Amazon Cognito
- Amazon Cognito provides authentication, authorization, and user management for the web and mobile apps.
- Users can sign in directly with a username and password, or through a third party such as Facebook, Amazon, Google, or Apple.
- Cognito has two main components.
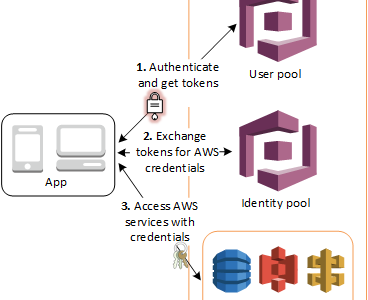
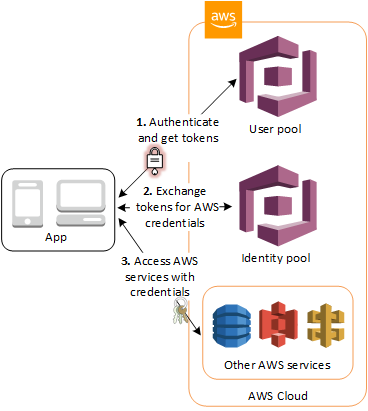
- User pools are user directories that provide sign-up and sign-in options for the app users.
- Identity pools enable you to grant the users access to other AWS services.
- Cognito Sync helps synchronize data across a user’s devices so that their app experience remains consistent when they switch between devices or upgrade to a new device.
Cognito User Pools
- User pools are for authentication (identity verification).
- User pools are user directories that provide sign-up and sign-in options for web and mobile app users.
- User pool helps users sign in to the web or mobile app, or federate through a third-party identity provider (IdP).
- All user pool members have a directory profile, whether the users sign in directly or through a third party, that can be accessed through an SDK.
- After successfully authenticating a user, Cognito issues JSON web tokens (JWT) that can be used to secure and authorize access to your own APIs, or exchange for AWS credentials.
- User pools provide:
- Sign-up and sign-in services.
- A built-in, customizable web UI to sign in users.
- Social sign-in with Facebook, Google, Apple, or Amazon, and through SAML and OIDC identity providers from the user pool.
- User directory management and user profiles.
- Security features such as MFA, checks for compromised credentials, account takeover protection, and phone and email verification.
- Customized workflows and user migration through Lambda triggers.
- Use cases
- Design sign-up and sign-in webpages for your app.
- Access and manage user data.
- Track user device, location, and IP address, and adapt to sign-in requests of different risk levels.
- Use a custom authentication flow for your app.
Cognito Identity Pools
- Identity pools are for authorization (access control).
- Identity pool helps users obtain temporary AWS credentials to access AWS services,
- Identity pools support both authenticated and unauthenticated identities.
- Unauthenticated identities typically belong to guest users.
- Authenticated identities belong to users who are authenticated by any supported identity provider:
- Cognito user pools
- Social sign-in with Facebook, Google, Login with Amazon, and Sign in with Apple
- OpenID Connect (OIDC) providers
- SAML identity providers
- Developer authenticated identities
- Each identity type has a role with policies assigned that determines the AWS services that the role can access.
- Identity Pools do not store any user profiles.
- Use cases
Cognito Sync
- Cognito Sync is an AWS service and client library that makes it possible to sync application-related user data across devices.
- Cognito Sync can synchronize user profile data across mobile devices and the web without using your own backend.
- The client libraries cache data locally so that the app can read and write data regardless of device connectivity status.
- When the device is online, the data can be synchronized.
- If you set up push sync, other devices can be notified immediately that an update is available.
- Sync store is a key/value pair store linked to an identity.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A company is building a social media mobile and web app for consumers. They want the application to be available on all desktop and mobile platforms, while being able to maintain user preferences across platforms. How can they implement the authentication to support the requirement?
- Use AWS Cognito
- Use AWS Glue
- Use Web Identity Federation
- Use AWS IAM
- A Developer needs to create an application that supports Security Assertion Markup Language (SAML) and Facebook authentication. It must also allow access to AWS services, such as Amazon DynamoDB. Which AWS service or feature will meet these requirements with the LEAST amount of additional coding?
- AWS AppSync
- Amazon Cognito identity pools
- Amazon Cognito user pools
- Amazon Lambda@Edge
- A development team is designing a mobile app that requires multi-factor authentication. Which steps should be taken to achieve this? (Choose two.)
- Use Amazon Cognito to create a user pool and create users in the user pool.
- Send multi-factor authentication text codes to users with the Amazon SNS Publish API call in the app code.
- Enable multi-factor authentication for the Amazon Cognito user pool.
- Use AWS IAM to create IAM users.
- Enable multi-factor authentication for the users created in AWS IAM.
- A Developer is building a mobile application and needs any update to user profile data to be pushed to all devices accessing the specific identity. The Developer does not want to manage a back end to maintain the user profile data. What is the MOST efficient way for the Developer to achieve these requirements using Amazon Cognito?
- Use Cognito federated identities.
- Use a Cognito user pool.
- Use Cognito Sync.
- Use Cognito events.