AWS Client VPN
- AWS Client VPN is a managed client-based VPN service that enables secure access to AWS resources and resources in the on-premises network
- Client VPN allows accessing the resources from any location using an OpenVPN-based VPN client.
- Client VPN establishes a secure TLS connection from any location using the OpenVPN client.
- Client VPN automatically scales to the number of users connecting to the AWS resources and on-premises resources.
- Client VPN supports client authentication using Active Directory, federated authentication, and certificate-based authentication.
- Client VPN provides manageability with the ability to manage active client connections, with the ability to terminate active client connections and to view connection logs, which provide details on client connection attempts
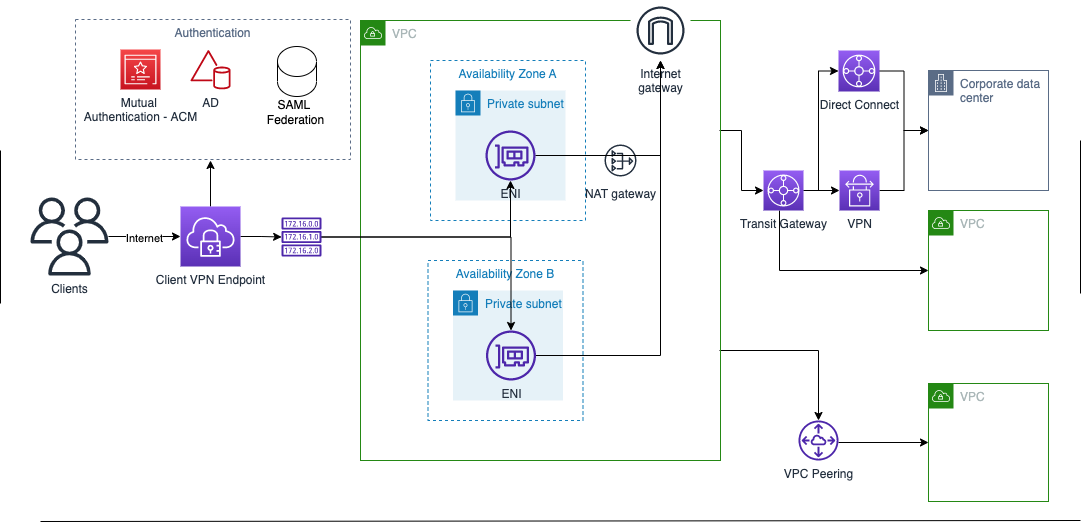
Client VPN Components
- Client VPN endpoint
- is the resource that is created and configured to enable and manage client VPN sessions.
- is the resource where all client VPN sessions are terminated.
- Target network
- is the network associated with a Client VPN endpoint.
- is a subnet from a VPC that enables establishing VPN sessions.
- Multiple subnets can be associated with the Client VPN endpoint, however, each subnet must belong to a different Availability Zone.
- Route
- describes the available destination network routes.
- Each route in the route table specifies the path for traffic to specific resources or networks.
- Authorization rules
- restrict the users who can access a network.
- helps configure the AD or IdP group that is allowed access. Only users belonging to this group can access the specified network.
- Client
- end-user connecting to the Client VPN endpoint to establish a VPN session.
- need to download an OpenVPN client and use the Client VPN configuration file to establish a VPN session.
Client VPN Authentication & Authorization
- Client VPN provides authentication and authorization capabilities.
- Authentication determines whether clients are allowed to connect to the Client VPN endpoint
- Client VPN offers the following types of client authentication:
- Active Directory authentication (user-based)
- Mutual authentication (certificate-based)
- Single sign-on (SAML-based federated authentication) (user-based)
- Client VPN supports two types of authorization:
- Security groups and
- Network-based authorization (using authorization rules)
- allows mapping of the Active Directory group or the SAML-based IdP group to the network they can have access to.
Client VPN Split Tunnel
- Client VPN endpoint, by default, routes all traffic over the VPN tunnel.
- Split-tunnel Client VPN endpoint helps when you do not want all user traffic to route through the Client VPN endpoint.
- Split tunnel ensures only traffic with a destination to the network matching a route from the Client VPN endpoint route table is routed over the Client VPN tunnel.
- Split-tunnel offers the following benefits:
- Optimized routing of traffic from clients by having only the AWS destined traffic traverse the VPN tunnel.
- Reduced volume of outgoing traffic from AWS, therefore reducing the data transfer cost.
Client VPN Limitations
- Client CIDR ranges cannot overlap with the local CIDR of the VPC in which the associated subnet is located, or any routes manually added to the Client VPN endpoint’s route table.
- Client CIDR ranges must have a block size between /22 and /12.
- Client CIDR range cannot be changed after Client VPN endpoint creation.
- Subnets associated with a Client VPN endpoint must be in the same VPC.
- Multiple subnets from the same AZ cannot be associated with a Client VPN endpoint.
- A Client VPN endpoint does not support subnet associations in a dedicated tenancy VPC.
- Client VPN supports IPv4 traffic only.
- Client VPN is not Federal Information Processing Standards (FIPS) compliant.
- As Client VPN is a managed service and the IP address to which the DNS name resolves might change. Hence, it is not recommended to connect to the Client VPN endpoint by using IP addresses. Use DNS instead.
- IP forwarding is currently disabled when using the AWS Client VPN Desktop Application.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A company is developing an application on AWS. For analysis, the application transmits log files to an Amazon Elasticsearch Service (Amazon ES) cluster. Each piece of data must be contained inside a VPC. A number of the company’s developers work remotely. Other developers are based at three distinct business locations. The developers must connect to Amazon ES directly from their local development computers in order to study and display logs. Which solution will satisfy these criteria?
- Configure and set up an AWS Client VPN endpoint. Associate the Client VPN endpoint with a subnet in the VPC. Configure a Client VPN self-service portal. Instruct the developers to connect by using the client for Client VPN.
- Create a transit gateway, and connect it to the VPC. Create an AWS Site-to-Site VPN. Create an attachment to the transit gateway. Instruct the developers to connect by using an OpenVPN client.
- Create a transit gateway, and connect it to the VPC. Order an AWS Direct Connect connection. Set up a public VIF on the Direct Connect connection. Associate the public VIF with the transit gateway. Instruct the developers to connect to the Direct Connect connection.
- Create and configure a bastion host in a public subnet of the VPC. Configure the bastion host security group to allow SSH access from the company CIDR ranges. Instruct the developers to connect by using SSH.
