AWS Transit Gateway – TGW
- AWS Transit Gateway – TGW is a highly available and scalable service to consolidate the AWS VPC routing configuration for a region with a hub-and-spoke architecture.
- acts as a Regional virtual router and is a network transit hub that can be used to interconnect VPCs and on-premises networks.
- traffic always stays on the global AWS backbone, data is automatically encrypted, and never traverses the public internet, thereby reducing threat vectors, such as common exploits and DDoS attacks.
- is a Regional resource and can connect VPCs within the same AWS Region.
- TGWs across different regions can peer with each other to enable VPC communications across regions.
- Each spoke VPC only needs to connect to the TGW to gain access to other connected VPCs.
- provides simpler VPC-to-VPC communication management over VPC Peering with a large number of VPCs.
- scales elastically based on the volume of network traffic.
- TGW routing operates at layer 3, where the packets are sent to a specific next-hop attachment, based on their destination IP addresses.
- AWS Resource Access Manager – RAM can be used to share the TGW with other accounts.
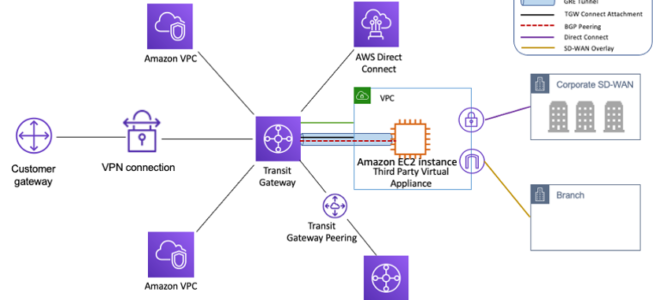
Transit Gateway Attachments
- Transit Gateway attachment is the connection between resources like VPC, VPN, Direct Connect, and the TGW.
- YGW attachment is both a source and a destination of packets.
- TGW supports the following attachments
- One or more VPCs
- One or more VPN connections
- One or more AWS Direct Connect Gateways
- One or more Transit Gateway Connect attachments
- One or more Transit Gateway peering connections
- One of more Connect SD-WAN/third-party network appliance
Transit Gateway Routing
- Transit Gateway routes IPv4 and IPv6 packets between attachments using transit gateway route tables.
- Route tables can be configured to propagate routes from the route tables for the attached VPCs, VPN connections, and Direct Connect gateways.
- When a packet comes from one attachment, it is routed to another attachment using the route that matches the destination IP address.
- VPC attached to a TGW must be added a route to the subnet route table in order for traffic to route through the TGW.
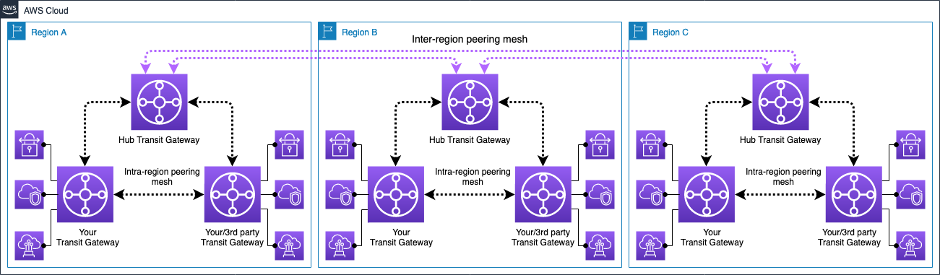
Transit Gateway Peering
- Transit Gateway supports the ability to establish peering connections between TGWs in the same and different AWS Regions.
- Inter-region Transit Gateway peering
- enables customers to extend this connectivity and build global networks spanning multiple AWS Regions.
- simplifies routing and inter-connectivity between VPCs and on-premises networks that are serviced and managed via separate TGWs
- encrypts inter-region traffic with no single point of failure.
- ensures the traffic always stays on the AWS global network and never traverses the public internet, thereby reducing threat vectors, such as common exploits and DDoS attacks.
Transit Gateway High Availability
- Transit Gateway must be enabled with multiple AZs to ensure availability and to route traffic to the resources in the VPC subnets.
- AZ can be enabled by specifying exactly one subnet within the AZ
- TGW places a network interface in that subnet using one IP address from the subnet.
- TGW can route traffic to all the subnets and not just the specified subnet within the enabled AZ.
- Resources that reside in AZs where there is no TGW attachment cannot reach the TGW.
Transit Gateway Appliance Mode
- For stateful network appliances in the VPC, appliance mode support for the VPC attachment can be enabled in which the appliance is located.
- Appliance Mode ensures that network flows are symmetrically routed to the same AZ and network appliance
- Appliance Mode ensures that the same AZ for that VPC attachment is used for the lifetime of a flow of traffic between source and destination.
- Appliance Mode also allows the TGW to send traffic to any AZ in the VPC, as long as there is a subnet association in that zone.
Transit Gateway Connect Attachment
- Transit Gateway Connect attachment can help establish a connection between a TGW and third-party virtual appliances (such as SD-WAN appliances) running in a VPC.
- A Connect attachment supports the Generic Routing Encapsulation (GRE) tunnel protocol for high performance and Border Gateway Protocol (BGP) for dynamic routing.
Transit Gateway Network Manager
- AWS Transit Gateway Network Manager provides a single global view of the private network.
- includes events and metrics to monitor the quality of the global network, both in AWS and on-premises.
- Event alerts specify changes in the topology, routing, and connection status. Usage metrics provide information on up/down connection, bytes in/out, packets in/out, and packets dropped.
- seamlessly integrates with SD-WAN solutions
Transit Gateway Best Practices
- Use a separate subnet for each transit gateway VPC attachment.
- Create one network ACL and associate it with all of the subnets that are associated with the TGW. Keep the network ACL open in both the inbound and outbound directions.
- Associate the same VPC route table with all of the subnets that are associated with the YGW, unless your network design requires multiple VPC route tables (for example, a middle-box VPC that routes traffic through multiple NAT gateways).
- Use BGP Site-to-Site VPN connections, if the customer gateway device or firewall for the connection supports multipath, enable the feature.
- Enable route propagation for AWS Direct Connect gateway attachments and BGP Site-to-Site VPN attachments.
- are highly available by design and do not need additional TGWs for high availability,
- Limit the number of TGW route tables unless the design requires multiple TGW route tables.
- For redundancy, use a single TGW in each Region for disaster recovery.
- For deployments with multiple TGWs, it is recommended to use a unique ASN for each of them.
- supports intra-Region peering.
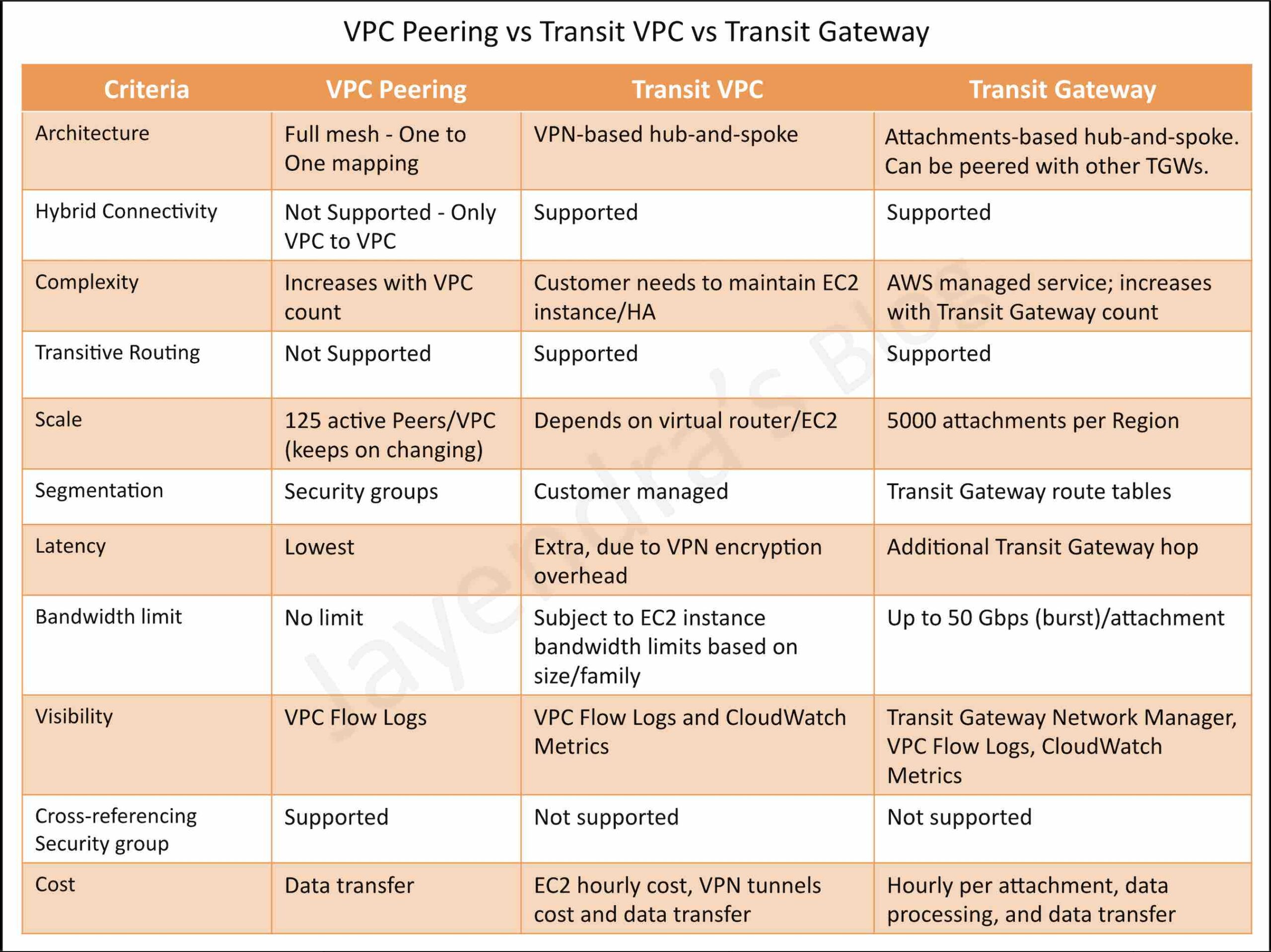
Transit Gateway vs Transit VPC vs VPC Peering
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A company is using a VPC peering strategy to connect its VPCs in a single Region to allow for cross-communication. A recent increase in account creations and VPCs has made it difficult to maintain the VPC peering strategy, and the company expects to grow to hundreds of VPCs. There are also new requests to create site-to-site VPNs with some of the VPCs.
A solutions architect has been tasked with creating a centrally managed networking setup for multiple accounts, VPCs, and VPNs.Which networking solution meets these requirements?- Configure shared VPCs and VPNs and share with each other.
- Configure a hub-and-spoke VPC and route all traffic through VPC peering.
- Configure an AWS Direct Connect connection between all VPCs and VPNs.
- Configure a transit gateway with AWS Transit Gateway and connect all VPCs and VPNs
- A company hosts its core network services, including directory services and DNS, in its on-premises data center. The data center is connected to the AWS Cloud using AWS Direct Connect (DX). Additional AWS accounts are planned that will require quick, cost-effective, and consistent access to these network services. What should a solutions architect implement to meet these requirements with the LEAST amount of operational overhead?
- Create a DX connection in each new account. Route the network traffic to the on-premises servers.
- Configure VPC endpoints in the DX VPC for all required services. Route the network traffic to the on-premises servers.
- Create a VPN connection between each new account and the DX VPC. Route the network traffic to the on-premises servers.
- Configure AWS Transit Gateway between the accounts. Assign DX to the transit gateway and route network traffic to the on-premises servers.