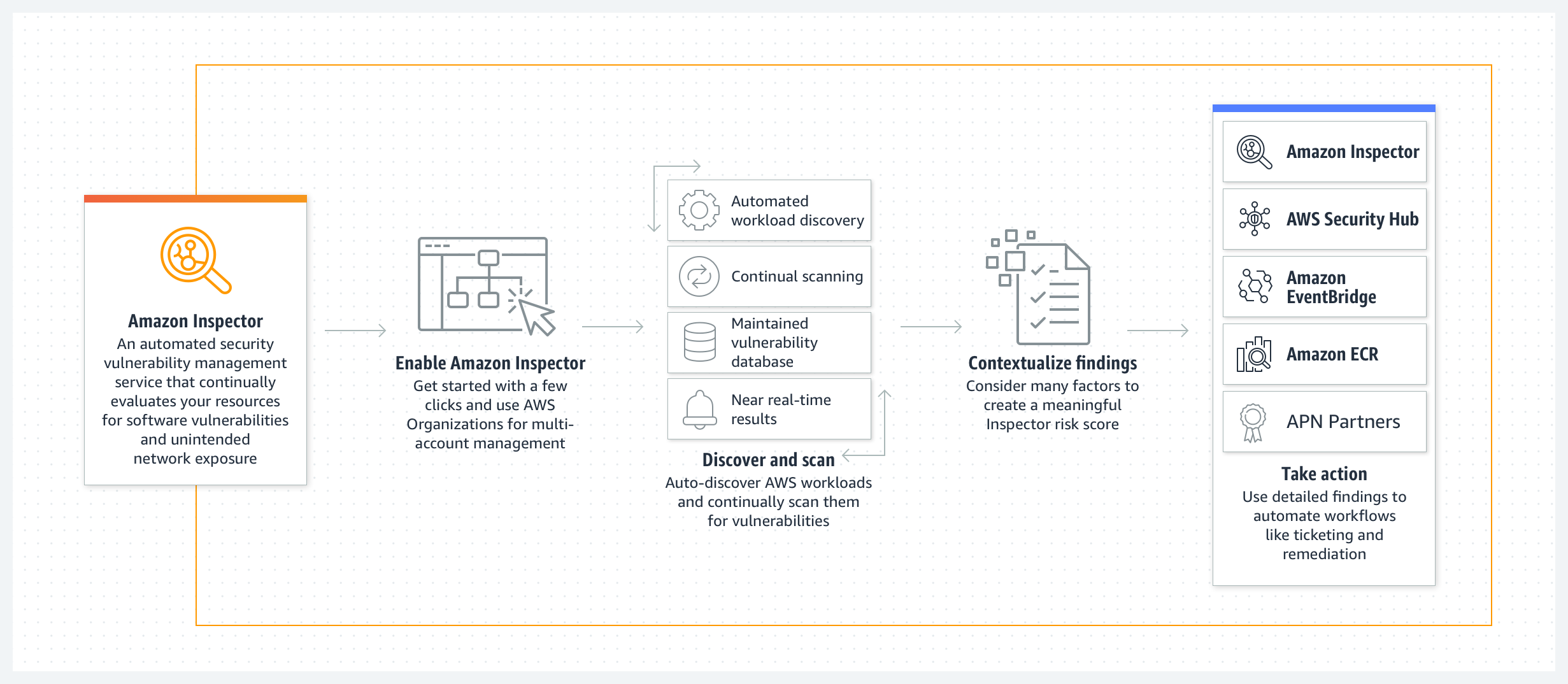
Amazon Inspector
- Amazon Inspector is a vulnerability management service that continuously scans the AWS workloads for vulnerabilities.
- automatically discovers and scans EC2 instances and container images in ECR for software vulnerabilities and unintended network exposure.
- creates a finding, when a software vulnerability or network issue is discovered, that describes the vulnerability, rates its severity, identifies the affected resource and provides remediation guidance.
- is a Regional service and configurations needs to be repeated across each region.
- requires Systems Manager (SSM) agent to be installed and activated for Common Vulnerabilities and Exposures (CVE) data.
- SSM agents can be set up as VPC Interface endpoints to avoid sending any information over the internet.
- uses an IAM
AWSServiceRoleForAmazonInspector2service-linked-role linked directly to Inspector with all the permissions required to call other AWS services on your behalf. - has multi-account management through AWS Organizations integration, which allows delegating an administrator account for the organization.
- integrates with AWS Security Hub which collects and centralizes the security data from across the AWS accounts, services, and other supported products to assess the security state of the environment according to industry standards and best practices.
AWS Inspector Features
- Continuously scan environments for vulnerabilities and network exposure
- automatically discovers and begins scanning the eligible resources without the need to manually schedule or configure assessment scans.
- Assess vulnerabilities accurately with the Inspector Risk score
- Inspector collects information about the environment through scans, it provides severity scores specifically tailored to the environment.
- Identify high-impact findings with the Inspector dashboard
- The dashboard offers a high-level view of findings from across your environment.
- Manage your findings using customizable views
- Inspector console offers a Findings view
- Users can use filters and suppression rules to generate customized finding reports
- Monitor and process findings with other services and systems
Inspector Finding Types
- Package Vulnerability
- Package vulnerability findings identify software packages in the environment that are exposed to common vulnerabilities and exposures (CVEs).
- Package vulnerability findings are generated for both EC2 instances, ECR container images and Lambda functions.
- Network Vulnerability
- Network reachability findings indicate that there are allowed network paths to EC2 instances in the environment.
- Network reachability findings are only generated for EC2 resources.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Which of the following services allows you to analyze EC2 Instances against pre-defined security templates to check for vulnerabilities?
- AWS Trusted Advisor
- AWS Inspector
- AWS WAF
- AWS Shield
- Your company has a set of AWS resources which consists of EC2 Instances. The Security departments need to run vulnerability analysis on these machines to ensure that the Instances comply with the latest security standards. Which of the following would you implement for this requirement?
- AWS WAF
- AWS Snowball
- AWS CloudFront
- AWS Inspector