Table of Contents
hide
AWS Control Tower
- AWS Control Tower helps set up and govern an AWS multi-account environment, following prescriptive best practices.
- AWS Control Tower offers the easiest way to set up and govern a secure, compliant, well-architected, multi-account AWS environment, that adheres to corporate standards, and meets regulatory requirements based on best practices established by working with thousands of enterprises.
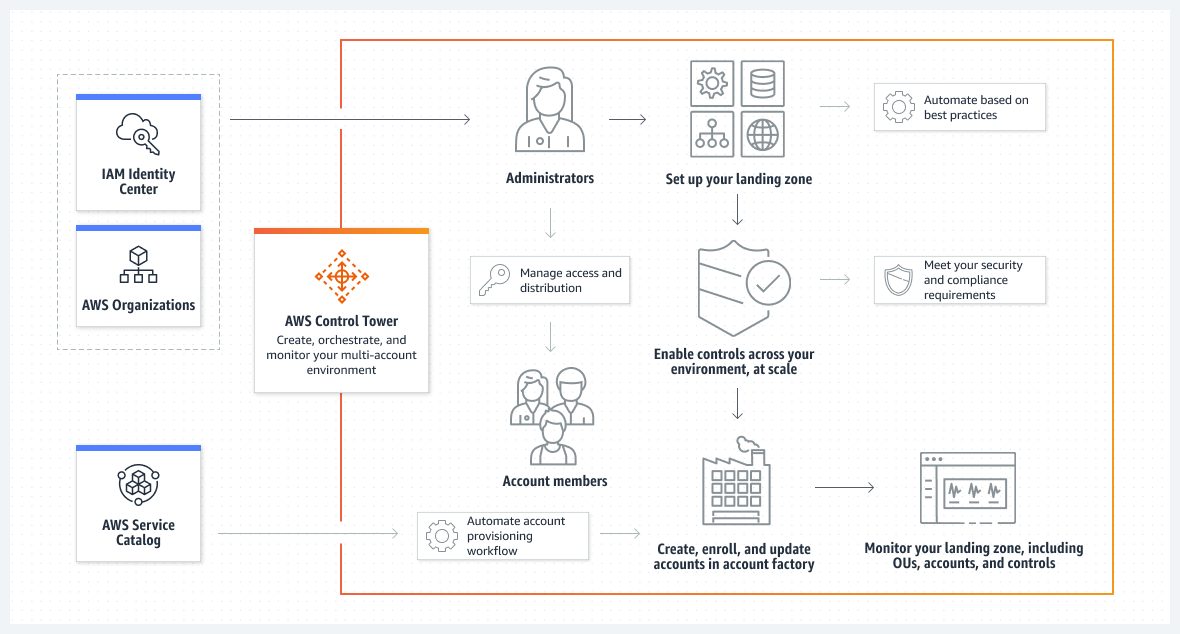
- AWS Control Tower orchestrates the capabilities of several other AWS services, including AWS Organizations, AWS Service Catalog, and AWS Identity Center (AWS Single Sign-on), to build a landing zone in less than an hour. Resources are set up and managed on your behalf.
- Control Tower applies preventive and detective controls (guardrails) to help keep AWS organizations and accounts from drift, which is a divergence from best practices for e.g, guardrails can be used to help ensure that security logs and necessary cross-account access permissions are created, and not altered.
- Control Tower enables end-users on distributed teams to provision new AWS accounts quickly using configurable account templates in Account Factory. The central cloud administrators can monitor that all accounts are aligned with established, company-wide compliance policies.
Control Tower Features
- Landing zone
- A landing zone is a well-architected, multi-account environment that’s based on security and compliance best practices.
- It is the enterprise-wide container that holds all of the organizational units (OUs), accounts, users, and other resources that need to be subject to compliance regulation.
- A landing zone can scale to fit the needs of an enterprise of any size.
- AWS Control Tower automates a landing zone to set up a baseline environment that includes:
- A multi-account environment using AWS Organizations.
- Identity management using AWS Single Sign-On (SSO).
- Federated access to accounts using AWS SSO.
- Centralize logging from CloudTrail, and Config stored in S3.
- Cross-account security audits using AWS IAM and AWS SSO.
- Guardrails
- A guardrail is a high-level rule that provides ongoing governance for the overall AWS environment.
- Two kinds of guardrails exist
- Preventive – uses SCPs and helps establish intent and prevent deployment of resources that don’t conform to the policies.
- Detective – using AWS Config and continuously monitors deployed resources for non-conformance.
- Three categories of guidance apply to the two kinds of guardrails
- mandatory
- strongly recommended
- elective
- AWS Control Tower automatically translates guardrails into granular AWS policies by:
- Establishing a configuration baseline using AWS CloudFormation
- Preventing configuration changes of the underlying implementation using SCPs (for preventive guardrails)
- Continuously detecting configuration changes through AWS Config rules (for detective guardrails)
- Updating guardrail status on the AWS Control Tower dashboard
- Account Factory
- An Account Factory is a configurable account template that helps to standardize the provisioning of new accounts with pre-approved account configurations.
- AWS Control Tower offers a built-in Account Factory that helps automate the account provisioning workflow in the organization.
- Account Factory uses AWS Service Catalog to provision new accounts.
- Dashboard
- The dashboard offers continuous oversight of the landing zone to your team of central cloud administrators.
- Use the dashboard to see provisioned accounts across the enterprise, guardrails enabled for policy enforcement, guardrails enabled for continuous detection of policy non-conformance and non-compliant resources organized by accounts and OUs.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A company is expanding its use of AWS services across its portfolios. The company wants to provision AWS accounts for each team to ensure a separation of business processes for security, compliance, and billing. Account creation and bootstrapping should be completed in a scalable and efficient way so new accounts are created with a defined baseline and governance guardrails in place. An administrator needs to design a provisioning process that saves time and resources. Which action should be taken to meet these requirements?
- Automate using AWS Elastic Beanstalk to provision the AWS accounts, set up infrastructure, and integrate with AWS Organizations.
- Create bootstrapping scripts in AWS OpsWorks and combine them with AWS CloudFormation templates to provision accounts and infrastructure.
- Use AWS Config to provision accounts and deploy instances using AWS Service Catalog.
- Use AWS Control Tower to create a template in Account Factory and use the template to provision new accounts.