AWS Network Firewall vs Gateway Load Balancer
AWS Network Firewall
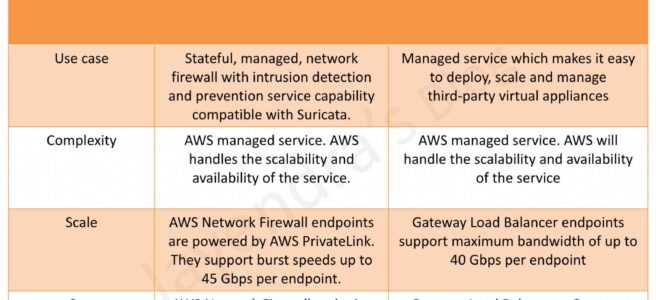
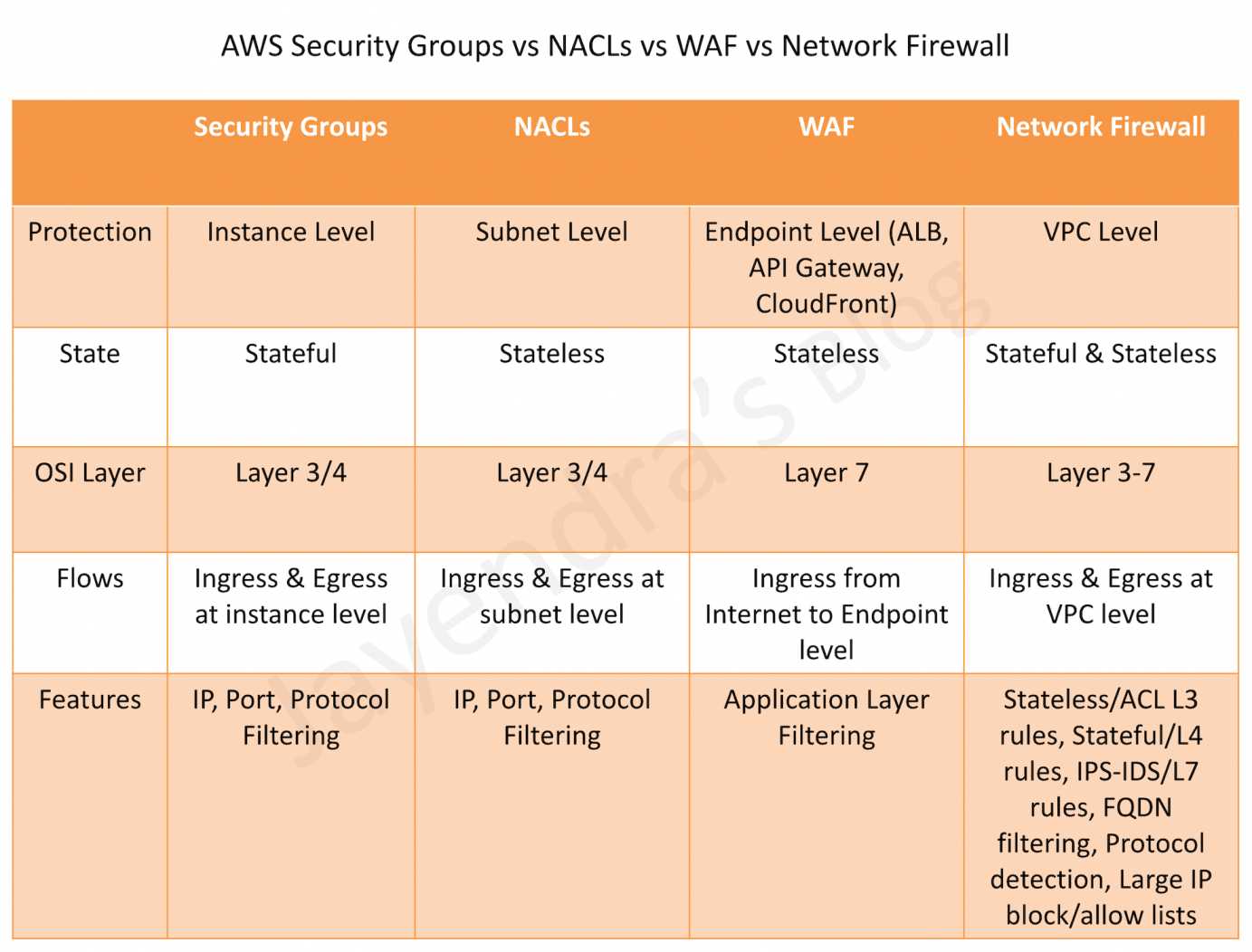
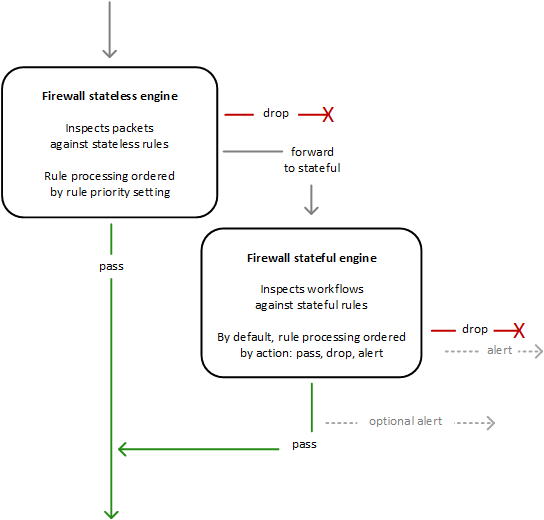
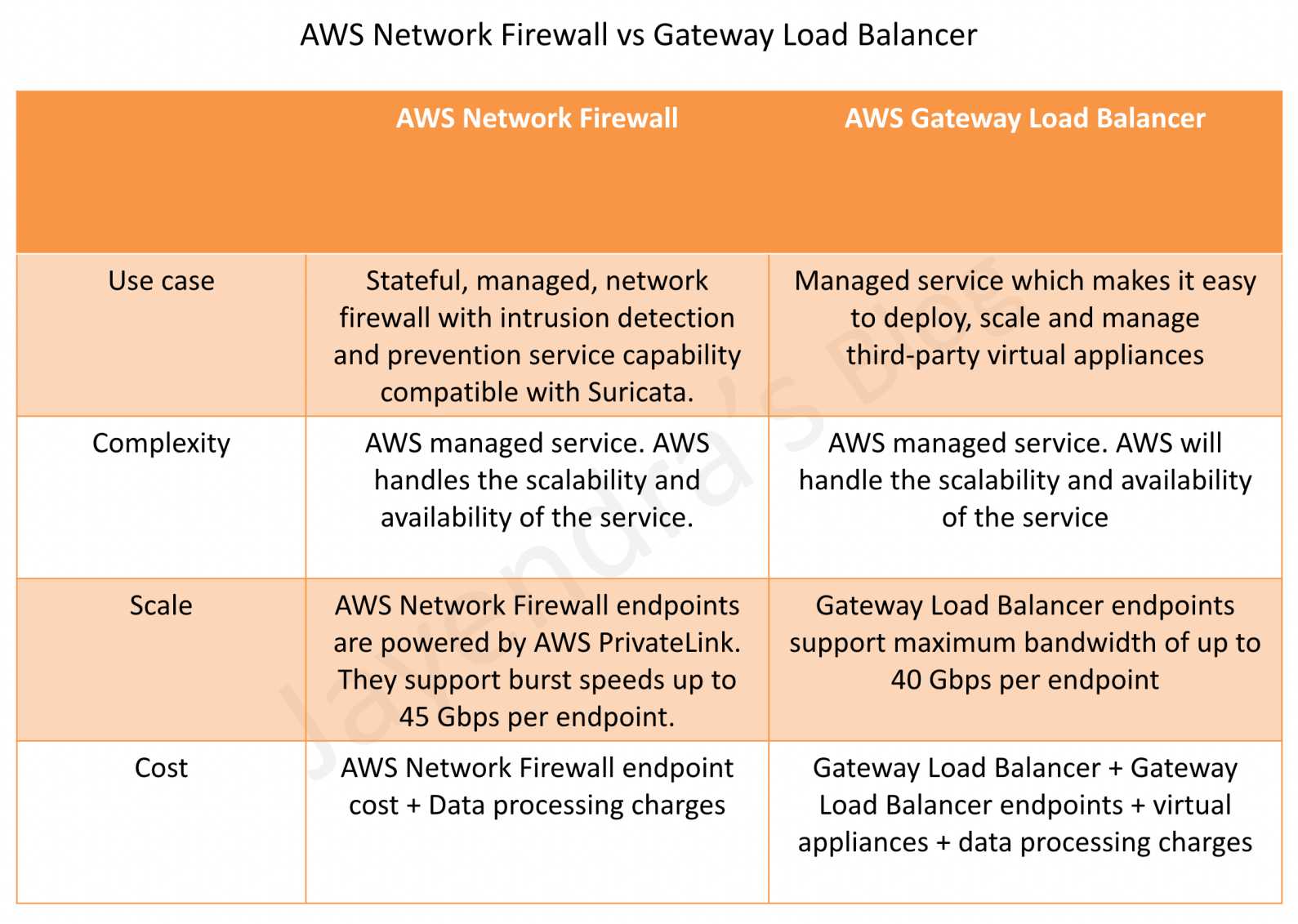
- AWS Network Firewall is a stateful, fully managed, network firewall and intrusion detection and prevention service (IDS/IPS) for VPCs.
- Network Firewall scales automatically with the network traffic, without the need for deploying and managing any infrastructure.
- AWS Network Firewall cost covers
- an hourly rate for each firewall endpoint,
- the amount of traffic and data processing charges, billed by the gigabyte, processed by the firewall endpoint,
- standard AWS data transfer charges for all data transferred via the AWS Network Firewall.
AWS Gateway Load Balancer
- Gateway Load Balancer helps deploy, scale, and manage virtual appliances, such as firewalls, intrusion detection and prevention systems (IDS/IPS), and deep packet inspection systems.
- is architected to handle millions of requests/second, volatile traffic patterns, and introduces extremely low latency.
- AWS Gateway Load Balancer cost covers
- charges for each hour or partial hour that a GWLB is running,
- the number of Gateway Load Balancer Capacity Units (GLCU) used by Gateway Load Balancer per hour.
- GWLB uses Gateway Load Balancer Endpoint (GWLBE) to simplify how applications can securely exchange traffic with GWLB across VPC boundaries. GWLBE is priced and billed separately.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.