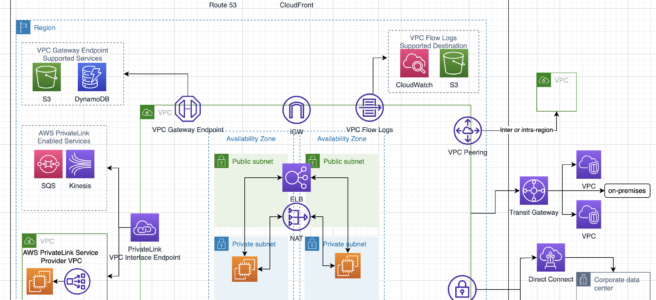
VPC Peering
- A VPC peering connection is a networking connection between two VPCs that enables routing of traffic between them using private IPv4 addresses or IPv6 addresses.
- VPC peering connection
- can be established between your own VPCs, or with a VPC in another AWS account in the same or different region.
- is a one-to-one relationship between two VPCs.
- supports intra and inter-region peering connections.
- With VPC peering,
- Instances in either VPC can communicate with each other as if they are within the same network
- AWS uses the existing infrastructure of a VPC to create a peering connection; it is neither a gateway nor a VPN connection and does not rely on a separate piece of physical hardware.
- There is no single point of failure for communication or a bandwidth bottleneck
- All inter-region traffic is encrypted with no single point of failure, or bandwidth bottleneck. Traffic always stays on the global AWS backbone, and never traverses the public internet, which reduces threats, such as common exploits, and DDoS attacks.
- VPC peering does not have any separate charges. However, there are data transfer charges.
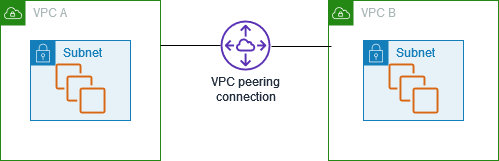
VPC Peering Connectivity
- To create a VPC peering connection, the owner of the requester VPC sends a request to the owner of the accepted VPC.
- Accepter VPC can be owned by the same account or a different AWS account.
- Once the Accepter VPC accepts the peering connection request, the peering connection is activated.
- Route tables on both the VPCs should be manually updated to allow traffic
- Security groups on the instances should allow traffic to and from the peered VPCs.
VPC Peering Limitations & Rules
- Does not support Overlapping or matching IPv4 or IPv6 CIDR blocks.
- Does not support transitive peering relationships i.e. the VPC does not have access to any other VPCs that the peer VPC may be peered with even if established entirely within your own AWS account
- Does not support Edge to Edge Routing Through a Gateway or Private Connection
- In a VPC peering connection, the VPC does not have access to any other connection that the peer VPC may have and vice versa. Connections that the peer VPC can include
- A VPN connection or an AWS Direct Connect connection to a corporate network
- An Internet connection through an Internet gateway
- An Internet connection in a private subnet through a NAT device
- A ClassicLink connection to an EC2-Classic instance
- A VPC endpoint to an AWS service; for example, an endpoint to S3.
- VPC peering connections are limited on the number of active and pending peering connections that you can have per VPC.
- Only one peering connection can be established between the same two VPCs at the same time.
- Jumbo frames are supported for peering connections within the same region.
- A placement group can span peered VPCs that are in the same region; however, you do not get full-bisection bandwidth between instances in peered VPCs
- Inter-region VPC peering connections
- The Maximum Transmission Unit (MTU) across an inter-region peering connection is 1500 bytes. Jumbo frames are not supported.
- Security group rule that references a peer VPC security group cannot be created.
- Any tags created for the peering connection are only applied in the account or region in which they were created
- Unicast reverse path forwarding in peering connections is not supported
- Circa July 2016, Instance’s Public DNS can now be resolved to its private IP address across peered VPCs.
The instance’s public DNS hostname does not resolve to its private IP address across peered VPCs.
VPC Peering Troubleshooting
- Verify that the VPC peering connection is in the Active state.
- Be sure to update the route tables for the peering connection. Verify that the correct routes exist for connections to the IP address range of the peered VPCs through the appropriate gateway.
- Verify that an ALLOW rule exists in the network access control (NACL) table for the required traffic.
- Verify that the security group rules allow network traffic between the peered VPCs.
- Verify using VPC flow logs that the required traffic isn’t rejected at the source or destination. This rejection might occur due to the permissions associated with security groups or network ACLs.
- Be sure that no firewall rules block network traffic between the peered VPCs. Use network utilities such as
traceroute(Linux) ortracert(Windows) to check rules for firewalls such as iptables (Linux) or Windows Firewall (Windows).
VPC Peering Architecture

- VPC Peering can be applied to create shared services or perform authentication with an on-premises instance
- This would help create a single point of contact, as well limiting the VPN connections to a single account or VPC
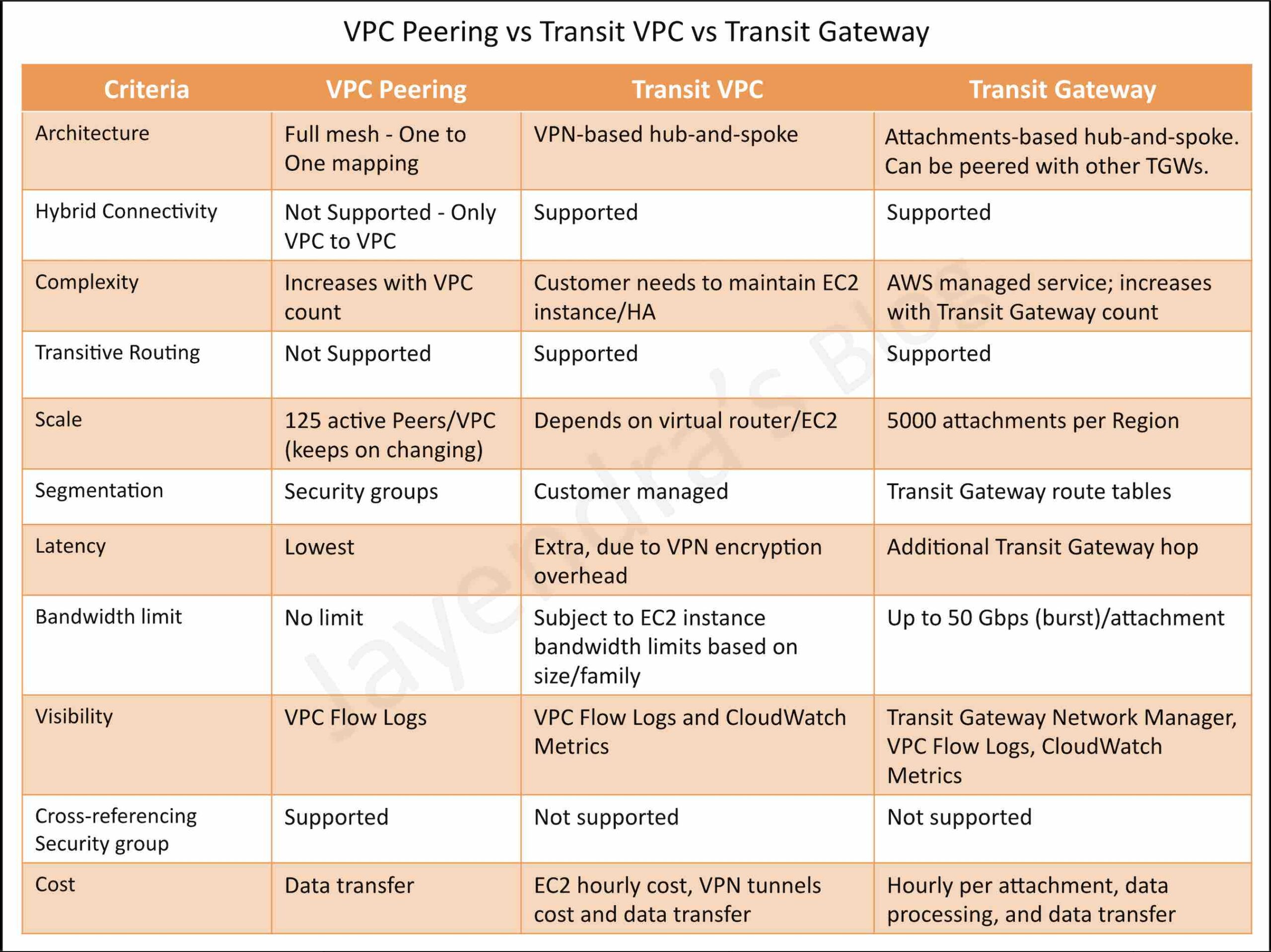
VPC Peering vs Transit Gateway
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- You currently have 2 development environments hosted in 2 different VPCs in an AWS account in the same region. There is now a need for resources from one VPC to access another. How can this be accomplished?
- Establish a Direct Connect connection.
- Establish a VPN connection.
- Establish VPC Peering.
- Establish Subnet Peering.
- A company has an AWS account that contains three VPCs (Dev, Test, and Prod) in the same region. Test is peered to both Prod and Dev. All VPCs have non-overlapping CIDR blocks. The company wants to push minor code releases from Dev to Prod to speed up the time to market. Which of the following options helps the company accomplish this?
- Create a new peering connection Between Prod and Dev along with appropriate routes.
- Create a new entry to Prod in the Dev route table using the peering connection as the target.
- Attach a second gateway to Dev. Add a new entry in the Prod route table identifying the gateway as the target.
- The VPCs have non-overlapping CIDR blocks in the same account. The route tables contain local routes for all VPCs.
- A company has 2 AWS accounts that have individual VPCs. The VPCs are in different AWS regions and need to communicate with each other. The VPCs have non-overlapping CIDR blocks. Which of the following would be a cost-effective connectivity option?
- Use VPN connections
- Use VPC peering between the 2 VPC’s
- Use AWS Direct Connect
- Use a NAT gateway