AWS Transit VPC
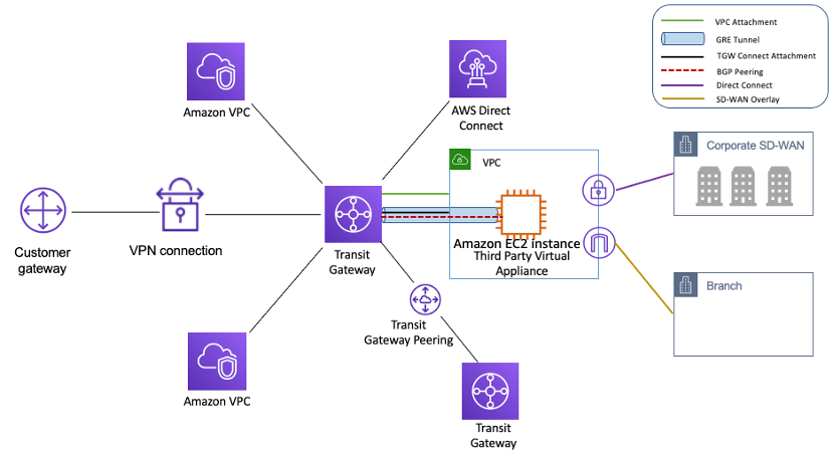
- Transit Gateway can be used instead of Transit VPC. AWS Transit Gateway offers the same advantages as transit VPC, but it is a managed service that scales elastically in a highly available product.
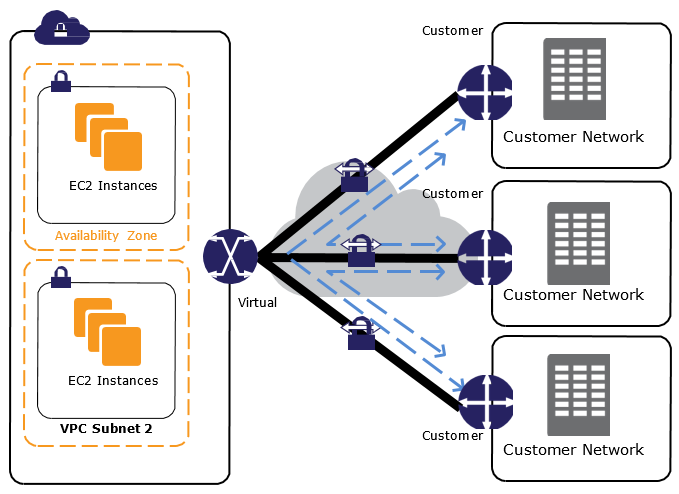
- Transit VPC helps connect multiple, geographically disperse VPCs and remote networks in order to create a global network transit center.
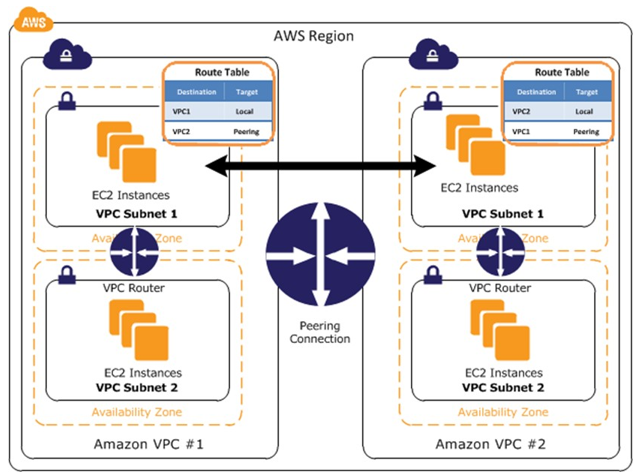
- Transit VPC can solve some of the shortcomings of VPC peering by introducing a hub and spoke design for inter-VPC connectivity.
- A transit VPC simplifies network management and minimizes the number of connections required to connect multiple VPCs and remote networks.
- Transit VPC allows an easy way to implement shared services or packet inspection/replication in a VPC.
- Transit VPC can be used to support important use cases
- Private Networking – build a private network that spans two or more AWS Regions.
- Shared Connectivity – Multiple VPCs can share connections to data centers, partner networks, and other clouds.
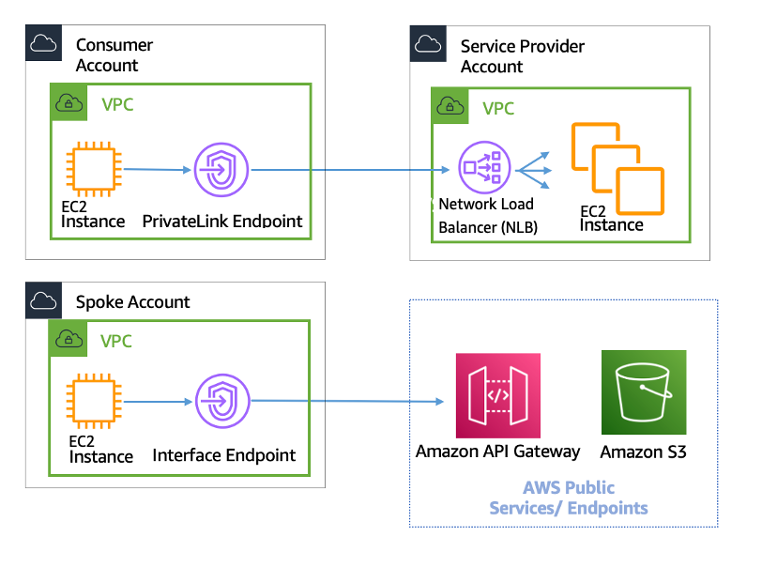
- Cross-Account AWS Usage – The VPCs and the AWS resources within them can reside in multiple AWS accounts.
- Transit VPC design helps implement more complex routing rules, such as network address translation between overlapping network ranges, or to add additional network-level packet filtering or inspection
Transit VPC Configuration
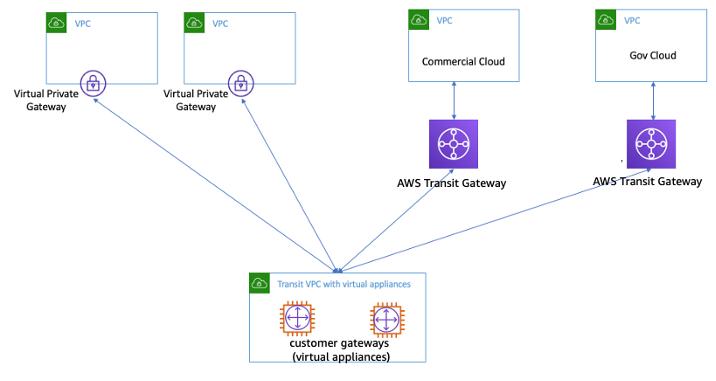
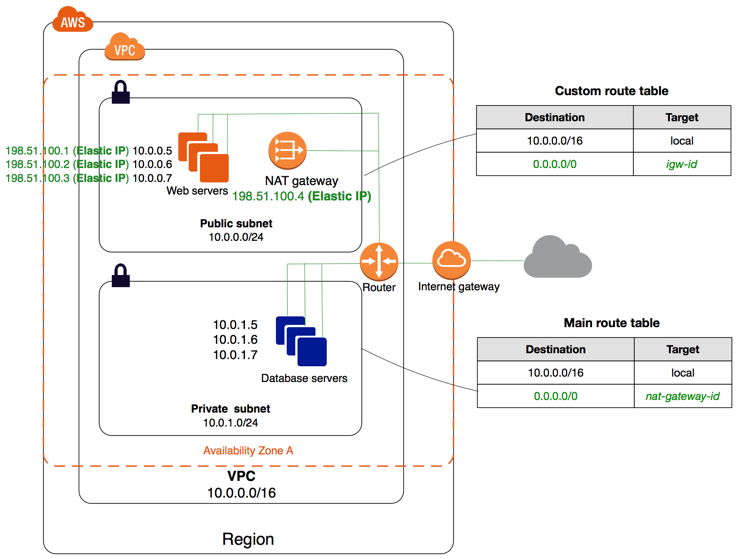
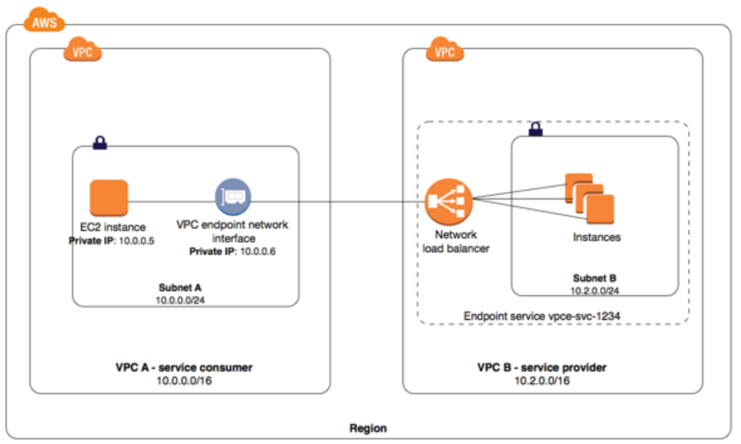
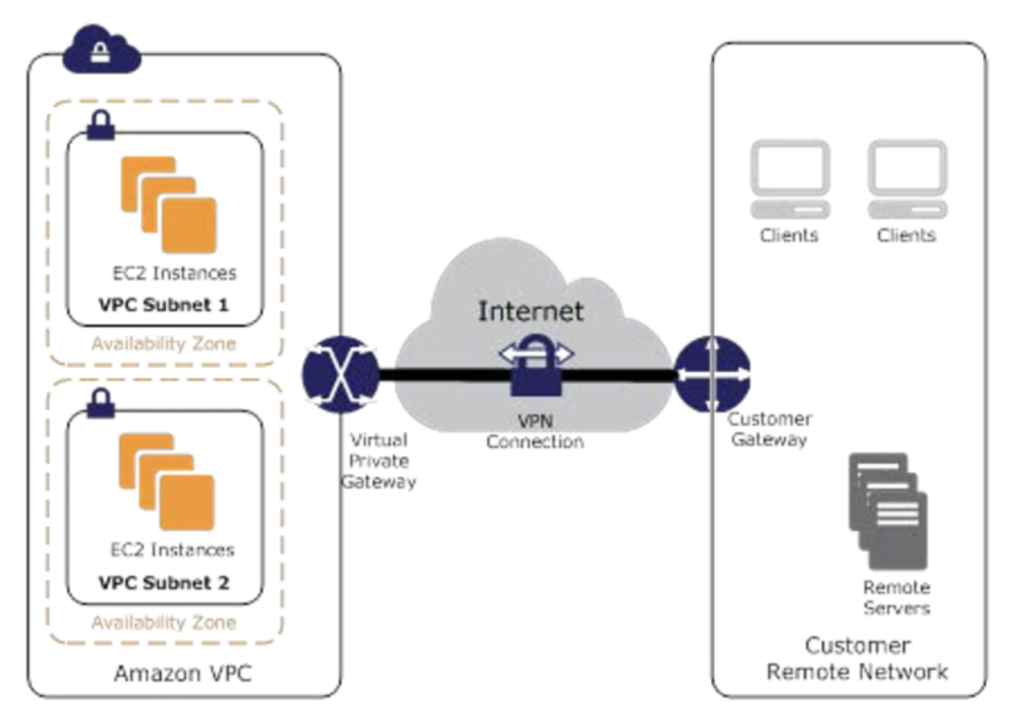
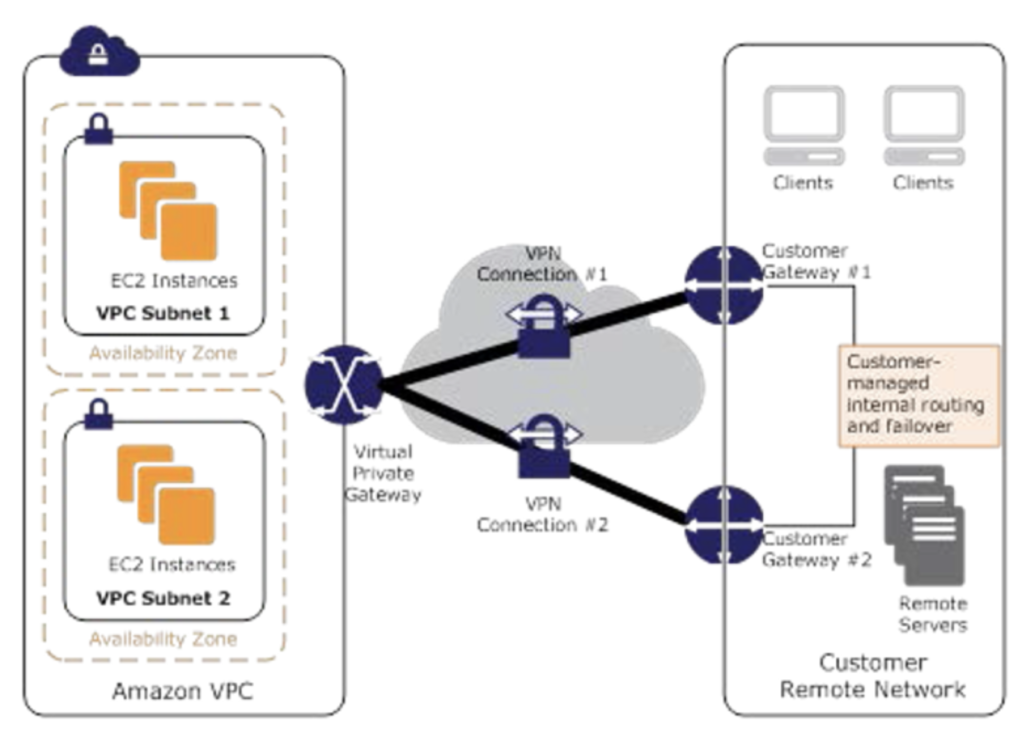
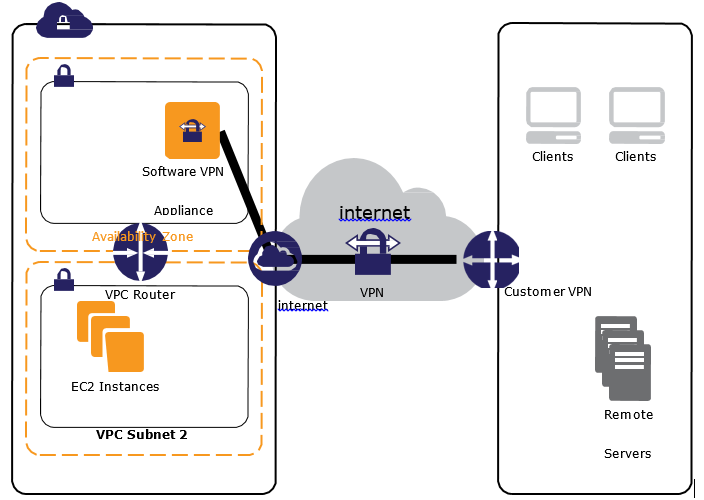
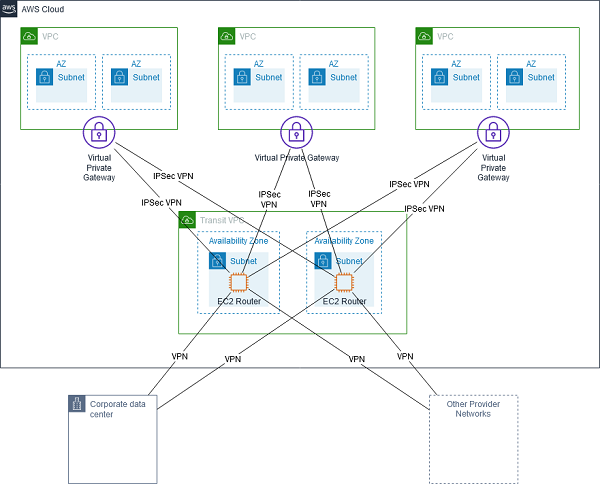
- Transit VPC network consists of a central VPC (the hub VPC) connecting with every other VPC (spoke VPC) through a VPN connection typically leveraging BGP over IPsec.
- Central VPC contains EC2 instances running software appliances that route incoming traffic to their destinations using the VPN overlay.
Transit VPC Advantages & Disadvantages
- supports Transitive routing using the overlay VPN network — allowing for a simpler hub and spoke design. Can be used to provide shared services for VPC Endpoints, Direct Connect connection, etc.
- supports network address translation between overlapping network ranges.
- supports vendor functionality around advanced security (layer 7 firewall/Intrusion Prevention System (IPS)/Intrusion Detection System (IDS) ) using third-party software on EC2
- leverages instance-based routing that increases costs while lowering availability and limiting the bandwidth.
- Customers are responsible for managing the HA and redundancy of EC2 instances running the third-party vendor virtual appliances
Transit VPC High Availability
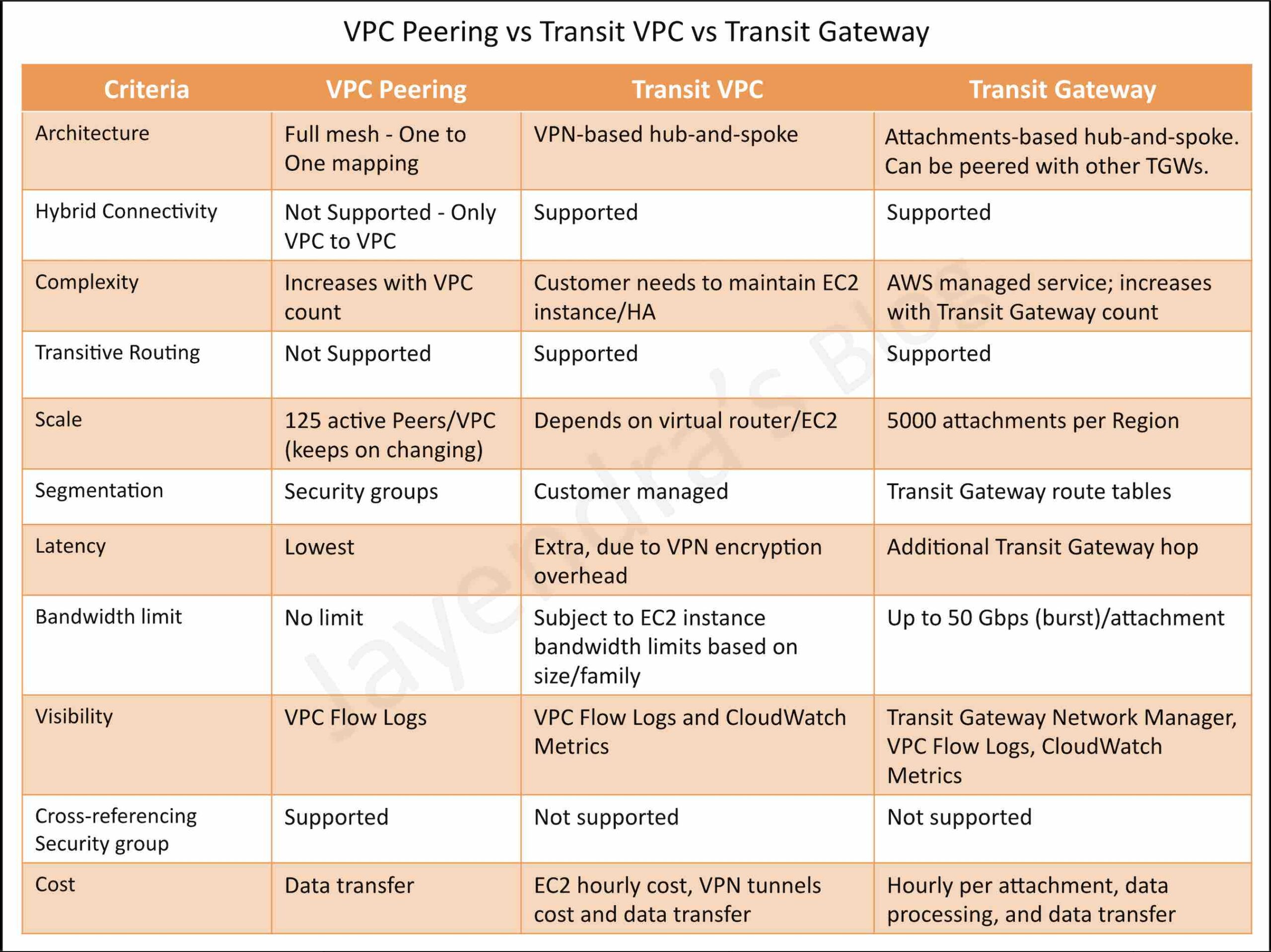
Transit VPC vs VPC Peering vs Transit Gateway
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Under increased cyber security concerns, a company is deploying a near real-time intrusion detection system (IDS) solution. A system must be put in place as soon as possible. The architecture consists of many AWS accounts, and all results must be delivered to a central location. Which solution will meet this requirement, while minimizing downtime and costs?
- Deploy a third-party vendor solution to perform deep packet inspection in a transit VPC.
- Enable VPC Flow Logs on each VPC. Set up a stream of the flow logs to a central Amazon Elasticsearch cluster.
- Enable Amazon Macie on each AWS account and configure central reporting.
- Enable Amazon GuardDuty on each account as members of a central account.
- Your company has set up a VPN connection between their on-premises infrastructure and AWS. They have multiple VPCs defined. They also need to ensure that all traffic flows through a security VPC from their on-premise infrastructure. How would you architect the solution? (Select TWO)
- Create a VPN connection between the On-premise environment and the Security VPC (Transit VPC pattern)
- Create a VPN connection between the On-premise environment to all other VPC’s
- Create a VPN connection between the Security VPC to all other VPC’s (Transit VPC pattern)
- Create a VPC peering connection between the Security VPC and all other VPC’s