Elastic Container Registry – ECR
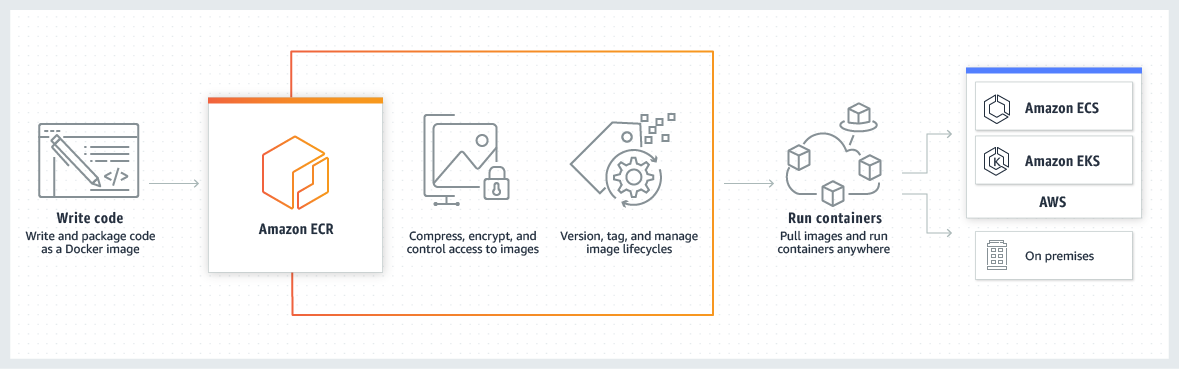
- Amazon Elastic Container Registry – ECR is a fully managed, secure, scalable, reliable container image registry service.
- makes it easy for developers to share and deploy container images and artifacts.
- is integrated with ECS, EKS, Fargate, and Lambda, simplifying the development to production workflow.
- eliminates the need to operate your own container repositories or worry about scaling the underlying infrastructure.
- hosts the images, using S3, in a highly available and scalable architecture, allowing you to deploy containers for the applications reliably.
- is a Regional service with the ability to push/pull images to the same AWS Region. Images can be pulled between Regions or out to the internet with additional latency and data transfer costs.
- supports cross-region and cross-account image replication.
- integrates with AWS IAM and supports resource-based permissions
- supports public and private repositories.
- automatically encrypts images at rest using S3 server-side encryption or AWS KMS encryption and transfers the container images over HTTPS.
- supports tools and docker CLI to push, pull and manage Docker images, Open Container Initiative (OCI) images, and OCI-compatible artifacts.
- automatically scans the container images for a broad range of operating system vulnerabilities.
- supports ECR Lifecycle policies that help with managing the lifecycle of the images in the repositories.
ECR Components
- Registry
- ECR private registry hosts the container images in a highly available and scalable architecture.
- A default ECR private registry is provided to each AWS account.
- One or more repositories can be created in the registry and images stored in them.
- Repositories can be configured for either cross-Region or cross-account replication.
- Private Registry is enabled for basic scanning, by default.
- Enhanced scanning can be enabled which provides an automated, continuous scanning mode that scans for both operating system and programming language package vulnerabilities.
- Repository
- An ECR repository contains Docker images, Open Container Initiative (OCI) images, and OCI compatible artifacts.
- Repositories can be controlled with both user access policies and individual repository policies.
- Image
- Images can be pushed and pulled to the repositories.
- Images can be used locally on the development system, or in ECS task definitions and EKS pod specifications
- Repository policy
- Repository policies are resource-based policies that can help control access to the repositories and the images within them.
- Repository policies are a subset of IAM policies that are scoped for, and specifically used for, controlling access to individual ECR repositories.
- A user or role only needs to be allowed permission for an action through either a repository policy or an IAM policy but not both for the action to be allowed.
- Resource-based policies also help grant the usage permission to other accounts on a per-resource basis.
- Authorization token
- A client must authenticate to the registries as an AWS user before they can push and pull images.
- An authentication token is used to access any ECR registry that the IAM principal has access to and is valid for 12 hours.
- Authorization token’s permission scope matches that of the IAM principal used to retrieve the authentication token.
ECR with VPC Endpoints
- ECR can be configured to use an Interface VPC endpoint, that enables you to privately access Amazon ECR APIs through private IP addresses.
- AWS PrivateLink restricts all network traffic between the VPC and ECR to the Amazon network. You don’t need an internet gateway, a NAT device, or a virtual private gateway.
- VPC endpoints currently don’t support cross-Region requests.
- VPC endpoints currently don’t support ECR Public repositories.
- VPC endpoints only support AWS provided DNS through Route 53.
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- A company is using Amazon Elastic Container Service (Amazon ECS) to run its container-based application on AWS. The company needs to ensure that the container images contain no severe vulnerabilities. Which solution will meet these requirements with the LEAST management overhead?
- Pull images from the public container registry. Publish the images to Amazon ECR repositories with scan on push configured.
- Pull images from the public container registry. Publish the images to a private container registry hosted on Amazon EC2 instances. Deploy host-based container scanning tools to EC2 instances that run ECS.
- Pull images from the public container registry. Publish the images to Amazon ECR repositories with scan on push configured.
- Pull images from the public container registry. Publish the images to AWS CodeArtifact repositories in a centralized AWS account.
References
Amazon_Elastic_Container_Registry_ECR

One thought on “Amazon Elastic Container Registry – ECR”
Comments are closed.