AWS Network Firewall
- AWS Network Firewall is stateful, fully managed, network firewall and intrusion detection and prevention service (IDS/IPS) for VPCs.
- Network Firewall scales automatically with the network traffic, without the need for deploying and managing any infrastructure.
- AWS Network Firewall
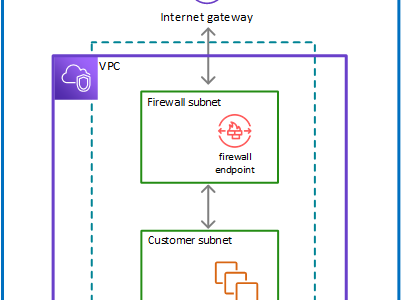
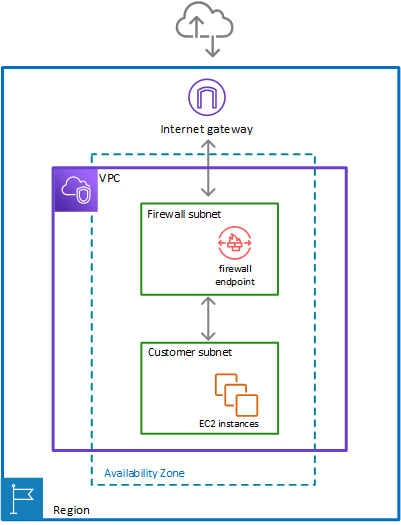
- can filter traffic at the perimeter of the VPC. This includes filtering traffic going to and coming from an internet gateway, NAT gateway, or over VPN or AWS Direct Connect.
- protects the subnets within the VPC by filtering traffic going between the subnets and locations outside of the VPC
- flexible rules engine allows defining firewall rules that give fine-grained control over network traffic, such as blocking outbound Server Message Block (SMB) requests to prevent the spread of malicious activity.
- supports importing rules already written in common open source rule formats as well as enables integrations with managed intelligence feeds sourced by AWS partners.
- works together with AWS Firewall Manager to build policies based on AWS Network Firewall rules and then centrally apply those policies across the VPCs and accounts.
- helps provide protection from common network threats.
- can incorporate context from traffic flows, like tracking connections and protocol identification, to enforce policies such as preventing the VPCs from accessing domains using an unauthorized protocol.
- supports intrusion prevention system (IPS) to provide active traffic flow inspection to help identify and block vulnerability exploits using signature-based detection.
- uses the open source intrusion prevention system (IPS), Suricata, for stateful inspection and supports Suricata compatible rules.
- supports web filtering that can stop traffic to known bad URLs and monitor fully qualified domain names.
AWS Network Firewall Components
- Rule Group
- Holds a reusable collection of criteria for inspecting traffic and for handling packets and traffic flows that match the inspection criteria.
- Rule groups are either stateless or stateful.
- Rules configuration includes 5-tuple and domain name filtering.
- Firewall policy
- Defines a reusable set of stateless and stateful rule groups, along with some policy-level behaviour settings.
- Firewall policy provides the network traffic filtering behaviour for a firewall.
- A single firewall policy can be used in multiple firewalls.
- Firewall
- Connects the inspection rules in the firewall policy to the VPC that the rules protect.
- Each firewall requires one firewall policy.
- The firewall additionally defines settings like how to log information about the network traffic and the firewall’s stateful traffic filtering.
Stateless and Stateful Rules Engines
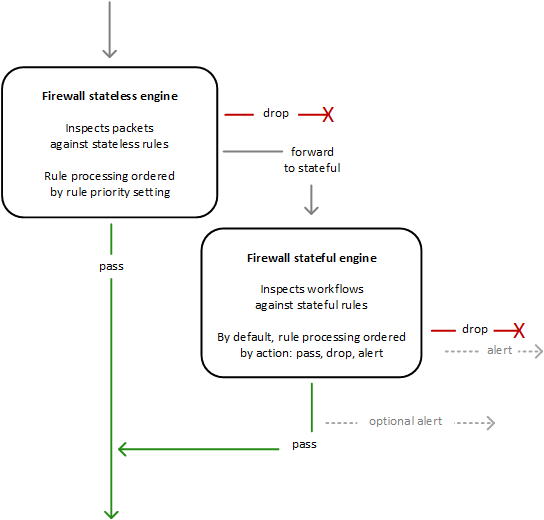
- AWS Network Firewall uses two rules engines to inspect packets according to the rules that you provide in your firewall policy.
- Stateless Rules Engine
- First, the Stateless engine inspects the packet against the configured stateless rules.
- Each packet inspection happens in isolation, without regard to factors such as the direction of traffic, or whether the packet is part of an existing, approved connection.
- This engine prioritizes the speed of evaluation and it takes rules with standard 5-tuple connection criteria.
- The engine processes the rules in the defined priority order and stops processing when it finds a match.
- Network Firewall stateless rules are similar in behaviour and use to VPC network access control lists (ACLs).
- Depending on the packet settings, the stateless inspection criteria, and the firewall policy settings, the stateless engine might
- drop a packet,
- pass it through to its destination, or
- forward it to the stateful rules engine.
- Stateful Rules Engine
- Stateful engine inspects packets in the context of their traffic flow, using the configured stateful rules.
- Packets are inspected in the context of their traffic flow.
- Stateful rules consider traffic direction. The stateful rules engine might delay packet delivery in order to group packets for inspection.
- By default, the stateful rules engine processes the rules in the order of their action setting, with pass rules processed first, then drop, and then alert. The engine stops processing when it finds a match.
- The stateful engine either
- drops packets or
- passes them to their destination.
- Stateful engine activities send flow and alert logs to the firewall’s logs if logging is configured.
- Stateful engine sends alerts for dropped packets and can optionally send them for passed packets.
- Stateful rules are similar in behaviour and use to VPC security groups.
- By default, the stateful rules engine allows traffic to pass, while the security groups default is to deny traffic.
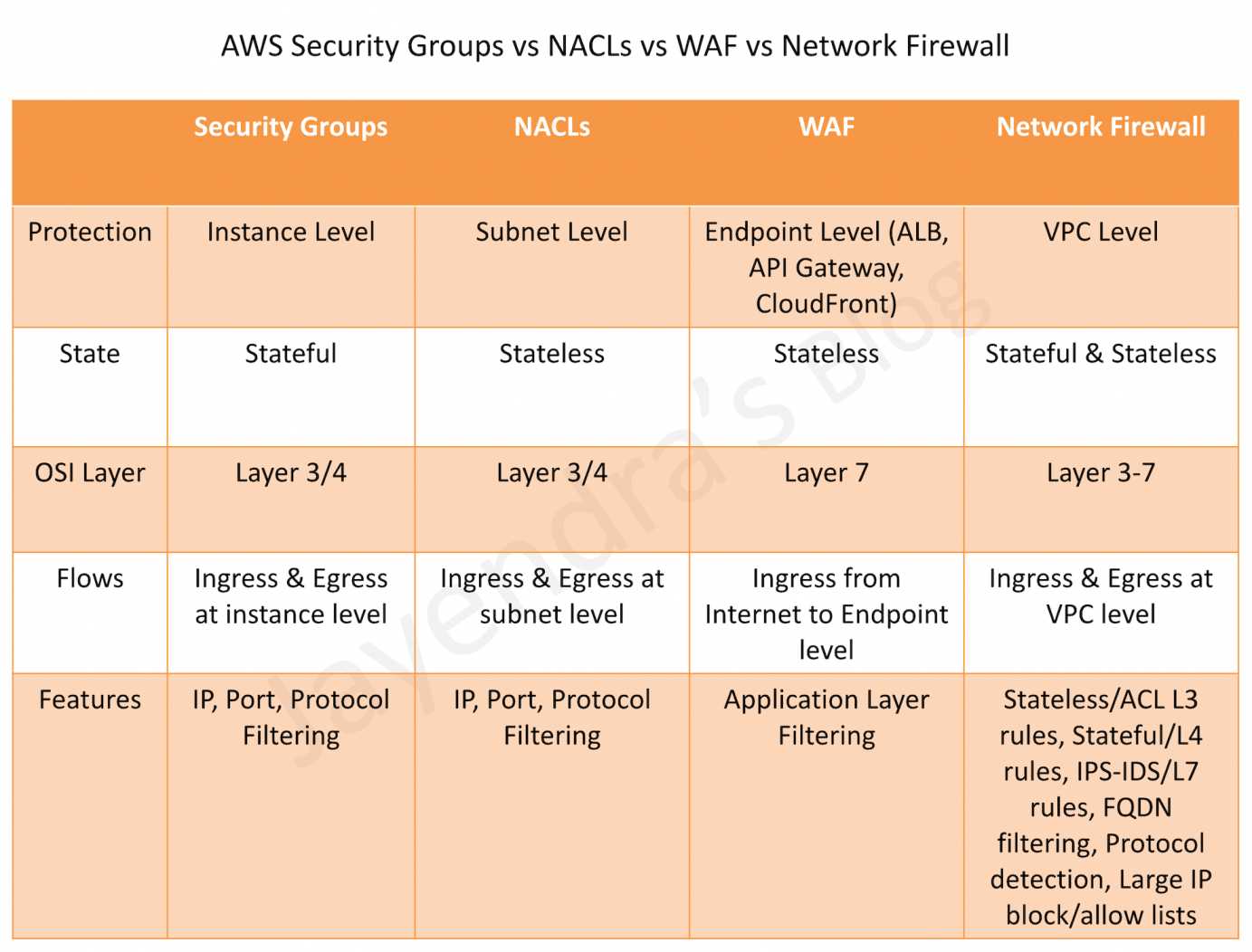
AWS Network Firewall vs WAF vs Security Groups vs NACLs
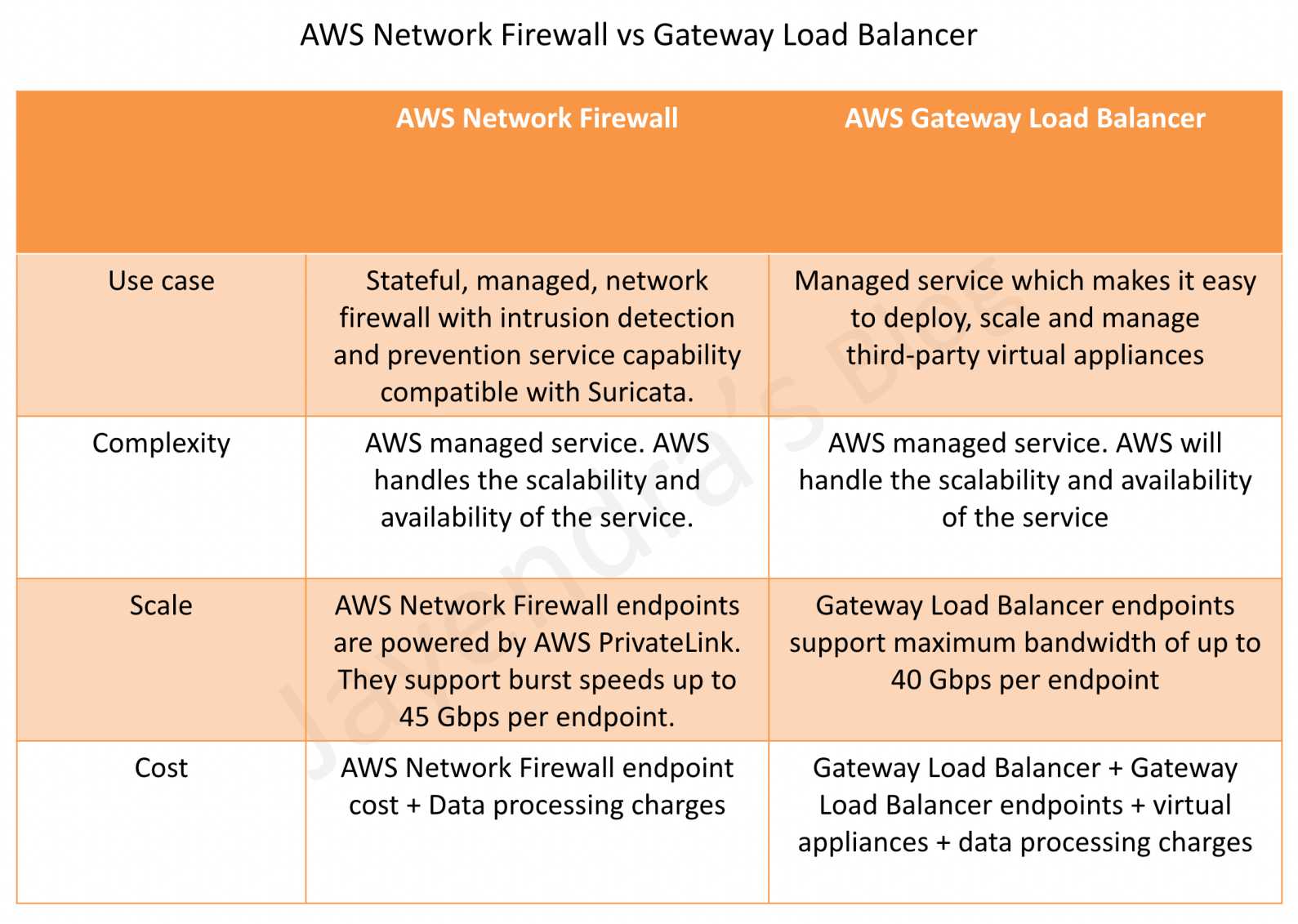
AWS Network Firewall vs Gateway Load Balancer
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.