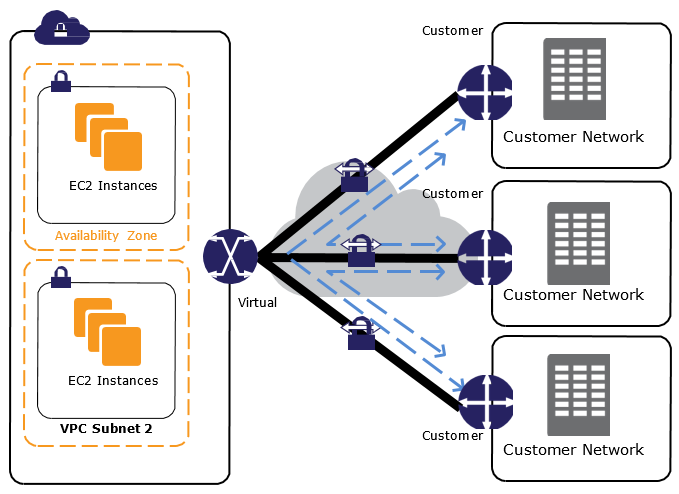
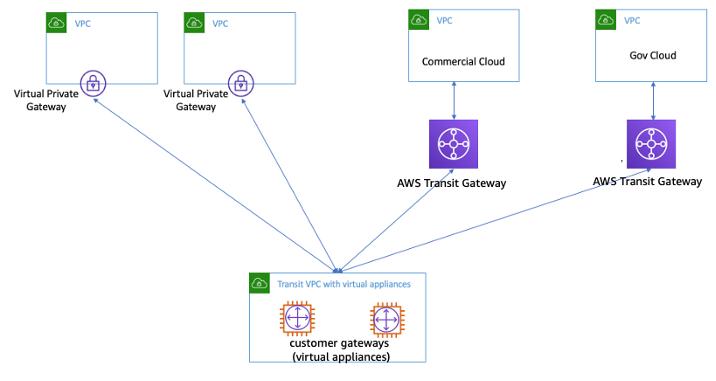
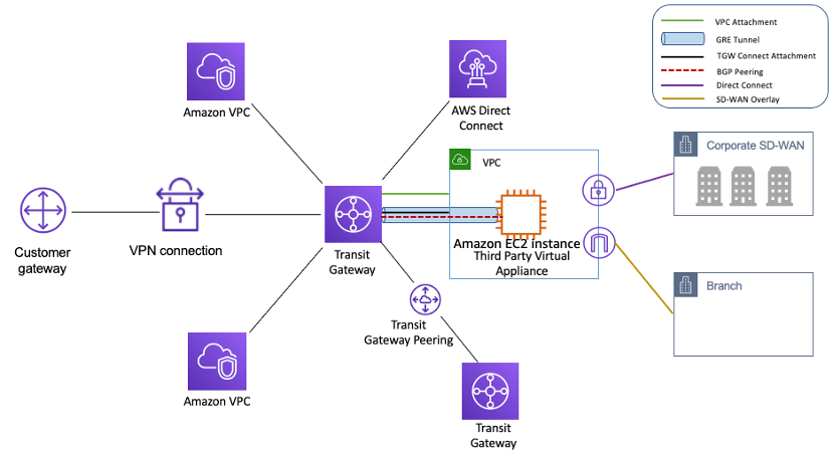
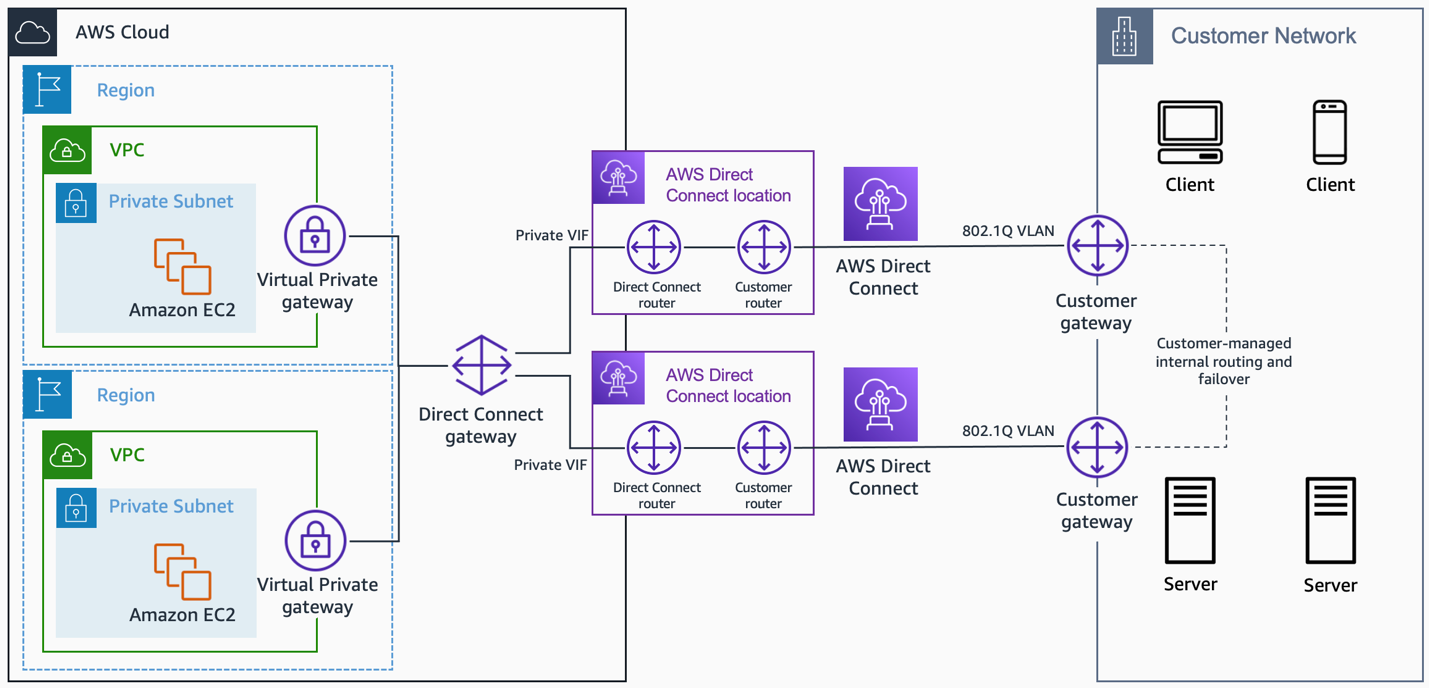
AWS VPC Endpoints
- VPC Endpoints enable the creation of a private connection between VPC to supported AWS services and VPC endpoint services powered by PrivateLink using its private IP address
- Endpoints do not require a public IP address, access over the Internet, NAT device, a VPN connection, or AWS Direct Connect.
- Traffic between VPC and AWS service does not leave the Amazon network
- Endpoints are virtual devices, that are horizontally scaled, redundant, and highly available VPC components that allow communication between instances in the VPC and AWS services without imposing availability risks or bandwidth constraints on your network traffic.
- Endpoints currently do not support cross-region requests, ensure that the endpoint is created in the same region as the S3 bucket
- AWS currently supports the following types of Endpoints
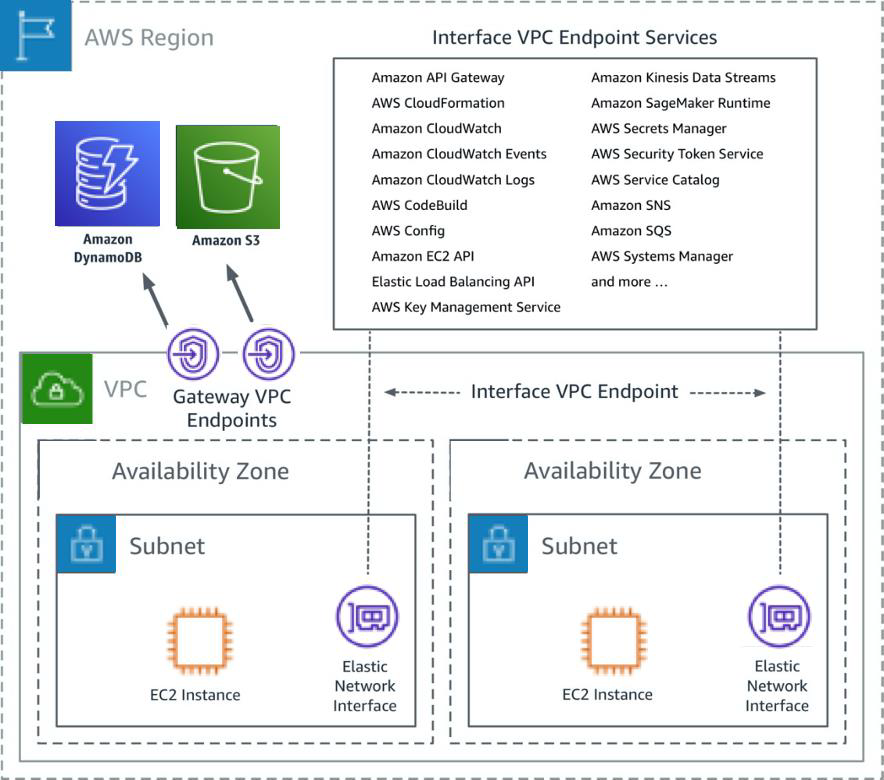
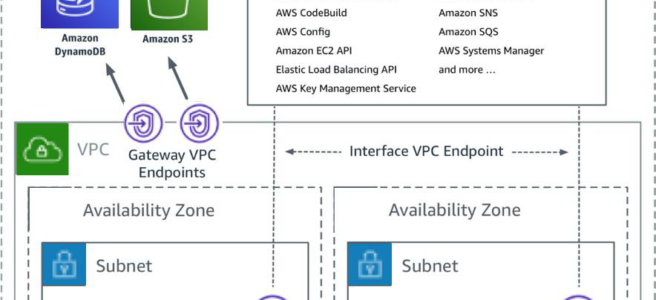
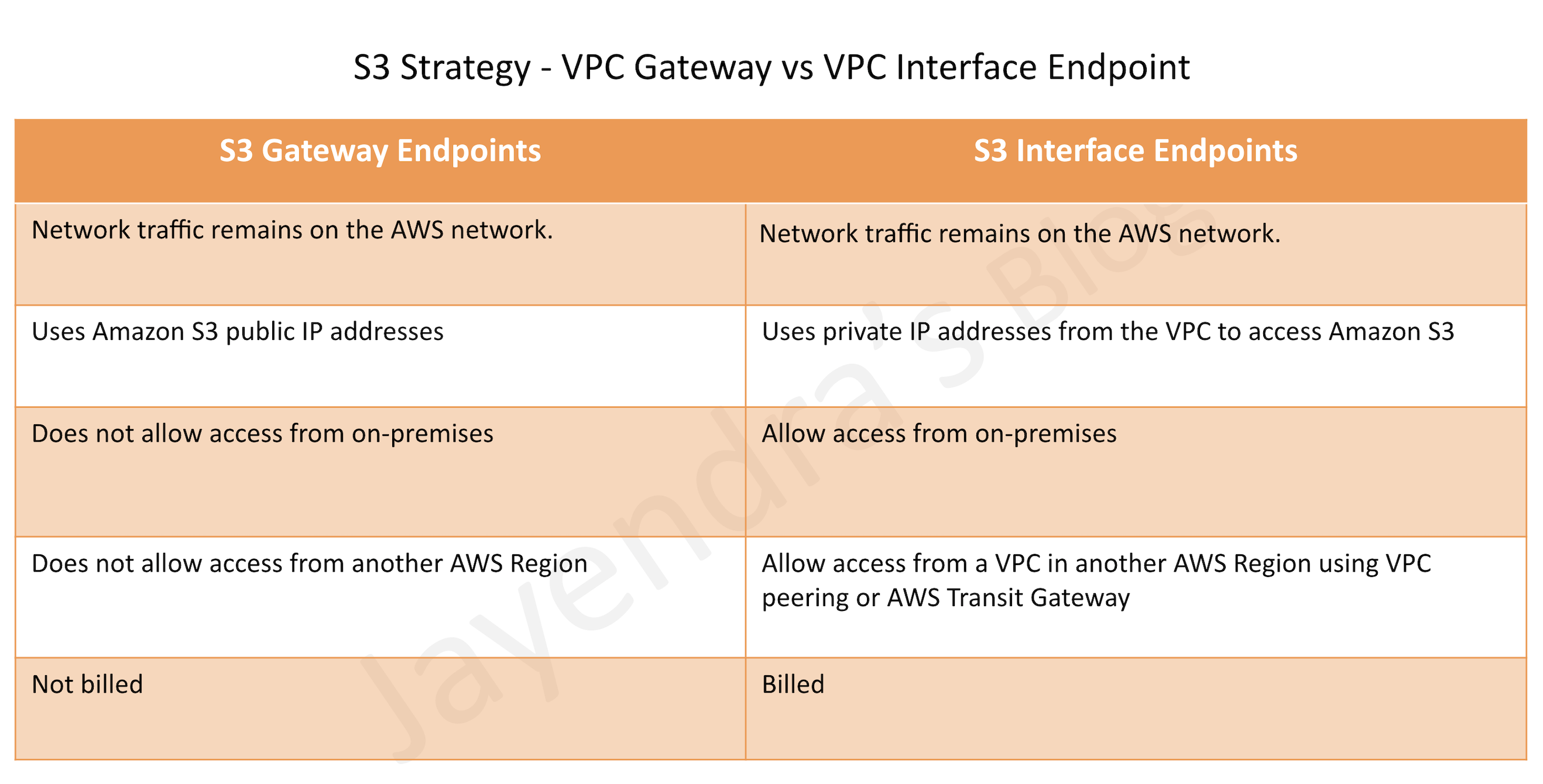
VPC Gateway Endpoints
- A VPC Gateway Endpoint is a gateway that is a target for a specified route in the route table, used for traffic destined for a supported AWS service.
- Gateway Endpoints currently supports S3 and DynamoDB services
- Gateway Endpoints do not require an Internet gateway or a NAT device for the VPC.
- Gateway endpoints do not enable AWS PrivateLink.
- VPC Endpoint policy and Resource-based policies can be used for fine-grained access control.
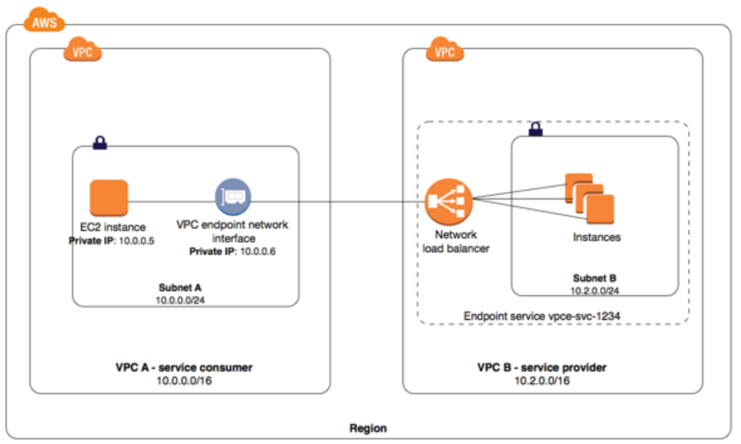
VPC Interface Endpoints – PrivateLink
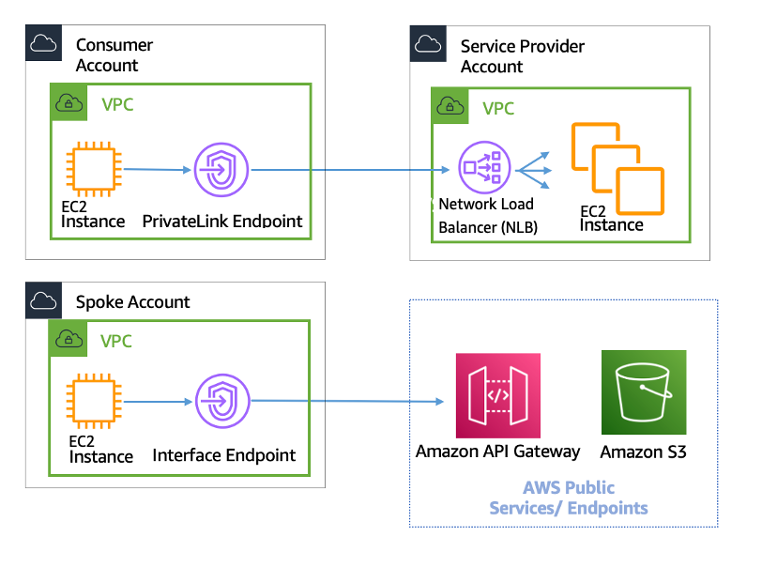
- VPC Interface endpoints enable connectivity to services powered by AWS PrivateLink.
- Services include AWS services like CloudTrail, CloudWatch, etc., services hosted by other AWS customers and partners in their own VPCs (referred to as endpoint services), and supported AWS Marketplace partner services.
- Interface Endpoints only allow traffic from VPC resources to the endpoints and not vice versa
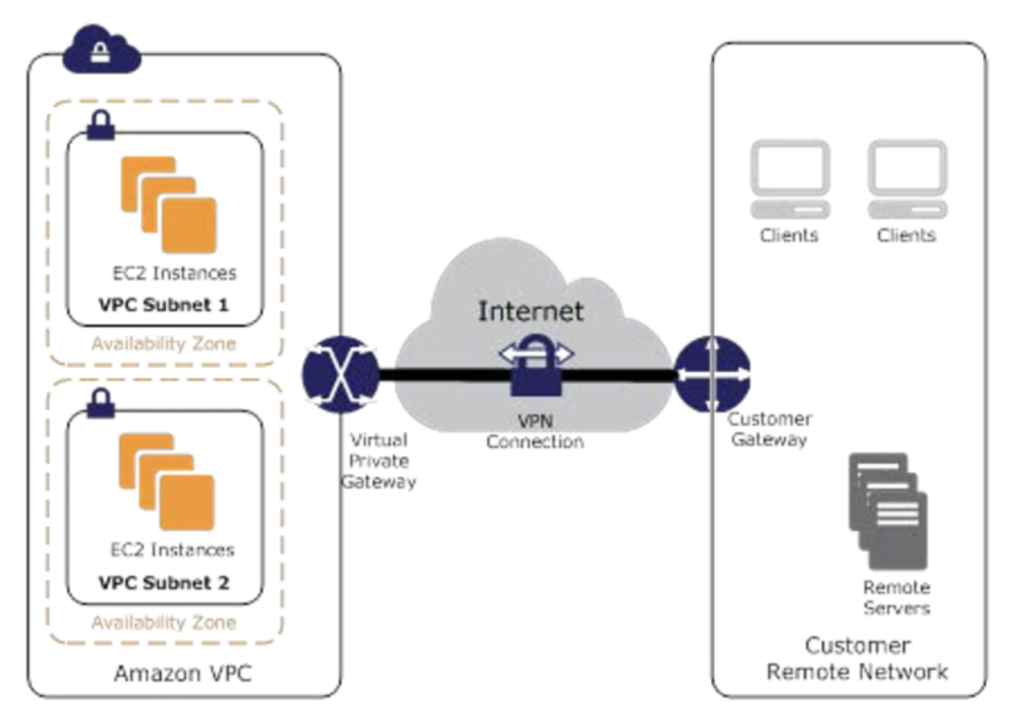
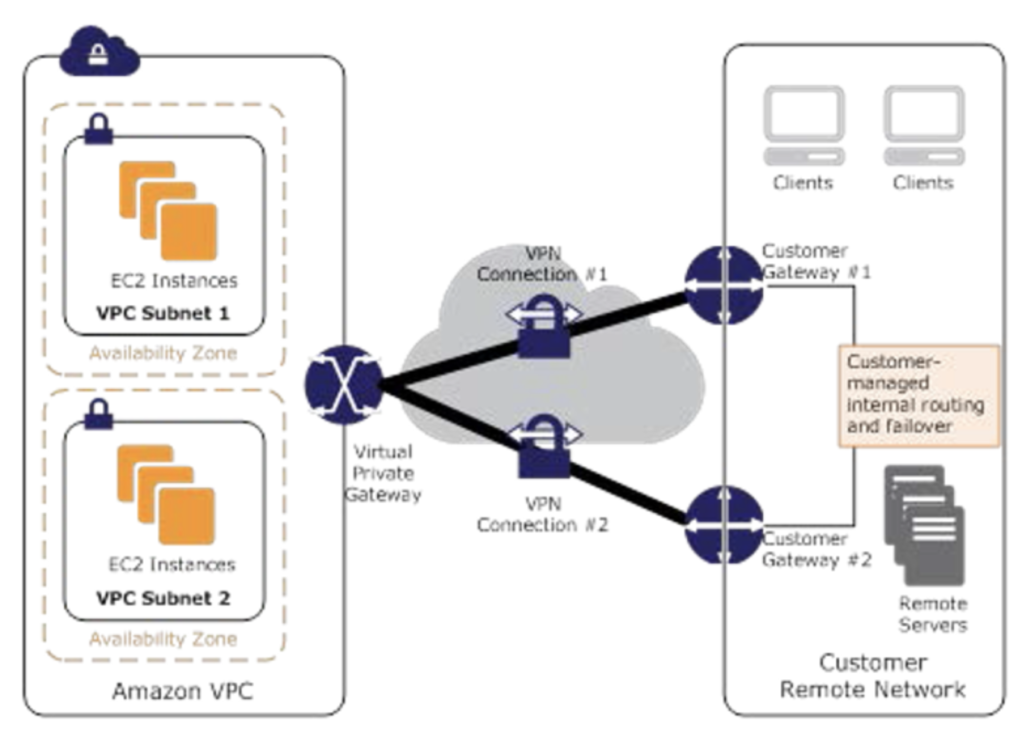
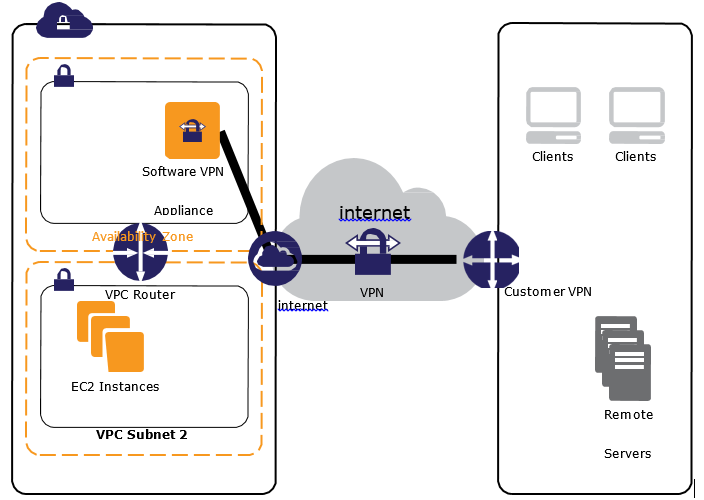
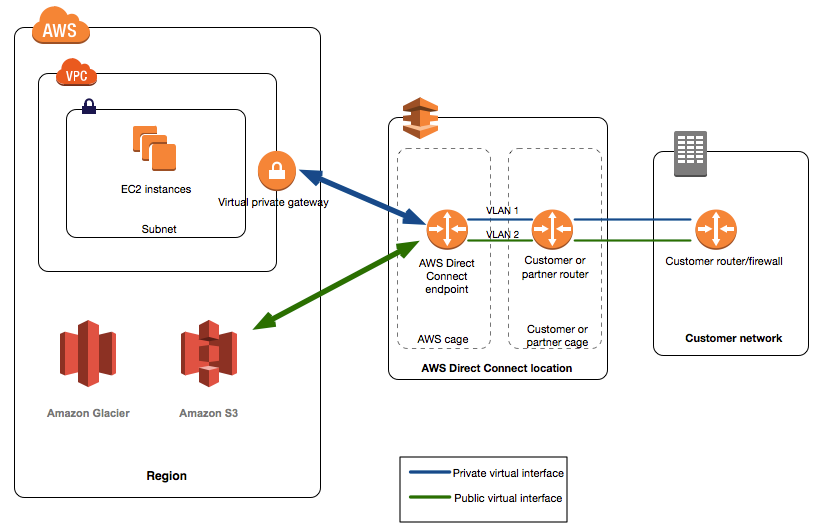
- PrivateLink endpoints can be accessed across both intra- and inter-region VPC peering connections, Direct Connect, and VPN connections.
- VPC Interface Endpoints, by default, have an address like
vpce-svc-01234567890abcdef.us-east-1.vpce.amazonaws.comwhich needs application changes to point to the service. - Private DNS name feature allows consumers to use AWS service public default DNS names which would point to the private VPC endpoint service.
- Interface Endpoints can be used to create custom applications in VPC and configure them as an AWS PrivateLink-powered service (referred to as an endpoint service) exposed through a Network Load Balancer.
- Custom applications can be hosted within AWS or on-premises (via Direct Connect or VPN)
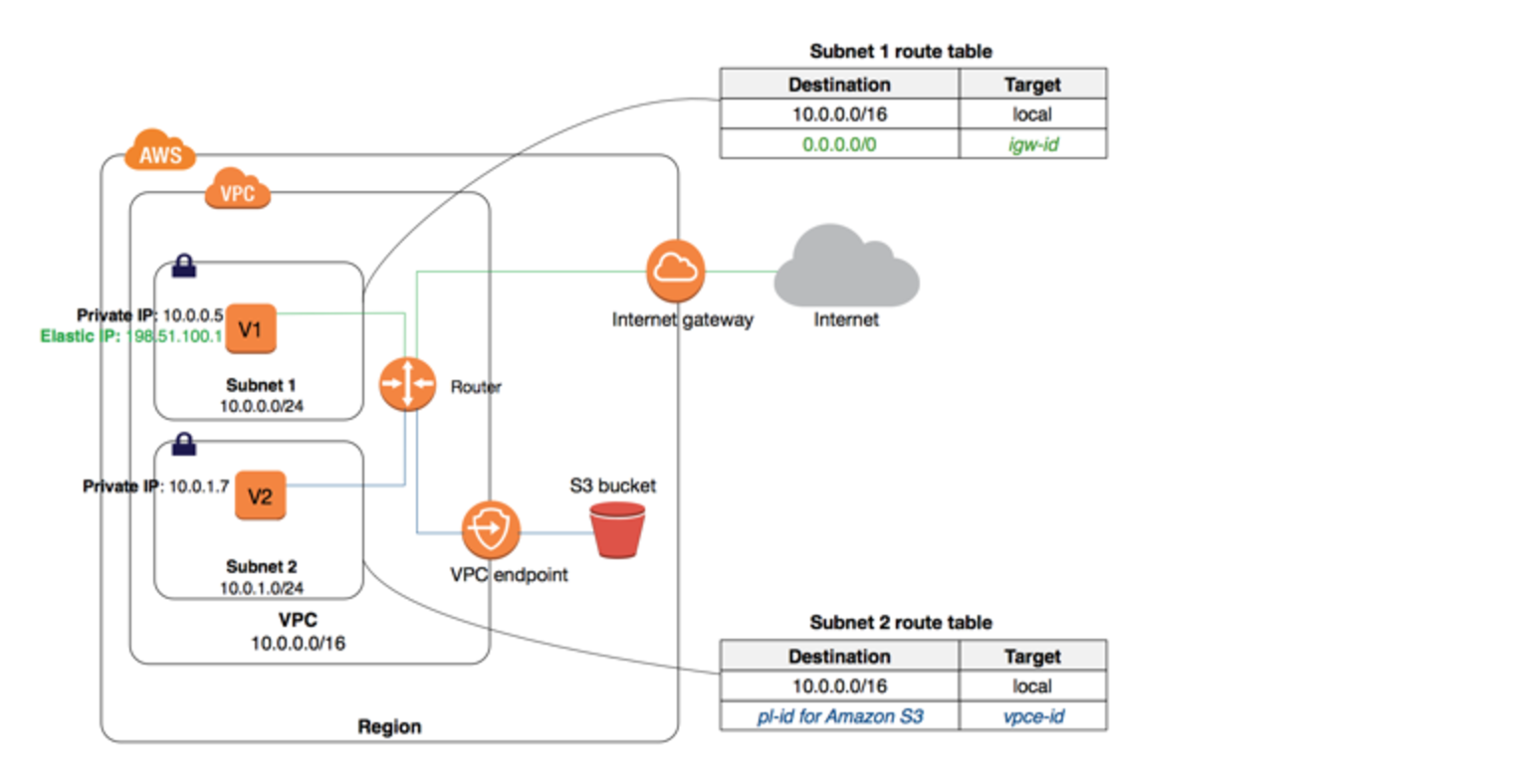
S3 VPC Endpoints Strategy
S3 is now accessible with both Gateway Endpoints and Interface Endpoints.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- You have an application running on an Amazon EC2 instance that uploads 10 GB video objects to amazon S3. Video uploads are taking longer than expected inspite of using multipart upload cause of internet bandwidth, resulting in poor application performance. Which action can help improve the upload performance?
- Apply an Amazon S3 bucket policy
- Use Amazon EBS provisioned IOPS
- Use VPC endpoints for S3
- Request a service limit increase
- What are the services supported by VPC endpoints, using Gateway endpoint type? Choose 2 answers
- Amazon S3
- Amazon EFS
- Amazon DynamoDB
- Amazon Glacier
- Amazon SQS
- What are the different types of endpoint types supported by VPC endpoints? Choose 2 Answers
- Gateway
- Classic
- Interface
- Virtual
- Network
- An application running on EC2 instances processes sensitive information stored on Amazon S3. The information is accessed over the Internet. The security team is concerned that the Internet connectivity to Amazon S3 is a security risk. Which solution will resolve the security concern?
- Access the data through an Internet Gateway.
- Access the data through a VPN connection.
- Access the data through a NAT Gateway.
- Access the data through a VPC endpoint for Amazon S3.
- You need to design a VPC for a three-tier architecture, a web application consisting of an Elastic Load Balancer (ELB), a fleet of web/application servers, and a backend consisting of an RDS database. The entire Infrastructure must be distributed over 2 availability zones. Which VPC configuration works while assuring the least components are exposed to Internet?
- Two public subnets for ELB, two private subnets for the web-servers, two private subnets for RDS and DynamoDB
- Two public subnets for ELB and web-servers, two private subnets for RDS and DynamoDB
- Two public subnets for ELB, two private subnets for the web-servers, two private subnets for RDS and VPC Endpoints for DynamoDB
- Two public subnets for ELB and web-servers, two private subnets for RDS and VPC Endpoints for DynamoDB