Google Cloud KMS Key Management Service
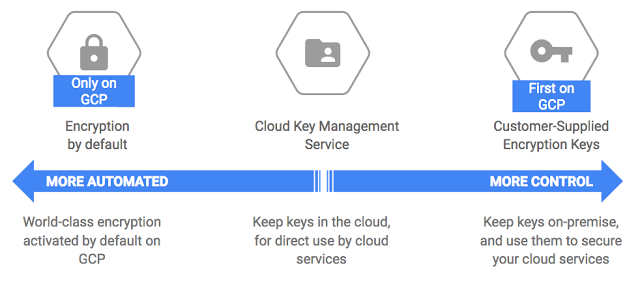
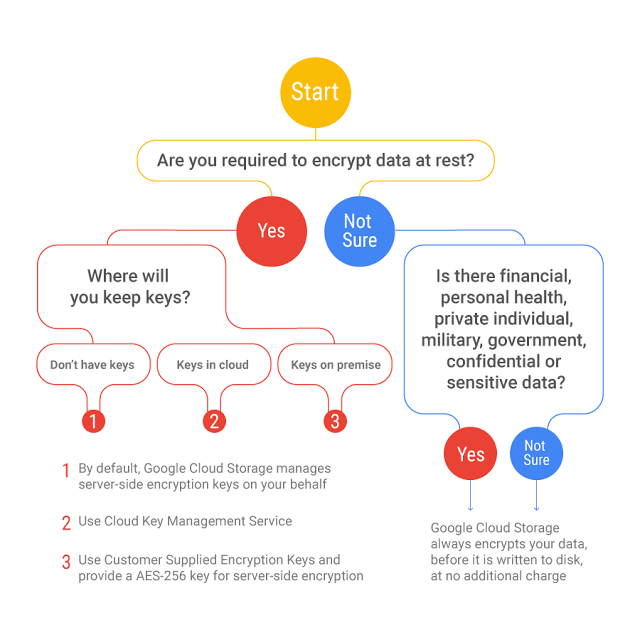
- Google Cloud KMS – Key Management Service provides a centralized, scalable, fast cloud key management service to manage encryption keys
- KMS helps apply hardware security modules (HSMs) effortlessly to the most sensitive data by just a toggle between software- and hardware-protected encryption keys with the press of a button.
- KMS provides support for external keys using Cloud External Key Manager to protect the data in Google Cloud and separate the data from the key
Cloud KMS Keys, Keys Versions, and Key Rings
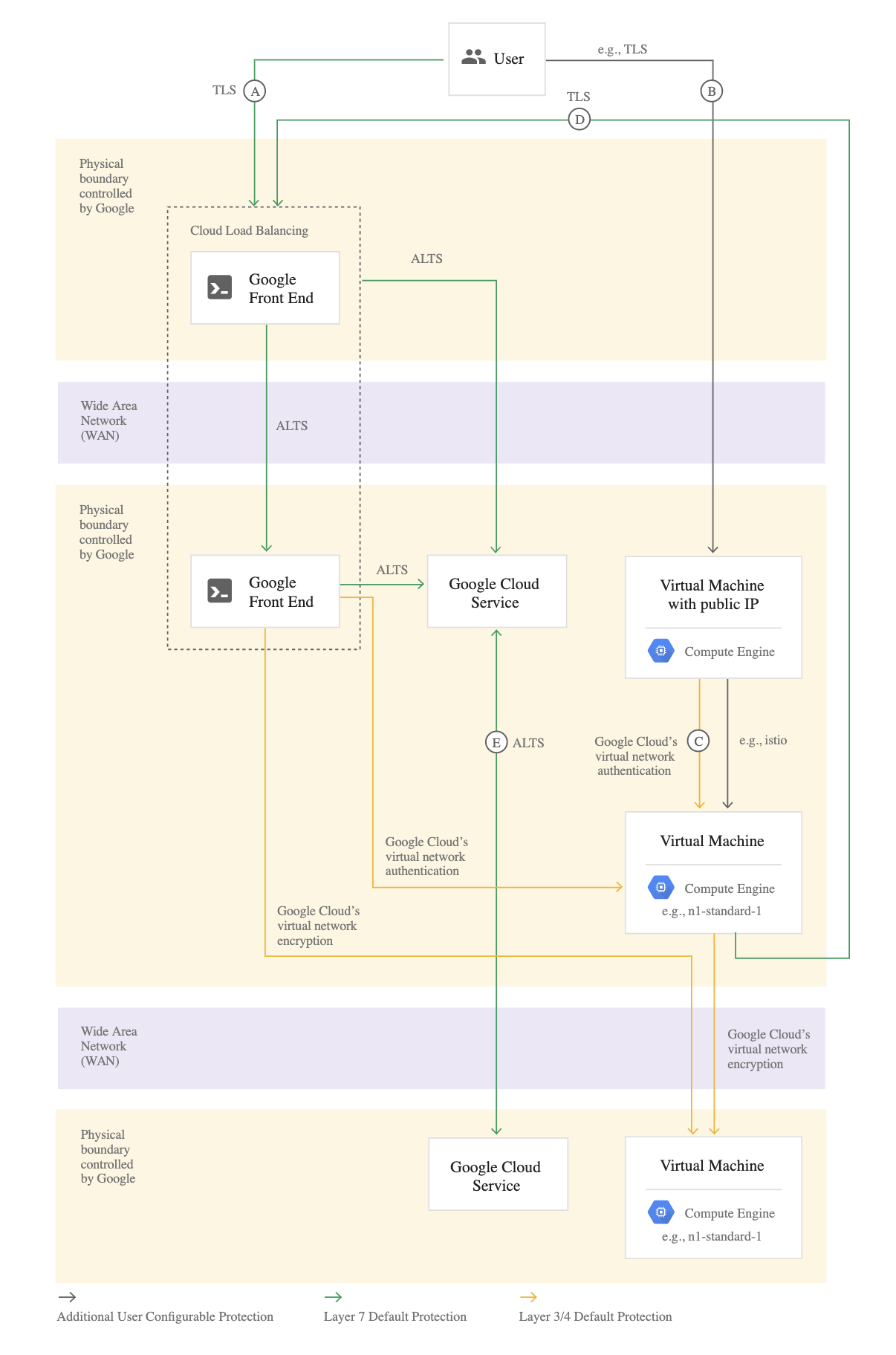
- A Cloud KMS key is a named object containing one or more key versions, along with metadata for the key.
- A key exists on exactly one key ring tied to a specific location.
- After creation, a key cannot be moved to another location or exported.
 Key
Key
- A named object representing a cryptographic key that is used for a specific purpose. The key material – the actual bits used for cryptographic operations – can change over time as new key versions are created
- Key is the most important object for understanding KMS usage.
- Key purpose and other attributes of the key are connected with and managed using the key.
- IAM permissions and roles can be used to allow and deny access to keys
- Cloud KMS supports both asymmetric keys and symmetric keys.
- Symmetric key
- is used for symmetric encryption to protect some corpus of data for e.g., using AES-256 to encrypt a block of plaintext.
- Asymmetric key
- consists of a public and private key.
- can be used for asymmetric encryption, or for creating digital signatures.
- Key’s type (symmetric or asymmetric) can’t be changed after key creation
Key Ring
- A grouping of keys for organizational purposes.
- Key ring belongs to Google Cloud project and resides in a specific location
- Keys inherit IAM policies from the Key Ring that contains them.
- Grouping keys with related permissions in a key ring allows you to grant, revoke, or modify permissions to those keys at the key ring level without needing to act on each key individually.
- Key rings provide convenience and categorization
- To prevent resource name collisions, a key ring cannot be deleted.
- Key rings and keys do not have billable costs or quota limitations, so their continued existence does not affect costs or production limits.
Key Metadata
- Includes resource names, properties of KMS resources such as IAM policies, key type, key size, key state, and any other derived data
- Key metadata can be managed differently than the key material.
Key Version
- Represents the key material associated with a key at some point in time.
- Key version is the resource that contains the actual key material.
- Granting access to a key also grants access to all of its enabled versions. Access to a key version cannot be managed.
- A key version can be disabled or destroyed without affecting other versions
- Disabling or destroying a key also disables or destroys each key version.
- Versions are numbered sequentially, beginning with version 1.
- When a key is rotated, a new key version is created with new key material.
- The same logical key can have multiple versions over time, thus limiting the use of any single version.
- Symmetric keys will always have a primary version. This version is used for encrypting by default, if not version is specified
- Asymmetric keys do not have primary versions, and a version must be specified when using the key.
- When Cloud KMS performs decryption using symmetric keys, it identifies automatically which key version is needed to perform the decryption.
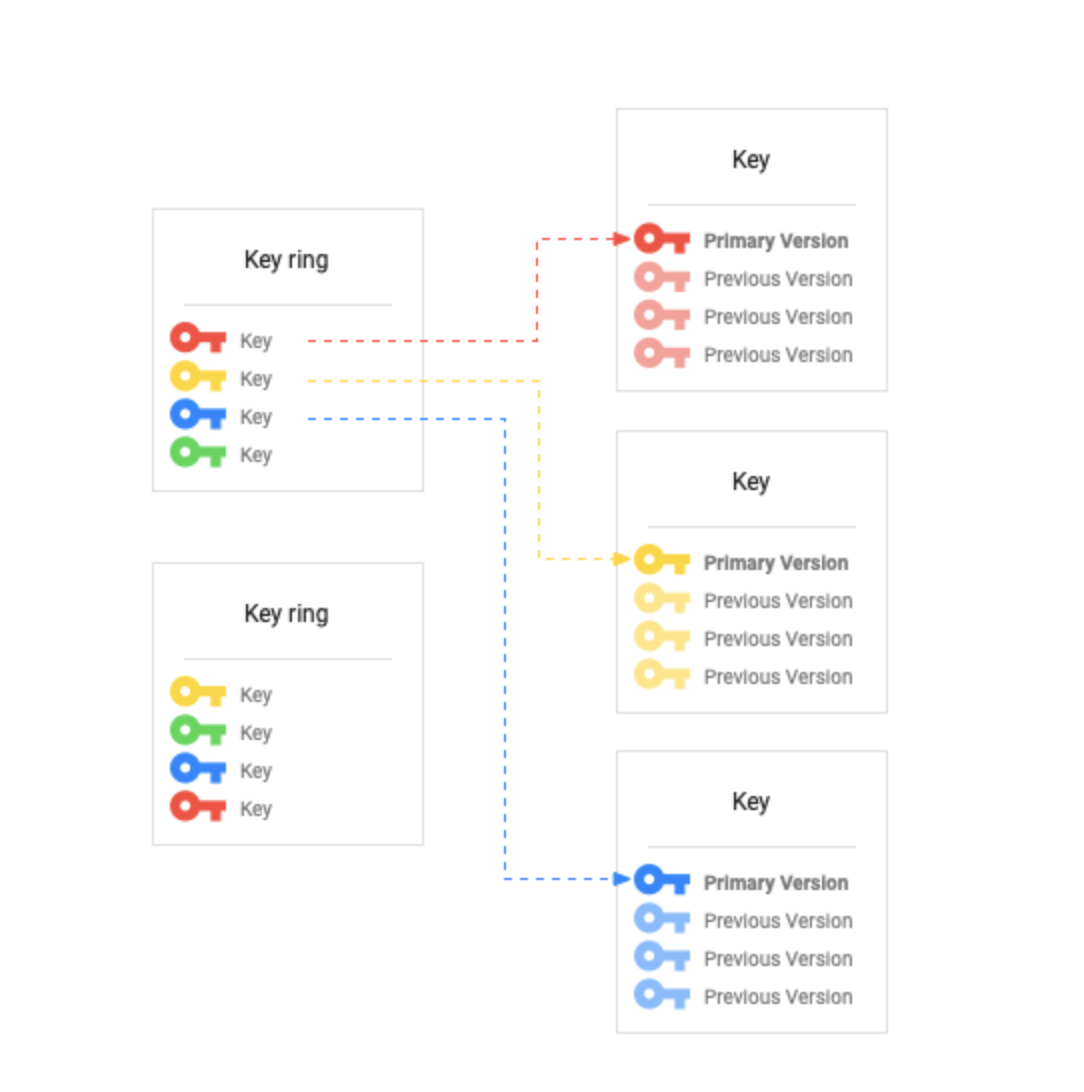
Key States
- A key version’s state is always one of the following:
- Pending generation (PENDING_GENERATION)
- Applies to asymmetric keys only
- is still being generated and can’t be used, enabled, disabled, or destroyed yet.
- KMS will automatically change the state to enabled as soon as the version is ready.
- Enabled (ENABLED)
- Disabled (DISABLED)
- may not be used, but the key material is still available, and the version can be placed back into the enabled state.
- Scheduled for destruction (DESTROY_SCHEDULED):
- is scheduled for destruction, and will be destroyed soon.
- can be placed back into the disabled state.
- Destroyed (DESTROYED)
- is destroyed, and the key material is no longer stored in Cloud KMS.
- If the key version was used
- for asymmetric or symmetric encryption, any ciphertext encrypted with this version is not recoverable.
- for digital signing, new signatures cannot be created.
- may not leave the destroyed state once entered.
- A key version can only be used when it is enabled.
Key Rotation
- For symmetric encryption, periodically and automatically rotating keys is a recommended security practice
- Cloud MS does not support automatic rotation of asymmetric keys and has to be done manually
- With key rotation, data encrypted with previous key versions is not automatically re-encrypted with the new key version.
- Rotating keys provides several benefits:
- Limiting the number of messages encrypted with the same key version helps prevent brute-force attacks enabled by cryptanalysis.
- In the event that a key is compromised, regular rotation limits the number of actual messages vulnerable to compromise.
- If you suspect that a key version is compromised, disable it and revoke access to it as soon as possible.
- Regular key rotation helps validate the key rotation procedures before a real-life security incident occurs.
- Regular key rotation ensures that the system is resilient to manual rotation, whether due to a security breach or the need to migrate your application to a stronger cryptographic algorithm.
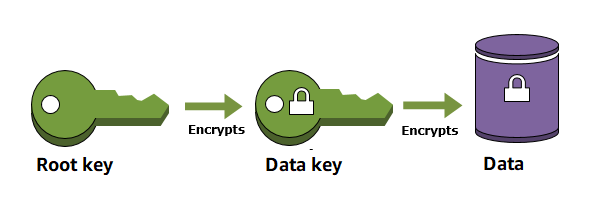
Key Hierarchy
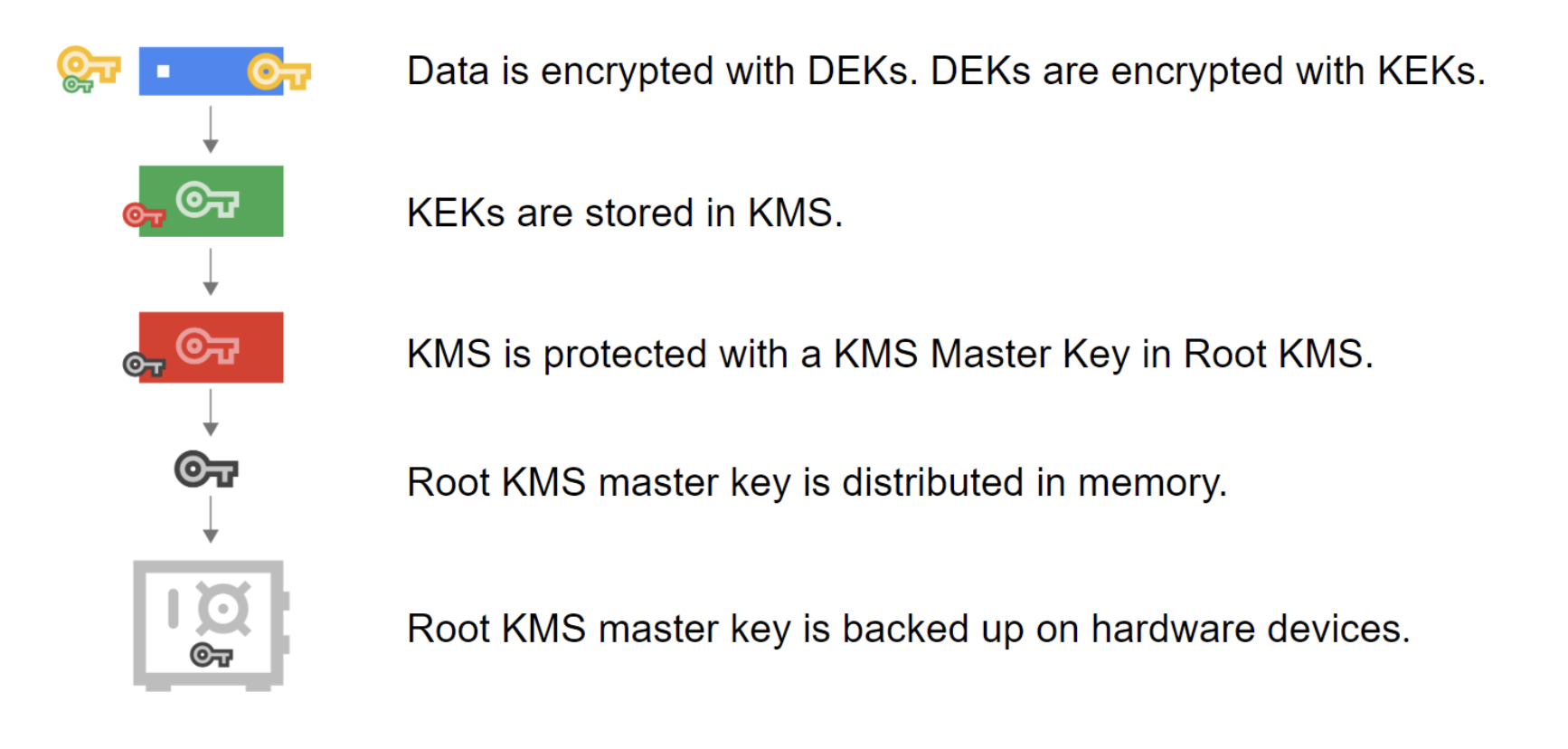
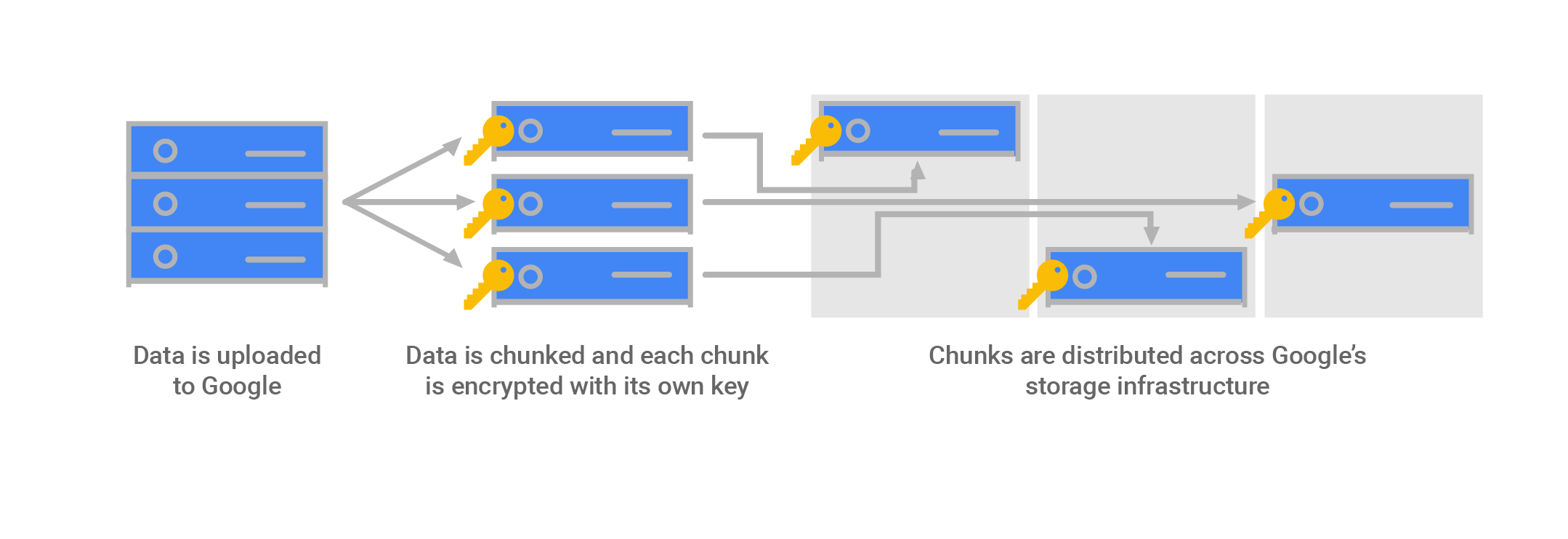
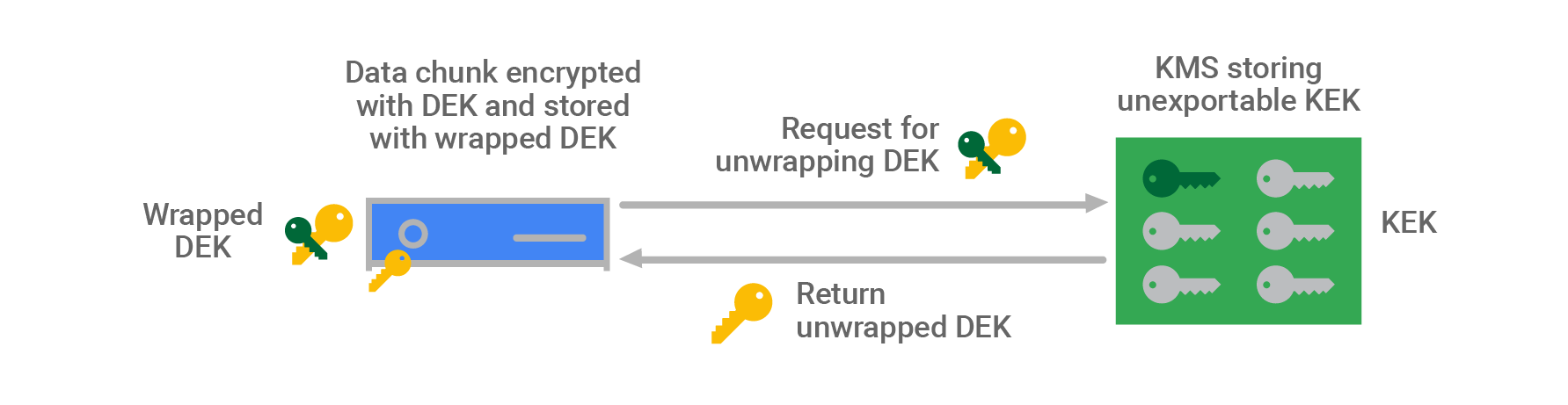
- Data Encryption Key (DEK)
- A key used to encrypt data.
- Key Encryption Key (KEK)
- A key used to encrypt, or wrap, a DEK.
- All Cloud KMS platform options (software, hardware, and external backends) allow you to control KEK.
- KMS Master Key
- The key used to encrypt the KEK.
- This key is distributed in memory.
- KMS Master Key is backed up on hardware devices.
- Root KMS
- Google’s internal key management service.
Cloud KMS Locations
- Within a project, Cloud KMS resources can be created in one of many locations.
- A key’s location impacts the performance of applications using the key
- Regional
- data centers exist in a specific geographical place
- Dual-regional
- data centers exist in two specific geographical places.
- Multi-regional
- data centers are spread across a general geographical area
- Global
- special multi-region with its data centers spread throughout the world
- Reading and writing resources or associated metadata in dual-regional or multi-regional locations, including the
global location may be slower than reading or writing from a single region.
GCP Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- GCP services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- GCP exam questions are not updated to keep up the pace with GCP updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
References
Google_Cloud_Key_Management_Service_KMS
 Key
Key