DynamoDB Security
- DynamoDB provides a highly durable storage infrastructure for mission-critical and primary data storage.
- Data is redundantly stored on multiple devices across multiple facilities in a DynamoDB Region.
- AWS handles basic security tasks like guest operating system (OS) and database patching, firewall configuration, and disaster recovery.
- DynamoDB protects user data stored at rest and in transit between on-premises clients and DynamoDB, and between DynamoDB and other AWS resources within the same AWS Region.
- Fine-Grained Access Control (FGAC) gives a high degree of control over data in the table.
- FGAC helps control who (caller) can access which items or attributes of the table and perform what actions (read/write capability).
- FGAC is integrated with IAM, which manages the security credentials and the associated permissions.
- VPC Endpoints allow private connectivity from within a VPC only to DynamoDB.
DynamoDB Encryption
- DynamoDB Security supports both encryption at rest and in transit.
Encryption in Transit
- DynamoDB Data in Transit encryption can be done by encrypting sensitive data on the client side or using encrypted connections (TLS).
- DAX supports encryption in transit, ensuring that all requests and responses between the application and the cluster are encrypted by transport level security (TLS), and connections to the cluster can be authenticated by verification of a cluster x509 certificate.
- All the data in DynamoDB is encrypted in transit
- communications to and from DynamoDB using the HTTPS protocol, which protects network traffic using SSL/TLS encryption.
- Data can also be protected using client-side encryption
Encryption at Rest
- Encryption at rest enables encryption for the data persisted (data at rest) in the DynamoDB tables.
- Encryption at rest includes the base tables, primary key, local and global secondary indexes, streams, global tables, backups, and DynamoDB Accelerator (DAX) clusters.
- Encryption at rest is enabled on all DynamoDB table data and cannot be disabled.
- Encryption at rest automatically integrates with AWS KMS for managing the keys used for encrypting the tables.
- Encryption at rest also supports the following KMS keys
- AWS owned CMK – Default encryption type. The key is owned by DynamoDB (no additional charge).
- AWS managed CMK – the key is stored in your account and is managed by AWS KMS (AWS KMS charges apply).
- Customer managed CMK – the key is stored in your account and is created, owned, and managed by you. You have full control over the KMS key (AWS KMS charges apply).
- Encryption at rest can be enabled only for a new table and encryption keys can be switched for an existing table.
- DynamoDB streams can be used with encrypted tables and are always encrypted with a table-level encryption key.
- On-Demand Backups of encrypted DynamoDB tables are encrypted using S3’s Server-Side Encryption
- Encryption at rest encrypts the data using 256-bit AES encryption.
- DAX clusters cannot use customer-managed key encryption.
DynamoDB Encryption Client
- DynamoDB Encryption Client is a software library that helps protect the table data before sending it to DynamoDB.
- Encrypting the sensitive data in transit and at rest helps ensure that the plaintext data isn’t available to any third party, including AWS.
- helps in end-to-end data encryption.
- encrypts attribute values that can be controlled but do not encrypt the entire table, attribute names, or primary key.
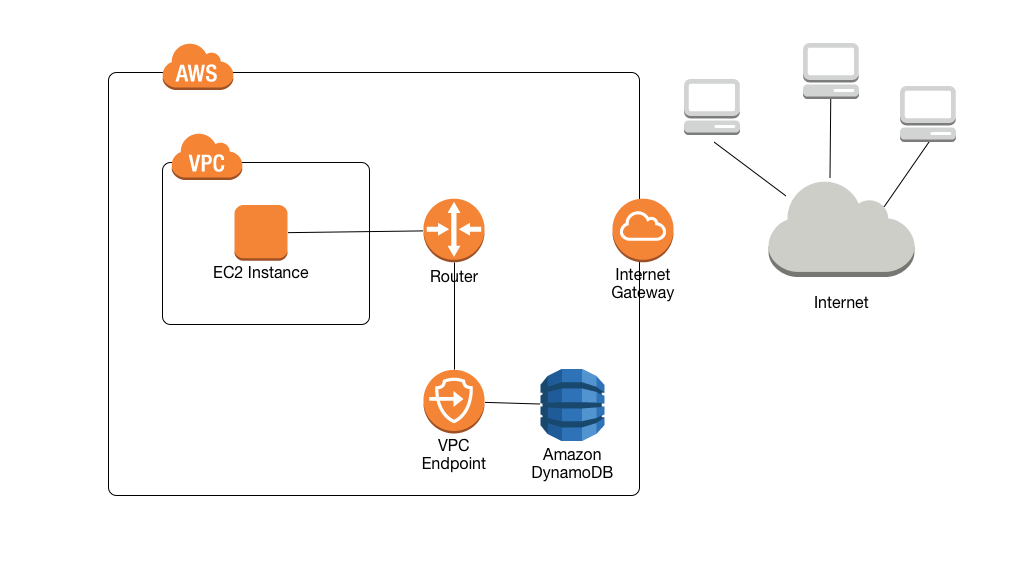
VPC Endpoints
- By default, communications to and from DynamoDB use the HTTPS protocol, which protects network traffic by using SSL/TLS encryption.
- A VPC endpoint for DynamoDB enables EC2 instances in the VPC to use their private IP addresses to access DynamoDB with no exposure to the public internet.
- Traffic between the VPC and the AWS service does not leave the Amazon network.
- EC2 instances do not require public IP addresses, an internet gateway, a NAT device, or a virtual private gateway in the VPC.
- VPC Endpoint Policies to control access to DynamoDB.
DynamoDB Security Best Practices
- DynamoDB encrypts at rest all user data stored in tables, indexes, streams, and backups using encryption keys stored in KMS.
- DynamoDB can be configured to use an AWS owned key (default encryption type), an AWS managed key, or a customer managed key to encrypt user data.
- Use IAM Roles to authenticate access to DynamoDB
- Use VPC endpoint and policies to access DynamoDB
- DynamoDB Encryption Client is a software library that helps in client-side encryption and protects the table data before you send it to DynamoDB.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- What are the services supported by VPC endpoints, using the Gateway endpoint type?
- Amazon EFS
- Amazon DynamoDB
- Amazon Glacier
- Amazon SQS

2 thoughts on “AWS DynamoDB Security”
Comments are closed.