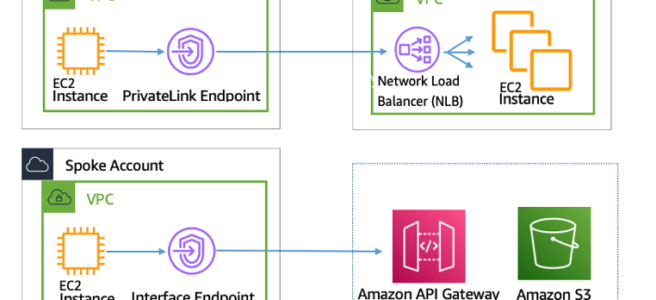
VPC Interface Endpoints – PrivateLink
- VPC Interface endpoints enable connectivity to services powered by AWS PrivateLink.
- Services include AWS services like CloudTrail, CloudWatch, etc., services hosted by other AWS customers and partners in their own VPCs (referred to as endpoint services), and supported AWS Marketplace partner services.
- VPC Interface Endpoints only allow traffic from VPC resources to the endpoints and not vice versa
- PrivateLink endpoints can be accessed across both intra- and inter-region VPC peering connections, Direct Connect, and VPN connections.
- VPC Interface Endpoints, by default, have an address like
vpce-svc-01234567890abcdef.us-east-1.vpce.amazonaws.comwhich needs application changes to point to the service. - Private DNS name feature allows consumers to use AWS service public default DNS names which would point to the private VPC endpoint service.
- Interface Endpoints can be used to create custom applications in VPC and configure them as an AWS PrivateLink-powered service (referred to as an endpoint service) exposed through a Network Load Balancer.
- Custom applications can be hosted within AWS or on-premises (via Direct Connect or VPN)
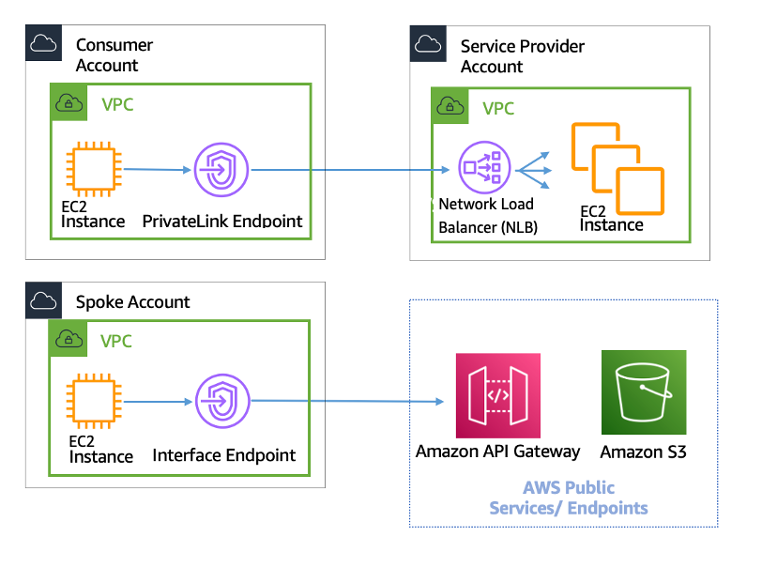
Interface Endpoints Configuration
- Create an interface endpoint, and provide the name of the AWS service, endpoint service, or AWS Marketplace service
- Choose the subnet to use the interface endpoint by creating an endpoint network interface.
- An endpoint network interface is assigned a private IP address from the IP address range of the subnet and keeps this IP address until the interface endpoint is deleted
- A private IP address also ensures the traffic remains private without any changes to the route table.
VPC Endpoint policy
- VPC Endpoint policy is an IAM resource policy attached to an endpoint for controlling access from the endpoint to the specified service.
- Endpoint policy, by default, allows full access to any user or service within the VPC, using credentials from any AWS account to any S3 resource; including S3 resources for an AWS account other than the account with which the VPC is associated
- Endpoint policy does not override or replace IAM user policies or service-specific policies (such as S3 bucket policies).
- Endpoint policy can be used to restrict which specific resources can be accessed using the VPC Endpoint.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
{ "Sid": "AccessToSpecificBucket", "Effect": "Allow", "Principal": "*", "Action": [ "s3:ListBucket", "s3:GetObject", ], "Resource": [ "arn:aws:s3:::example-bucket", "arn:aws:s3:::example-bucket/*" ] } |
Interface Endpoint Limitations
- For each interface endpoint, only one subnet per AZ can be selected.
- Interface Endpoint supports TCP traffic only.
- Endpoints are supported within the same region only.
- Endpoints support IPv4 traffic only.
- Each interface endpoint can support a bandwidth of up to 10 Gbps per AZ, by default, and automatically scales to 40 Gbps. Additional capacity may be added by reaching out to AWS support.
- NACLs for the subnet can restrict traffic, and needs to be configured properly
- Endpoints cannot be transferred from one VPC to another, or from one service to another.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- An application server needs to be in a private subnet without access to the internet. The solution must retrieve and upload data to an Amazon Kinesis. How should a Solutions Architect design a solution to meet these requirements?
- Use Amazon VPC Gateway endpoints
- Use a NAT Gateway
- Use Amazon VPC Interface endpoints
- Use a private Amazon Kinesis Data Stream