions, ensuring that instances in one partition do not share underlying hardware with instances in other partitions
- Spread – strictly places a small group of instances across distinct underlying hardware to reduce correlated failures
Network Maximum Transmission Unit – MTU
- MTU of a network connection is the size, in bytes, of the largest permissible packet that can be transferred over the connection.
- The larger the MTU of the connection the more the data can be transferred in a single packet
- Largest ethernet packet size supported over most of the internet is 1500 MTU
- Jumbo Frames
- Jumbo frames are Ethernet frames that allow more than 1500 bytes of data by increasing the payload size per packet and thus increasing the percentage of the packet that is not packet overhead.
- Fewer packets are needed to send the same amount of usable data
- Jumbo frames should be used with caution for Internet-bound traffic or any traffic that leaves a VPC.
- Packets are fragmented by intermediate systems, which slows down this traffic.
- Maximum supported MTU for an instance depends on its instance type
- All EC2 instance types support 1500 MTU, and many current instance sizes support 9001 MTU or Jumbo frames
- Traffic is limited to a maximum MTU of 1500 in the following cases:
- Traffic outside of a given AWS Region for EC2-Classic
- Traffic outside of a single VPC
- Traffic over an inter-region VPC peering connection
- Traffic over VPN connections
- Traffic over an internet gateway
- For instances that are collocated inside a placement group, jumbo frames help to achieve the maximum network throughput possible, and they are recommended in this case.
Enhanced Networking
- Enhanced networking results in higher bandwidth, higher packet per second (PPS) performance, lower latency, consistency, scalability, and lower jitter.
- EC2 provides enhanced networking capabilities using single root I/O virtualization (SR-IOV) only on supported instance types
- SR-IOV is a method of device virtualization that provides higher I/O performance and lower CPU utilization
- It can be enabled for other OS distributions by installing the module with the correct attributes configured
Elastic Fabric Adapter – EFA
- An Elastic Fabric Adapter (EFA) is a network device that can be attached to the EC2 instance to accelerate High Performance Computing (HPC) and machine learning applications.
- EFA helps achieve the application performance of an on-premises HPC cluster, with the scalability, flexibility, and elasticity provided by AWS.
- EFA provides lower and more consistent latency and higher throughput than the TCP transport traditionally used in cloud-based HPC systems.
- EFA enhances the performance of inter-instance communication which is critical for scaling HPC and machine learning applications.
- EFA is optimized to work on the existing AWS network infrastructure and it can scale depending on application requirements.
- EFAs provide all of the same traditional IP networking features as ENAs, and they also support OS-bypass capabilities. OS-bypass enables HPC and machine learning applications to bypass the operating system kernel and to communicate directly with the EFA device.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A user is launching an EC2 instance in the US East region. Which of the below mentioned options is recommended by AWS with respect to the selection of the availability zone?
- Always select the US-East-1-a zone for HA
- Do not select the AZ; instead let AWS select the AZ
- The user can never select the availability zone while launching an instance
- Always select the AZ while launching an instance
- You have multiple Amazon EC2 instances running in a cluster across multiple Availability Zones within the same region. What combination of the following should be used to ensure the highest network performance (packets per second), lowest latency, and lowest jitter? Choose 3 answers
- Amazon EC2 placement groups (would not work for multiple AZs. Defaults to Cluster)
- Enhanced networking (provides network performance, lowest latency)
- Amazon PV AMI (Needs HVM)
- Amazon HVM AMI
- Amazon Linux (Can work on other flavors of Unix as well)
- Amazon VPC (Enhanced networking works only in VPC)
- Regarding the attaching of ENI to an instance, what does ‘warm attach’ refer to?
- Attaching an ENI to an instance when it is stopped
- Attaching an ENI to an instance when it is running
- Attaching an ENI to an instance during the launch process
- Can I detach the primary (eth0) network interface when the instance is running or stopped?
- Yes, You can.
- You cannot
- Depends on the state of the interface at the time
- By default what are ENIs that are automatically created and attached to instances using the EC2 console set to do when the attached instance terminates?
- Remain as is
- Terminate
- Hibernate
- Pause
- Select the incorrect statement
- In Amazon EC2, the private IP addresses only returned to Amazon EC2 when the instance is stopped or terminated
- In Amazon VPC, an instance retains its private IP addresses when the instance is stopped.
- In Amazon VPC, an instance does NOT retain its private IP addresses when the instance is stopped
- In Amazon EC2, the private IP address is associated exclusively with the instance for its lifetime
- To ensure failover capabilities, consider using a _____ for incoming traffic on a network interface”.
- primary public IP
- secondary private IP
- secondary public IP
- add on secondary IP
- Which statements are true about Elastic Network Interface (ENI)? (Choose 2 answers)
- You can attach an ENI in one AZ to an instance in another AZ
- You can change the security group membership of an ENI
- You can attach an instance to tow different subnets within a VPC by using two ENIs
- You can attach an ENI in one VPC to an instance in another VPC
- A user is planning to host a web server as well as an app server on a single EC2 instance, which is a part of the public subnet of a VPC. How can the user setup to have two separate public IPs and separate security groups for both the application as well as the web server?
- Launch a VPC instance with two network interfaces. Assign a separate security group to each and AWS will assign a separate public IP to them. (AWS cannot assign public IPs for instance with multiple ENIs)
- Launch VPC with two separate subnets and make the instance a part of both the subnets.
- Launch a VPC instance with two network interfaces. Assign a separate security group and elastic IP to them.
- Launch a VPC with ELB such that it redirects requests to separate VPC instances of the public subnet.
- An organization has created multiple components of a single application for compartmentalization. Currently all the components are hosted on a single EC2 instance. Due to security reasons the organization wants to implement two separate SSLs for the separate modules although it is already using VPC. How can the organization achieve this with a single instance?
- Create a VPC instance, which will have both the ACL and the security group attached to it and have separate rules for each IP address.
- Create a VPC instance, which will have multiple network interfaces with multiple elastic IP addresses.
- You have to launch two instances each in a separate subnet and allow VPC peering for a single IP.
- Create a VPC instance, which will have multiple subnets attached to it and each will have a separate IP address.
- Your system automatically provisions EIPs to EC2 instances in a VPC on boot. The system provisions the whole VPC and stack at once. You have two of them per VPC. On your new AWS account, your attempt to create a Development environment failed, after successfully creating Staging and Production environments in the same region. What happened?
- You didn’t choose the Development version of the AMI you are using.
- You didn’t set the Development flag to true when deploying EC2 instances.
- You hit the soft limit of 5 EIPs per region and requested a 6th. (There is a soft limit of 5 EIPs per Region for VPC on new accounts. The third environment could not allocate the 6th EIP)
- You hit the soft limit of 2 VPCs per region and requested a 3rd.
- A user has created a VPC with a public subnet. The user has terminated all the instances, which are part of the subnet. Which of the below mentioned statements is true with respect to this scenario?
- The user cannot delete the VPC since the subnet is not deleted
- All network interface attached with the instances will be deleted
- When the user launches a new instance it cannot use the same subnet
- The subnet to which the instances were launched with will be deleted
Very helpful summary. thanks 🙂
Hi Jayendra,
>>ENI in one subnet can be attached to an instance in another subnet, but the same AZ and same VPC
I think ENI can’t be moved to another **** subnet **** — private IP address of the ENI should be part of subnet IP address range so I think it can’t be moved?
From http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-eni.html
Note that you can’t move the elastic network interface to another subnet after it’s created, and you can only attach the interface to instances in the same Availability Zone.
Primary ENI cannot be detached from an instance. However, secondary ENI (eth1-ethN) can be attached and detached from an instance in an subnet to an other subnet. However, the subnet needs to be in the same AZ and the same VPC
Q7:
“To ensure failover capabilities, consider using a secondary private IPv4 for incoming traffic on a network interface. In the event of an instance failure, you can move the interface and/or secondary private IPv4 address to a standby instance.”
Could you please explain me the word: “move” in the above sentence? I am still confused how a secondary private IPv4 can help in case of instance failure.
Thank you.
you can detach an ENI associated to an instance to an other instance. As all security groups, ips are associated with ENI the network traffic is automatically routed to the new instance
Refer EC2 – Using ENI
You can create a network interface, attach it to an instance, detach it from an instance, and attach it to another instance. The attributes of a network interface follow it as it's attached or detached from an instance and reattached to another instance. When you move a network interface from one instance to another, network traffic is redirected to the new instance.“Q6. Select the incorrect statement
In Amazon EC2, the private IP addresses only returned to Amazon EC2 when the instance is stopped or terminated
In Amazon VPC, an instance retains its private IP addresses when the instance is stopped.
In Amazon VPC, an instance does NOT retain its private IP addresses when the instance is stopped
In Amazon EC2, the private IP address is associated exclusively with the instance for its lifetime”
Is the answer marked as correct indeed correct since the following is mentioned in the blog :
“Private IP address behaviour
remains associated with the Instance when it is stopped or rebooted
is disassociated only when the instance is terminated”
Please advise.
Thanks !
Please ignore my previous comment! I missed the word “INCORRECT” in the question 🙂
Sure No issues, be very careful reading the question as it is common occurrence in the exam.
HI Jajendra,
Answer for Qestion 6 should be B, not C.
If we need to fing INCORRECT sentence – then choose B.
Please provide feedback.
Thanks,
Yaroslav
The question is checking for the incorrect statement.
In Amazon VPC, an instance does not retain its private IP addresses when the instance is stopped – is Incorrect as the instance retains its private addresses with the stopped.
Even “a” is incorrect as it mentions about private IP address which does not get released when instance is stopped. Only public ip gets released when instance is stopped.
The Amazon EC2 here actually means Amazon EC2-Classic which preceded the VPC and is not used anymore. Option A is correct for EC2-Classic.
Hi Jayendra,
Could you pls help me on:
You are managing a legacy application Inside VPC with hard coded IP addresses in its configuration. Which two mechanisms will allow the application to failover to new instances without the need for reconfiguration? Choose 2 answers
A. Create an ELB to reroute traffic to a failover instance
B. Create a secondary ENI that can be moved to a failover instance
C. Use Route53 health checks to fail traffic over to a failover instance
D. Assign a secondary private IP address to the primary ENI0 that can be moved to a failover instance
B & D as the application is legacy and needs hard coded IP address, you can use secondary ENI or secondary IP address.
Thank You Jayendra 🙂
Btw.. using your blog, I completed the 3 associate exams. Thanks a LOT for your help.
Thats Great … Congrats ….
Hello,
For below question, “c” also seems correct answer.
Pls suggest.
7. To ensure failover capabilities, consider using a _____ for incoming traffic on a network interface”.
a. primary public IP
b. secondary private IP
c. secondary public IP
d. add on secondary IP
secondary private IP. Secondary public IP is not possible.
Hi Jayendra,
Your blogs are so succinct with so much information! Thank you for writing these!
I have a question about ENIs. If ENIs maintain private IPs when detached from an instance and attached to another, how can we have an ENI detached from one subnet and attached to an instance in another subnet in the same AZ and VPC?
Thanks!
Interesting question Veda, i have read the IP is carried with it but with the CIDR block being different that would be conflict. Let me check further on this also, if you have already it would be interesting to get the answer
Hi jayendra,
Thanks for such a nice blog.
any update on this?
—–interesting question Veda, i have read the IP is carried with it but with the CIDR block being different that would be conflict. Let me check further on this also, if you have already it would be interesting to get the answer—-
Thanks…
haven’t tried it yet, but should be easy to test by creating an ENI in subnet and trying to attached it to another instance in different subnet.
Hi,
For question #1 – why “b” is correct not “d”?
A user is launching an EC2 instance in the US East region. Which of the below mentioned options is recommended by AWS with respect to the selection of the availability zone?
a. Always select the US-East-1-a zone for HA
b. Do not select the AZ; instead let AWS select the AZ
c. The user can never select the availability zone while launching an instance
d.Always select the AZ while launching an instance
AZ selection is optional and if you do not select it AWS selects the best one for you based on system health and available capacity
Refer AWS documentation – EC2 – Using AZs