AWS Intrusion Detection & Prevention System IDS/IPS
- An Intrusion Prevention System IPS
- is an appliance that monitors and analyzes network traffic to detect malicious patterns and potentially harmful packets and prevent vulnerability exploits
- Most IPS offer firewall, unified threat management and routing capabilities
- An Intrusion Detection System IDS is
- an appliance or capability that continuously monitors the environment
- sends alerts when it detects malicious activity, policy violations or network & system attack from someone attempting to break into or compromise the system
- produces reports for analysis.
Approaches for AWS IDS/IPS
Network Tap or SPAN
- Traditional approach involves using a network Test Access Point (TAP) or Switch Port Analyzer (SPAN) to access & monitor all network traffic.
- Connection between the AWS Internet Gateway (IGW) and the Elastic Load Balancer would be an ideal place to capture all network traffic.
- However, there is no place to plug this in between IGW and ELB as there are no SPAN ports, network taps, or a concept of Layer 2 bridging
Packet Sniffing
- It is not possible for a virtual instance running in promiscuous mode to receive or sniff traffic that is intended for a different virtual instance.
- While interfaces can be placed into promiscuous mode, the hypervisor will not deliver any traffic to an instance that is not addressed to it.
- Even two virtual instances that are owned by the same customer located on the same physical host cannot listen to each other’s traffic
- So, promiscuous mode is not allowed
Host Based Firewall – Forward Deployed IDS
- Deploy a network-based IDS on every instance you deploy IDS workload scales with your infrastructure
- Host-based security software works well with highly distributed and scalable application architectures because network packet inspection is distributed across the entire software fleet
- However, CPU-intensive process is deployed onto every single machine.
Host Based Firewall – Traffic Replication
- An Agent is deployed on every instance to capture & replicate traffic for centralized analysis
- Actual workload of network traffic analysis is not performed on the instance but on a separate server
- Traffic capture and replication is still CPU-intensive (particularly on Windows machines.)
- It significantly increases the internal network traffic in the environment as every inbound packet is duplicated in the transfer from the instance that captures the traffic to the instance that analyzes the traffic
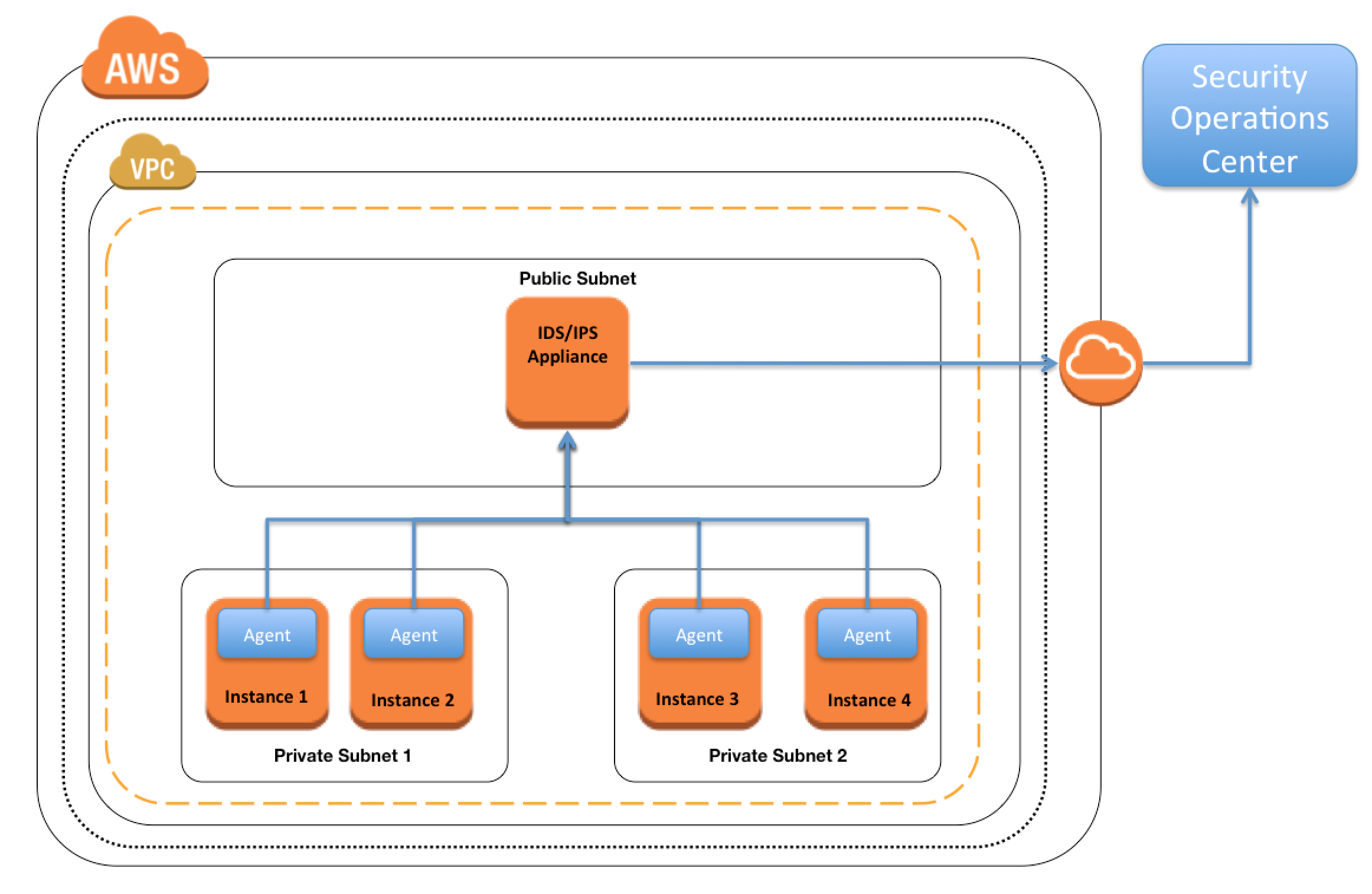
In-Line Firewall – Inbound IDS Tier
- Add another tier to the application architecture where a load balancer sends all inbound traffic to a tier of instances that performs the network analysis for e.g. Third Party Solution Fortinet FortiGate
- IDS workload is now isolated to a horizontally scalable tier in the architecture You have to maintain and manage another mission-critical elastic tier in the architecture
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A web company is looking to implement an intrusion detection and prevention system into their deployed VPC. This platform should have the ability to scale to thousands of instances running inside of the VPC. How should they architect their solution to achieve these goals?
- Configure an instance with monitoring software and the elastic network interface (ENI) set to promiscuous mode packet sniffing to see an traffic across the VPC. (virtual instance running in promiscuous mode to receive or“sniff” traffic)
- Create a second VPC and route all traffic from the primary application VPC through the second VPC where the scalable virtualized IDS/IPS platform resides.
- Configure servers running in the VPC using the host-based ‘route’ commands to send all traffic through the platform to a scalable virtualized IDS/IPS (host based routing is not allowed)
- Configure each host with an agent that collects all network traffic and sends that traffic to the IDS/IPS platform for inspection.
- You are designing an intrusion detection prevention (IDS/IPS) solution for a customer web application in a single VPC. You are considering the options for implementing IDS/IPS protection for traffic coming from the Internet. Which of the following options would you consider? (Choose 2 answers)
- Implement IDS/IPS agents on each Instance running In VPC
- Configure an instance in each subnet to switch its network interface card to promiscuous mode and analyze network traffic. (virtual instance running in promiscuous mode to receive or“sniff” traffic)
- Implement Elastic Load Balancing with SSL listeners In front of the web applications (ELB with SSL does not serve as IDS/IPS)
- Implement a reverse proxy layer in front of web servers and configure IDS/IPS agents on each reverse proxy server
Hello Jayendra, can you please explain wht you meant by “host base routing is not allowed” below?
c.Configure servers running in the VPC using the host-based ‘route’ commands to send all traffic through the platform to a scalable virtualized IDS/IPS (host based routing is not allowed)
This is no facility for the route commands which will allow to route traffic based on the host, hence the option is invalid.
Hi Jayendra,
For my curiosity in question # 2 why you are not considering option B. here is the explanation for the B.
B. Correct – IDS/IPS often involves listening to traffic. However the design proposed in B. Is out of date. It would work if you have Hubs, but not a Switch. If you want to listen to all traffic you need to listen to a specially configured port on the Switch.
(referring from the https://acloud.guru/forums/aws-certified-solutions-architect-professional/discussion/-K9w2aAi48d3nQKqEI0S/valid-idsips-to-protect-internet-traffic-to-a-web-server-in-vpc)
Frankly speaking, i haven’t found any material or videos from AWS mentioning the listening part old or new in promiscuous mode, which is basically not allowed.
The other 2 selected are the only legal way to implement it.
Hi Jayendra,
I see quite some discussion about the answer#b of question#1 ,would you pls kindly provide some advices on why the answer#b is not correct?thanks!
b.Create a second VPC and route all traffic from the primary application VPC through the second VPC where the scalable virtualized IDS/IPS platform resides.
Frankly I haven’t seen a solution that works with the traffic being passed from one VPC to another. With agents being installed is how all the third party solutions offering IDS/IPS work. However, I was not able to find any documentation as well which says for sure it doesn’t work.
Hi Jayendra,
Thank you very much for your effort in building up the list of AWS services and tips for my ASA Pro study, which is best study material I’ve ever found.
For the Q1-B, I think it’s doable. One of my customers is using this architecture, a dedicated Ingress/Engress VPC to handle the public traffices with WAF and IDS/IPS deployed in the VPC.
Thanks and Thats Great EddMt. Can you share the technical details, i have been trying to check on that option but never got a chance to implement or see it being implemented as well.
Hi.
Why is not D? – Question asks to to implement an intrusion detection and PREVENTION system. Agent collecting trafifc can’t prevent attacks, it can only DETECT.
Why is B? – IPS systems can proxy traffic. It can sends traffic to the end platform with their own IP address as a source (proxing traffic), avoiding “transit VPC peering” issue. but in reality I didn’t see a scalable IDS/IPS system.
I think question is wrong.
Q1 – I think the answer should be “B”.
A is out, promiscuous mode is not allowed in AWS.
C and D are similar in concept, just different wording.
C is out, intrusion traffic would already hit the servers and would need to deploy routing on servers [configure each host] to send traffic to the IDS/.IPS platfrom.
D is similar to C, intrusion traffic would already hit the servers and having to configure each servers [with an agent] to send (route) traffic to the IDS/IPS platform.
B – The second VPC would act as a front-line IDS/IPS (scalable). It analyzes and filters traffic before malicious traffic hit the servers in the primary VPC. Technology wise, it would be similar to a firewall (IDS/IPS) at the point of traffic entry to the corporate network.
It may work as WAF, but within the VPC. But haven’t seen any solution being implemented with 2 VPCs. If you find a reference, can you please let me know.
Hi,
Is this for CSAA ?
Regards.
yup better to know, i recollect an IDS/IPS question in the old CSAA exam.