AWS Security Services Cheat Sheet
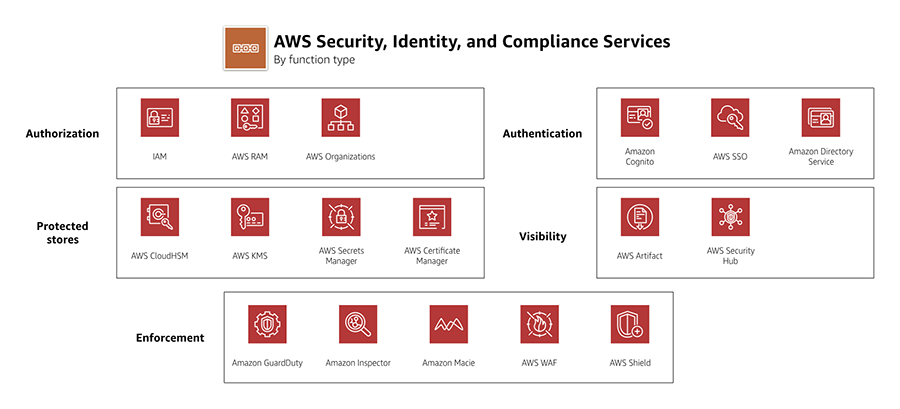
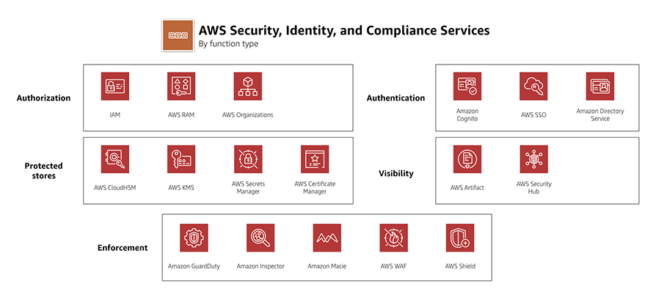
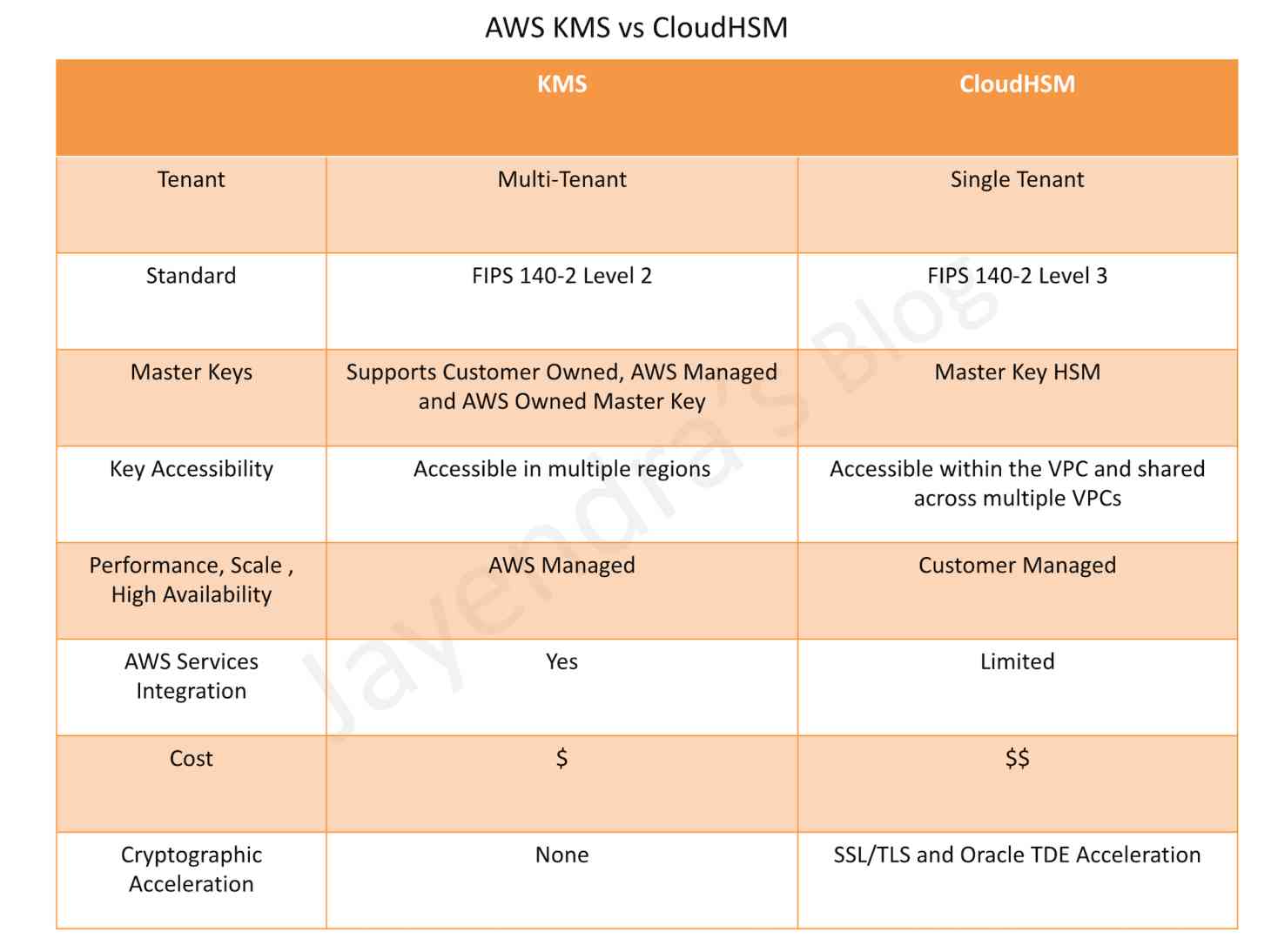
Key Management Service – KMS
- is a managed encryption service that allows the creation and control of encryption keys to enable data encryption.
- provides a highly available key storage, management, and auditing solution to encrypt the data across AWS services & within applications.
- uses hardware security modules (HSMs) to protect and validate the KMS keys by the FIPS 140-2 Cryptographic Module Validation Program.
- seamlessly integrates with several AWS services to make encrypting data in those services easy.
- supports multi-region keys, which are AWS KMS keys in different AWS Regions. Multi-Region keys are not global and each multi-region key needs to be replicated and managed independently.
CloudHSM
- provides secure cryptographic key storage to customers by making hardware security modules (HSMs) available in the AWS cloud
- helps manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs.
- single tenant, dedicated physical device to securely generate, store, and manage cryptographic keys used for data encryption
- are inside the VPC (not EC2-classic) & isolated from the rest of the network
- can use VPC peering to connect to CloudHSM from multiple VPCs
- integrated with Amazon Redshift and Amazon RDS for Oracle
- EBS volume encryption, S3 object encryption and key management can be done with CloudHSM but requires custom application scripting
- is NOT fault-tolerant and would need to build a cluster as if one fails all the keys are lost
- enables quick scaling by adding and removing HSM capacity on-demand, with no up-front costs.
- automatically load balance requests and securely duplicates keys stored in any HSM to all of the other HSMs in the cluster.
- expensive, prefer AWS Key Management Service (KMS) if cost is a criteria.
AWS WAF
- is a web application firewall that helps monitor the HTTP/HTTPS traffic and allows controlling access to the content.
- helps protect web applications from attacks by allowing rules configuration that allow, block, or monitor (count) web requests based on defined conditions. These conditions include IP addresses, HTTP headers, HTTP body, URI strings, SQL injection and cross-site scripting.
- helps define Web ACLs, which is a combination of Rules that is a combinations of Conditions and Action to block or allow
- integrated with CloudFront, Application Load Balancer (ALB), API Gateway services commonly used to deliver content and applications
- supports custom origins outside of AWS, when integrated with CloudFront
AWS Secrets Manager
- helps protect secrets needed to access applications, services, and IT resources.
- enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
- secure secrets by encrypting them with encryption keys managed using AWS KMS.
- offers native secret rotation with built-in integration for RDS, Redshift, and DocumentDB.
- supports Lambda functions to extend secret rotation to other types of secrets, including API keys and OAuth tokens.
- supports IAM and resource-based policies for fine-grained access control to secrets and centralized secret rotation audit for resources in the AWS Cloud, third-party services, and on-premises.
- enables secret replication in multiple AWS regions to support multi-region applications and disaster recovery scenarios.
- supports private access using VPC Interface endpoints
AWS Shield
- is a managed service that provides protection against Distributed Denial of Service (DDoS) attacks for applications running on AWS
- provides protection for all AWS customers against common and most frequently occurring infrastructure (layer 3 and 4) attacks like SYN/UDP floods, reflection attacks, and others to support high availability of applications on AWS.
- provides AWS Shield Advanced with additional protections against more sophisticated and larger attacks for applications running on EC2, ELB, CloudFront, AWS Global Accelerator, and Route 53.
AWS GuardDuty
- offers threat detection that enables continuous monitoring and protects the AWS accounts and workloads.
- is a Regional service
- analyzes continuous streams of meta-data generated from AWS accounts and network activity found in AWS CloudTrail Events, EKS audit logs, VPC Flow Logs, and DNS Logs.
- integrated threat intelligence
- combines machine learning, anomaly detection, network monitoring, and malicious file discovery, utilizing both AWS-developed and industry-leading third-party sources to help protect workloads and data on AWS
- supports suppression rules, trusted IP lists, and thread lists.
- provides Malware Protection to detect malicious files on EBS volumes
- operates completely independently from the resources so there is no risk of performance or availability impacts on the workloads.
Amazon Inspector
- is a vulnerability management service that continuously scans the AWS workloads for vulnerabilities
- automatically discovers and scans EC2 instances and container images residing in Elastic Container Registry (ECR) for software vulnerabilities and unintended network exposure.
- creates a finding, when a software vulnerability or network issue is discovered, that describes the vulnerability, rates its severity, identifies the affected resource, and provides remediation guidance.
- is a Regional service.
- requires Systems Manager (SSM) agent to be installed and enabled.
Amazon Detective
- helps analyze, investigate, and quickly identify the root cause of potential security issues or suspicious activities.
- automatically collects log data from the AWS resources and uses machine learning, statistical analysis, and graph theory to build a linked set of data to easily conduct faster and more efficient security investigations.
- enables customers to view summaries and analytical data associated with CloudTrail logs, EKS audit logs, VPC Flow Logs.
- provides detailed summaries, analysis, and visualizations of the behaviors and interactions amongst your AWS accounts, EC2 instances, AWS users, roles, and IP addresses.
- maintains up to a year of aggregated data
- is a Regional service and needs to be enabled on a region-by-region basis.
- is a multi-account service that aggregates data from monitored member accounts under a single administrative account within the same region.
- has no impact on the performance or availability of the AWS infrastructure since it retrieves the log data and findings directly from the AWS services.
AWS Security Hub
- a cloud security posture management service that performs security best practice checks, aggregates alerts, and enables automated remediation.
- collects security data from across AWS accounts, services, and supported third-party partner products and helps you analyze your security trends and identify the highest priority security issues.
- is Regional abut supports cross-region aggregation of findings.
- automatically runs continuous, account-level configuration and security checks based on AWS best practices and industry standards which include CIS Foundations, PCI DSS.
- consolidates the security findings across accounts and provider products and displays results on the Security Hub console.
- supports integration with Amazon EventBridge. Custom actions can be defined when a finding is received.
- has multi-account management through AWS Organizations integration, which allows delegating an administrator account for the organization.
- works with AWS Config to perform most of its security checks for controls
AWS Macie
- Macie is a data security service that discovers sensitive data by using machine learning and pattern matching, provides visibility into data security risks, and enables automated protection against those risks.
- provides an inventory of the S3 buckets and automatically evaluates and monitors the buckets for security and access control.
- automates the discovery, classification, and reporting of sensitive data.
- generates a finding for you to review and remediate as necessary if it detects a potential issue with the security or privacy of the data, such as a bucket that becomes publicly accessible.
- provides multi-account support using AWS Organizations to enable Macie across all of the accounts.
- is a regional service and must be enabled on a region-by-region basis and helps view findings across all the accounts within each Region.
- supports VPC Interface Endpoints to access Macie privately from a VPC without an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection.
AWS Artifact
- is a self-service audit artifact retrieval portal that provides customers with on-demand access to AWS’ compliance documentation and agreements
- can use AWS Artifact Reports to download AWS security and compliance documents, such as AWS ISO certifications, Payment Card Industry (PCI), and System and Organization Control (SOC) reports.