Google Cloud VPN
- Cloud VPN securely connects your peer network to the Virtual Private Cloud (VPC) network through an IPsec VPN connection.
- Traffic traveling between the two networks is encrypted by one VPN gateway and then decrypted by the other VPN gateway.
- Cloud VPN protects the data as it travels over the internet.
- Two instances of Cloud VPN can also be connected to each other.
Cloud VPN Specifications
- only supports site-to-site IPsec VPN connectivity
- does not support client-to-gateway scenarios i.e. Cloud VPN doesn’t support use cases where client computers need to “dial in” to a VPN by using client VPN software.
- only supports IPsec. Other VPN technologies (such as SSL VPN) are not supported.
- can be used with Private Google Access for on-premises hosts
- Each Cloud VPN gateway must be connected to another Cloud VPN gateway or a peer VPN gateway.
- Peer VPN gateway must have a static external (internet routable) IPv4 address, needed to configure Cloud VPN.
- requires that the peer VPN gateway be configured to support prefragmentation. Packets must be fragmented before being encapsulated.
- Each Cloud VPN tunnel can support up to 3 Gbps total for ingress and egress
- Cloud VPN only supports a pre-shared key for authentication. Cloud VPN supports IKEv1 and IKEv2 by using an IKE pre-shared key (shared secret) and IKE ciphers.
Cloud VPN Components
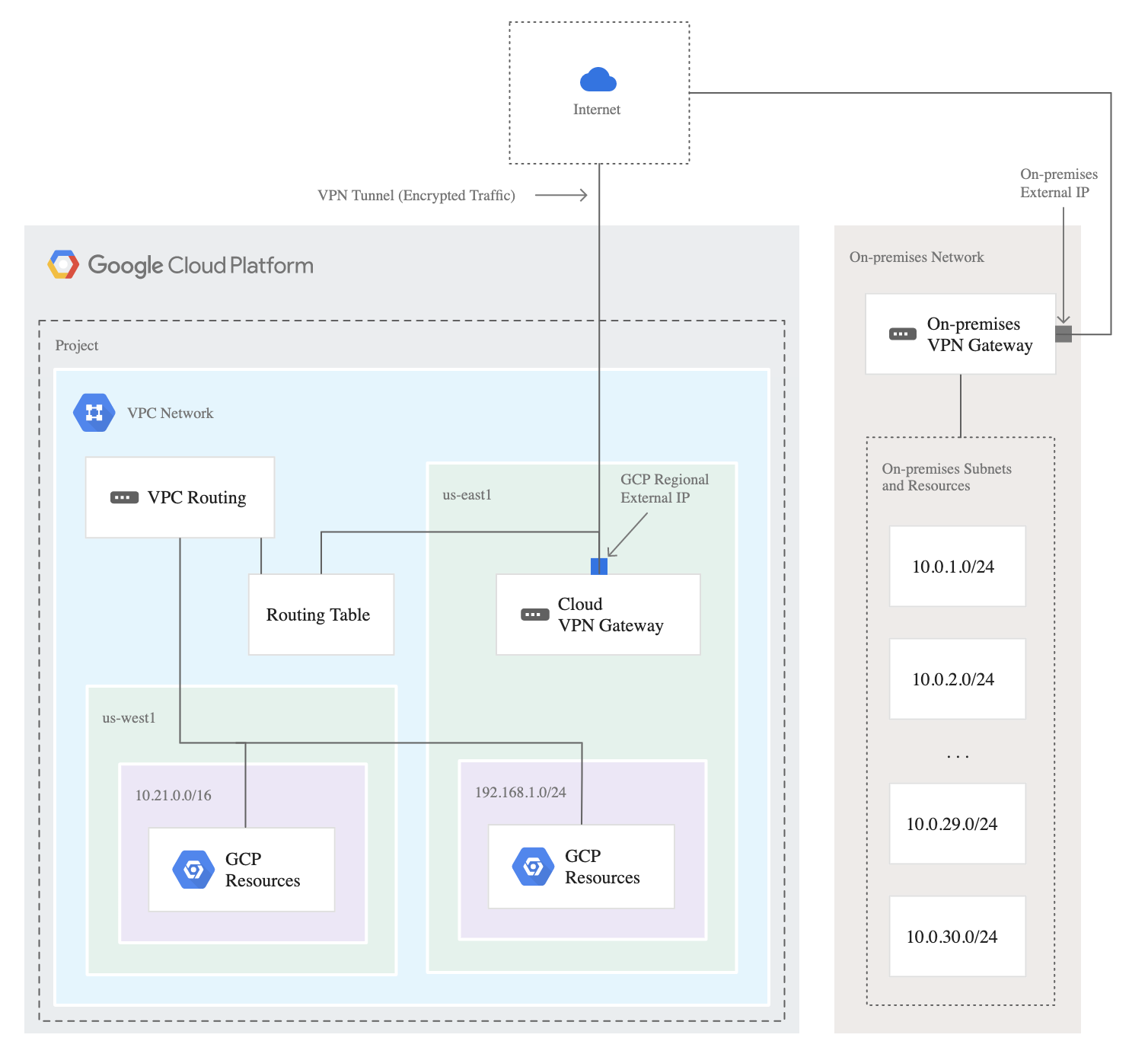
- Cloud VPN gateway
- A virtual VPN gateway running in Google Cloud managed by Google, using a specified configuration in the project, and used only by you.
- Each Cloud VPN gateway is a regional resource that uses one or more regional external IP addresses.
- A Cloud VPN gateway can connect to a peer VPN gateway.
- Peer VPN gateway
- A gateway that is connected to a Cloud VPN gateway.
- A peer VPN gateway can be one of the following:
- Another Cloud VPN gateway
- A VPN gateway hosted by another cloud provider such as AWS or Microsoft Azure
- An on-premises VPN device or VPN service
- External VPN gateway
- A gateway resource configured for HA VPN that provides information to Google Cloud about the peer VPN gateway or gateways.
- Remote peer IP address
- For an HA VPN gateway interface that connects to an external VPN gateway, the remote peer IP address is the IP address of the interface on the external VPN gateway that is used for the tunnel.
- VPN tunnel
- A VPN tunnel connects two VPN gateways and serves as a virtual medium through which encrypted traffic is passed.
- Internet Key Exchange (IKE)
- IKE is the protocol used for authentication and to negotiate a session key for encrypting traffic.
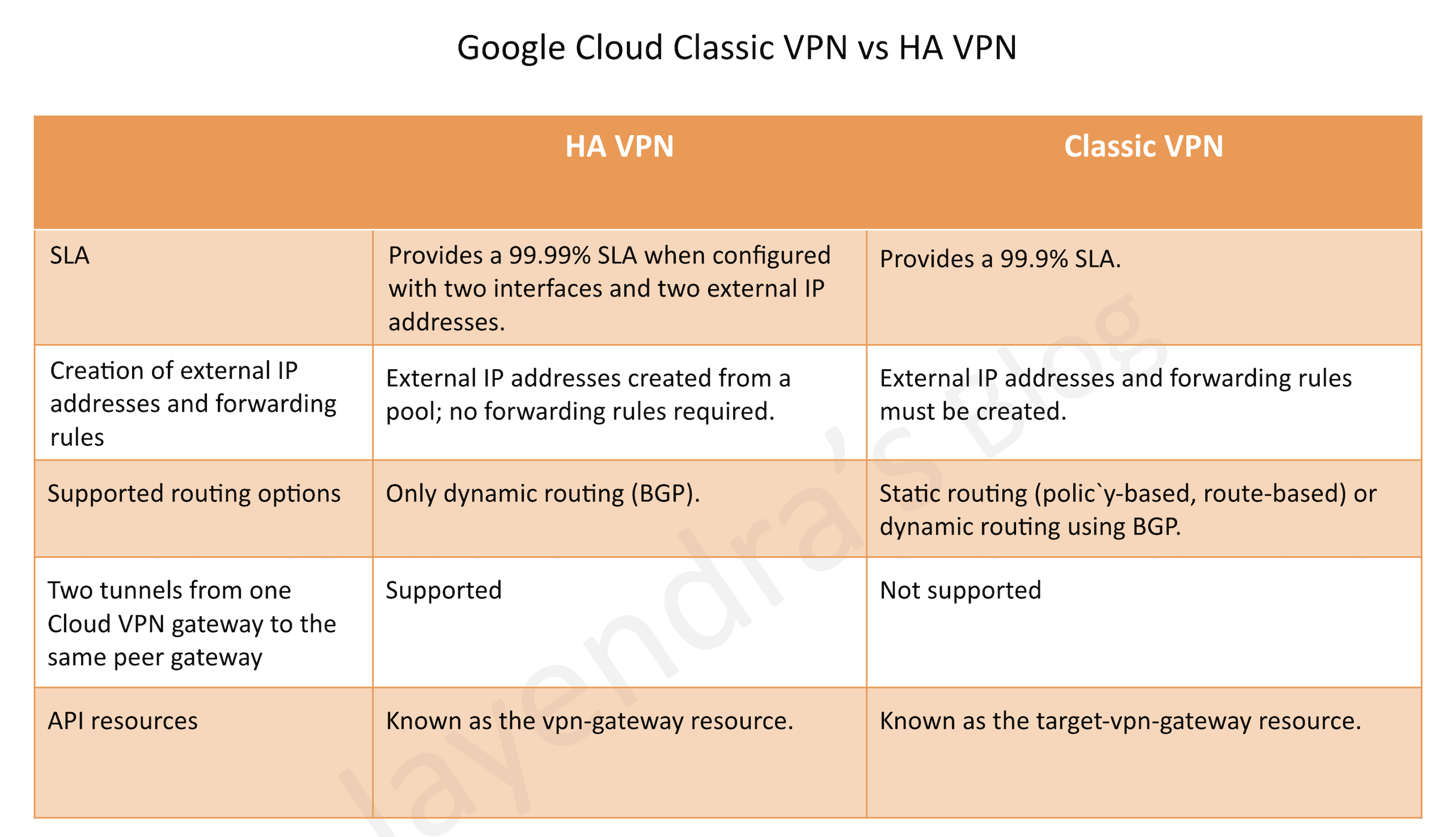
Classic VPN
- Classic VPN gateways have a single interface, a single external IP address, and support tunnels that use dynamic (BGP) or static routing (policy-based or route-based).
- Classic VPN provides an SLA of 99.9% service availability.
- Circa Oct 2021, Classic VPN would be deprecated
Cloud VPN HA
- Cloud VPN HA provides a highly available and secure connection between the on-premises and the VPC network through an IPsec VPN connection in a single region
- HA VPN provides an SLA of 99.99% service availability, when configured with two interfaces and two external IP addresses.
- Cloud VPN supports the creation of multiple HA VPN gateways and each of the HA VPN gateway interfaces supports multiple tunnels
- Peer VPN gateway device must support dynamic (BGP) routing.
- To achieve high availability when both VPN gateways are located in VPC networks, two HA VPN gateways must be used, and both of them must be located in the same region.
- Even though both gateways must be located in the same region, if the VPC network uses global dynamic routing mode, the routes to the subnets that the gateways share with each other can be located in any region

Active/Active vs Active/Passive Routing Options
- If a Cloud VPN tunnel goes down, it restarts automatically.
- If an entire virtual VPN device fails, Cloud VPN automatically instantiates a new one with the same configuration.
- The new gateway and tunnel connect automatically.
- Active/Active
- Effective aggregate throughput is the combined throughput of both tunnels.
- Peer gateway advertises the peer network’s routes with identical MED values for each tunnel.
- Egress traffic sent to the peer network uses equal-cost multipath (ECMP) routing.
- If one tunnel becomes unavailable, Cloud Router withdraws the learned custom dynamic routes whose next hops are the unavailable tunnel, which can take ~40 seconds
- Active/Passive
- Effective aggregate throughput is the individual throughput of each tunnel
- Peer gateway advertises the peer network’s routes with different MED values for each tunnel.
- Egress traffic sent to the peer network uses the route with the highest priority, as long as the associated tunnel is available.
- Peer gateway can only use the tunnel with the highest priority to send traffic to Google Cloud.
- If one tunnel becomes unavailable, Cloud Router withdraws the learned custom dynamic routes whose next hops are the unavailable tunnel, which can take ~40 seconds
- Google Cloud recommends
- Using Active/Passive configuration with a single HA VPN Gateway as the observed bandwidth capacity at the time of normal tunnel operation matches the bandwidth capacity observed during failover
- Using Active/Active configuration with multiple HA VPN Gateways as the observed bandwidth capacity at the time of normal tunnel operation is twice that of the guaranteed bandwidth capacity
Classic VPN vs HA VPN
GCP Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- GCP services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- GCP exam questions are not updated to keep up the pace with GCP updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Your company’s infrastructure is on-premises, but all machines are running at maximum capacity. You want to burst to Google
Cloud. The workloads on Google Cloud must be able to directly communicate to the workloads on-premises using a private IP
range. What should you do?- In Google Cloud, configure the VPC as a host for Shared VPC.
- In Google Cloud, configure the VPC for VPC Network Peering.
- Create bastion hosts both in your on-premises environment and on Google Cloud. Configure both as proxy servers using
their public IP addresses. - Set up Cloud VPN between the infrastructure on-premises and Google Cloud.
