Table of Contents
hide
AWS Key Management Service – KMS
- AWS Key Management Service – KMS is a managed encryption service that allows the creation and control of encryption keys to enable data encryption.
- provides a highly available key storage, management, and auditing solution to encrypt the data across AWS services & within applications.
- uses hardware security modules (HSMs) to protect and validate the keys by the FIPS 140-2 Cryptographic Module Validation Program.
- seamlessly integrates with several AWS services to make encrypting data in those services easy.
- is integrated with AWS CloudTrail to provide encryption key usage logs to help meet auditing, regulatory, and compliance needs.
is regional and keys are only stored and used in the region in which they are created. They cannot be transferred to another region.- enforces usage and management policies, to control which IAM user, role from the account, or other accounts can manage and use keys.
- can create and manage keys by
- Create, edit, and view symmetric and asymmetric keys, including HMAC keys.
- Control access to the keys by using key policies, IAM policies, and grants. Policies can be further refined using condition keys.
- Supports attribute-based access control (ABAC).
- Create, delete, list, and update aliases for the keys.
- Tag the keys for identification, automation, and cost tracking.
- Enable and disable keys.
- Enable and disable automatic rotation of the cryptographic material in keys.
- Delete keys to complete the key lifecycle.
- supports the following cryptographic operations
- Encrypt, decrypt, and re-encrypt data with symmetric or asymmetric keys.
- Sign and verify messages with asymmetric keys.
- Generate exportable symmetric data keys and asymmetric data key pairs.
- Generate and verify HMAC codes.
- Generate random numbers suitable for cryptographic applications
- supports multi-region keys, which act like copies of the same KMS key in different AWS Regions that can be used interchangeably – as though you had the same key in multiple Regions.
- supports VPC private endpoint to connect KMS privately from a VPC.
- supports keys in a CloudHSM key store backed by the CloudHSM cluster.
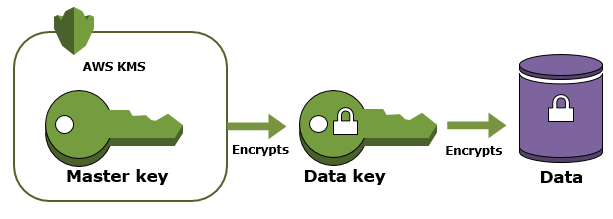
Envelope encryption
- AWS cloud services integrated with AWS KMS use a method called envelope encryption to protect the data.
- Envelope encryption is an optimized method for encrypting data that uses two different keys (Master key and Data key)
- With Envelop encryption
- A data key is generated and used by the AWS service to encrypt each piece of data or resource.
- Data key is encrypted under a defined master key.
- Encrypted data key is then stored by the AWS service.
- For data decryption by the AWS service, the encrypted data key is passed to KMS and decrypted under the master key that was originally encrypted so the service can then decrypt the data.
- When the data is encrypted directly with KMS it must be transferred over the network.
- Envelope encryption can offer significant performance benefits as KMS only supports sending data less than 4 KB to be encrypted.
- Envelope encryption reduces the network load for the application or AWS cloud service as only the request and fulfillment of the data key must go over the network.
KMS Service Concepts
KMS Keys OR Customer Master Keys (CMKs)
- AWS KMS key is a logical representation of a cryptographic key.
- KMS Keys can be used to create symmetric or asymmetric keys for encryption or signing OR HMAC keys to generate and verify HMAC tags.
- Symmetric keys and the private keys of asymmetric keys never leave AWS KMS unencrypted.
- A KMS key contains metadata, such as the key ID, key spec, key usage, creation date, description, key state, and a reference to the key material that is used to run cryptographic operations with the KMS key.
- Symmetric keys are 256-bit AES keys that are not exportable.
- KMS keys can be used to generate, encrypt, and decrypt the data keys, used outside of AWS KMS to encrypt the data [Envelope Encryption]
- Key material for symmetric keys and the private keys of asymmetric key never leaves AWS KMS unencrypted.
Customer Keys and AWS Keys
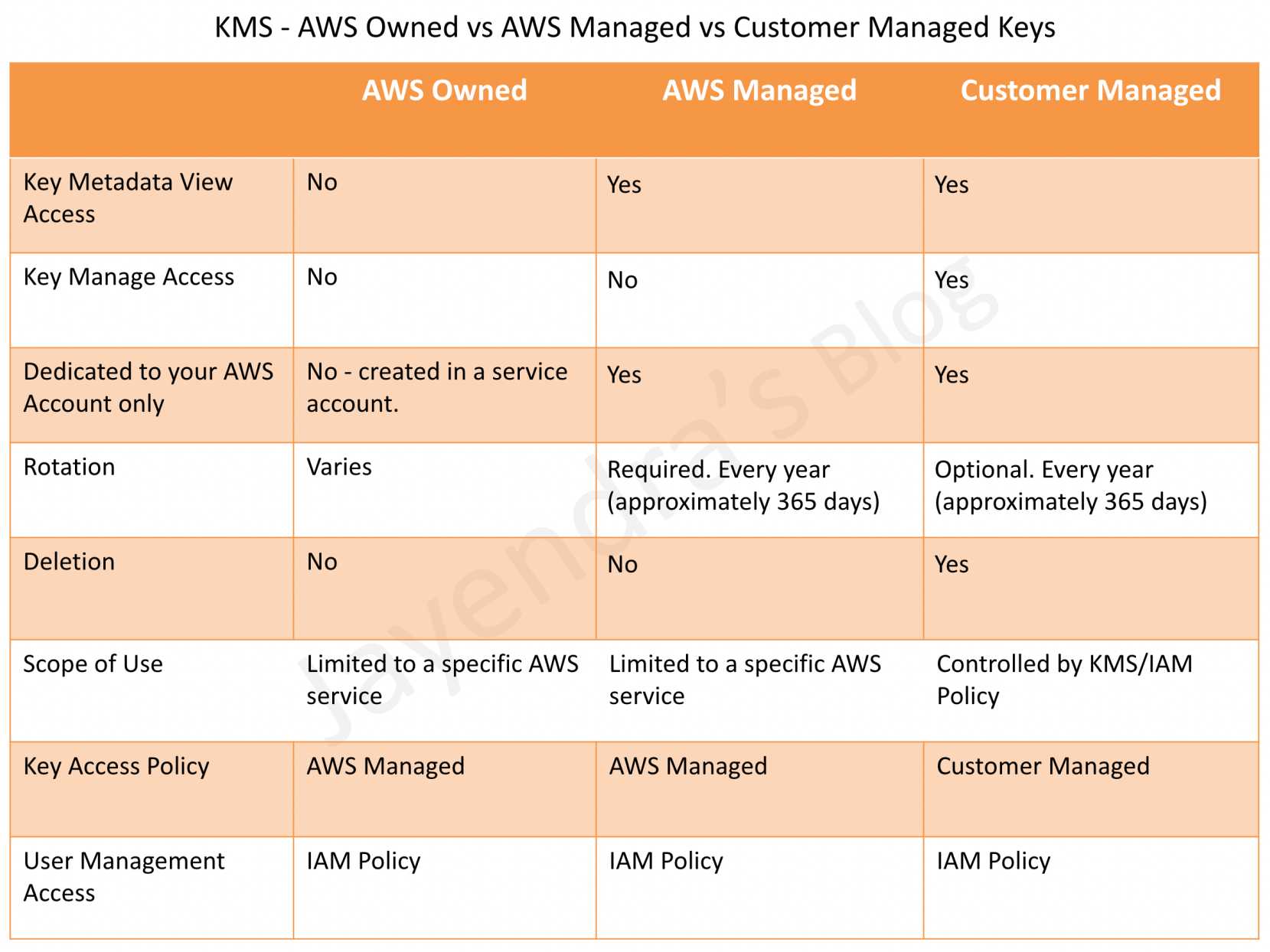
AWS Managed Keys
- AWS Managed keys are created, managed, and used on your behalf by AWS services in your AWS account.
- keys are automatically rotated every year (~365 days) and the rotation schedule cannot be changed.
- have permission to view the AWS managed keys in your account, view their key policies, and audit their use in CloudTrail logs.
- cannot manage or rotate these keys, change their key policies, or use them in cryptographic operations directly; the service that creates them uses them on your behalf.
Customer managed keys
- Customer managed keys are created by you to encrypt your service resources in your account.
- Automatic rotation is Optional and if enabled, keys are automatically rotated every year.
- provides full control over these keys, including establishing and maintaining their key policies, IAM policies, and grants, enabling and disabling them, rotating their cryptographic material, adding tags, creating aliases refering the KMS keys, and scheduling the KMS keys for deletion.
AWS Owned Keys
- AWS owned keys are a collection of KMS keys that an AWS service owns and manages for use in multiple AWS accounts.
- AWS owned keys are not in your AWS account, however, an AWS service can use the associated AWS owned keys to protect the resources in your account.
- cannot view, use, track, or audit them
Key Material
- KMS keys contain a reference to the key material used to encrypt and decrypt data.
- By default, AWS KMS generates the key material for a newly created key.
- KMS key can be created without key material and then your own key material can be imported or created in the AWS CloudHSM cluster associated with an AWS KMS custom key store.
- Key material cannot be extracted, exported, viewed, or managed.
- Key material cannot be deleted; you must delete the KMS key.
Key Material Origin
- Key material origin is a KMS key property that identifies the source of the key material in the KMS key.
- Symmetric encryption KMS keys can have one of the following key material origin values.
- AWS_KMS
- AWS KMS creates and manages the key material for the KMS key in AWS KMS.
- EXTERNAL
- Key has imported key material.
- Management and security of the key are the customer’s responsibility.
- Only symmetric keys are supported.
- Automatic rotation is not supported and needs to be manually rotated.
- AWS_CLOUDHSM
- AWS KMS created the key material for the KMS key in the AWS CloudHSM cluster associated with the custom key store.
- EXTERNAL_KEY_STORE
- Key material is a cryptographic key in an external key manager outside of AWS.
- This origin is supported only for KMS keys in an external key store.
- AWS_KMS
Data Keys
- Data keys are encryption keys that you can use to encrypt data, including large amounts of data and other data encryption keys.
- KMS does not store, manage, or track your data keys.
- Data keys must be used by services outside of KMS.
Encryption Context
- Encryption context provides an optional set of key–value pairs that can contain additional contextual information about the data.
- AWS KMS uses the encryption context as additional authenticated data (AAD) to support authenticated encryption.
- Encryption context is not secret and not encrypted and appears in plaintext in CloudTrail Logs so you can use it to identify and categorize your cryptographic operations.
- Encryption context should not include sensitive information.
- Encryption context usage
- When an encryption context is included in an encryption request, it is cryptographically bound to the ciphertext such that the same encryption context is required to decrypt the data.
- If the encryption context provided in the decryption request is not an exact, case-sensitive match, the decrypt request fails.
- Only the order of the key-value pairs in the encryption context can vary.
Key Policies
- help determine who can use and manage those keys.
- can add, remove, or change permissions at any time for a customer-managed key.
- cannot edit the key policy for AWS owned or managed keys.
Grants
- provides permissions, an alternative to the key policy and IAM policy, that allows AWS principals to use the KMS keys.
- are often used for temporary permissions because you can create one, use its permissions, and delete it without changing the key policies or IAM policies.
- permissions specified in the grant might not take effect immediately due to eventual consistency.
Grant Tokens
- help mitigate the potential delay with grants.
- use the grant token received in the response to
CreateGrantAPI request to make the permissions in the grant take effect immediately.
Alias
- Alias helps provide a friendly name for a KMS key.
- can be used to refer to different KMS keys in each AWS Region.
- can be used to point to different keys without changing the code.
- can allow and deny access to KMS keys based on their aliases without editing policies or managing grants.
- aliases are independent resources, not properties of a KMS key, and can be added, changed, and deleted without affecting the associated KMS key.
Encryption & Decryption Process
- Use KMS to get encrypted and plaintext data keys using CMK.
- Use the plaintext data key to encrypt the data and store the encrypted data key with the data.
- Use KMS decrypt to get the plaintext data key and decrypt the data.
- Remove the plaintext data key from memory, once the operation is completed.
KMS Working
- KMS centrally manages and securely stores the keys.
- Keys can be generated or imported from the key management infrastructure (KMI).
- Keys can be used from within the applications and supported AWS services to protect the data, but the key never leaves KMS.
- Data is submitted to KMS to be encrypted, or decrypted, under keys that you control.
- Usage policies on these keys can be set that determines which users can use them to encrypt and decrypt data.
KMS Access Control
- Primary way to manage access to AWS KMS keys is with policies.
- KMS keys access can be controlled using
- Key Policies
- are resource-based policies
- every KMS key has a key policy
- is a primary mechanism for controlling access to a key.
- can be used alone to control access to the keys.
- IAM policies
- use IAM policies in combination with the key policy to control access to keys.
- helps manage all of the permissions for your IAM identities in IAM.
- Grants
- Use grants in combination with the key policy and IAM policies to allow access to keys.
- helps allow access to the keys in the key policy, and to allow users to delegate their access to others.
- Key Policies
- To allow access to a KMS CMK, a key policy MUST be used, either alone or in combination with IAM policies or grants.
- IAM policies by themselves are not sufficient to allow access to keys, though they can be used in combination with a key policy.
- IAM user who creates a KMS key is not considered to be the key owner and they don’t automatically have permission to use or manage the KMS key that they created.
Rotating KMS or Customer Master Keys
- Key rotation changes only the key material, which is the cryptographic secret that is used in encryption operations.
- KMS keys can be enabled for automatic key rotation, where KMS generates new cryptographic material for the key every year.
- KMS saves all previous versions of the cryptographic material in perpetuity so it can decrypt any data encrypted with that key.
- KMS does not delete any rotated key material until you delete the KMS key.
- All new encryption requests against a key are encrypted under the newest version of the key.
- Rotation can be tracked in CloudWatch and CloudTrail.
Automatic Key Rotation
- Automatic key rotation has the following benefits
- properties of the KMS key like ID, ARN, region, policies, and permissions do not change.
- applications or aliases refering the key do not need to change
- Rotating key material does not affect the use of the KMS key in any AWS service.
- Automatic key rotation is supported only on symmetric encryption KMS keys with key material that KMS generates i.e. Origin = AWS_KMS.
- Automatic key rotation is not supported for
- asymmetric keys,
- HMAC keys,
- keys in custom key stores, and
- keys with imported key material.
- AWS managed keys
- automatically rotated every 1 year (updated from 3 years before)
- rotation cannot be enabled or disabled
- Customer Managed keys
- automatic key rotation is supported but is optional.
- automatic key rotation is disabled, by default, and needs to be enabled.
- keys can be rotated every year.
- CMKs with imported key material or keys generated in a CloudHSM cluster using the KMS custom key store feature
- do not support automatic key rotation.
- provide flexibility to manually rotate keys as required.
Manual Key Rotation
- Manual key rotation can be performed by creating a KMS key and updating the applications or aliases to point to the new key.
- does not retain the ID, ARN, and policies of the key.
- can help control the rotation frequency esp. if the frequency required is less than a year.
- is also a good solution for KMS keys that are not eligible for automatic key rotation, such as asymmetric keys, HMAC keys, keys in custom key stores, and keys with imported key material.
- For manually rotated keys, data has to be re-encrypted depending on the application’s configuration.
KMS Deletion
- KMS key deletion deletes the key material and all metadata associated with the key and is irreversible.
- Data encrypted by the deleted key cannot be recovered, once the key is deleted.
- AWS recommends disabling the key before deleting it.
- AWS Managed and Owned keys cannot be deleted. Only Customer managed keys can be scheduled for deletion.
- KMS never deletes the keys unless you explicitly schedule them for deletion and the mandatory waiting period expires.
- KMS requires setting a waiting period of 7-30 days for key deletion. During the waiting period, the KMS key status and key state is Pending deletion.
- Key pending deletion cannot be used in any cryptographic operations.
- Key material of keys that are pending deletion is not rotated.
KMS Multi-Region Keys
- AWS KMS supports multi-region keys, which are AWS KMS keys in different AWS Regions that can be used interchangeably – as though you had the same key in multiple Regions.
- Multi-Region keys have the same key material and key ID, so data can be encrypted in one AWS Region and decrypted in a different AWS Region without re-encrypting or making a cross-Region call to AWS KMS.
- Multi-Region keys never leave AWS KMS unencrypted.
- Multi-Region keys are not global and each multi-region key needs to be replicated and managed independently.
KMS Features
- Create keys with a unique alias and description
- Import your own keys
- Control which IAM users and roles can manage keys
- Control which IAM users and roles can use keys to encrypt & decrypt data
- Choose to have AWS KMS automatically rotate keys on an annual basis
- Temporarily disable keys so they cannot be used by anyone
- Re-enable disabled keys
- Delete keys that you no longer use
- Audit use of keys by inspecting logs in AWS CloudTrail
KMS with VPC Interface Endpoint
- AWS KMS can be connected through a private interface endpoint in the Virtual Private Cloud (VPC).
- Interface VPC endpoint ensures the communication between the VPC and AWS KMS is conducted entirely within the AWS network.
- Interface VPC endpoint connects the VPC directly to KMS without an internet gateway, NAT device, VPN, or Direct Connect connection.
- Instances in the VPC do not need public IP addresses to communicate with AWS KMS.
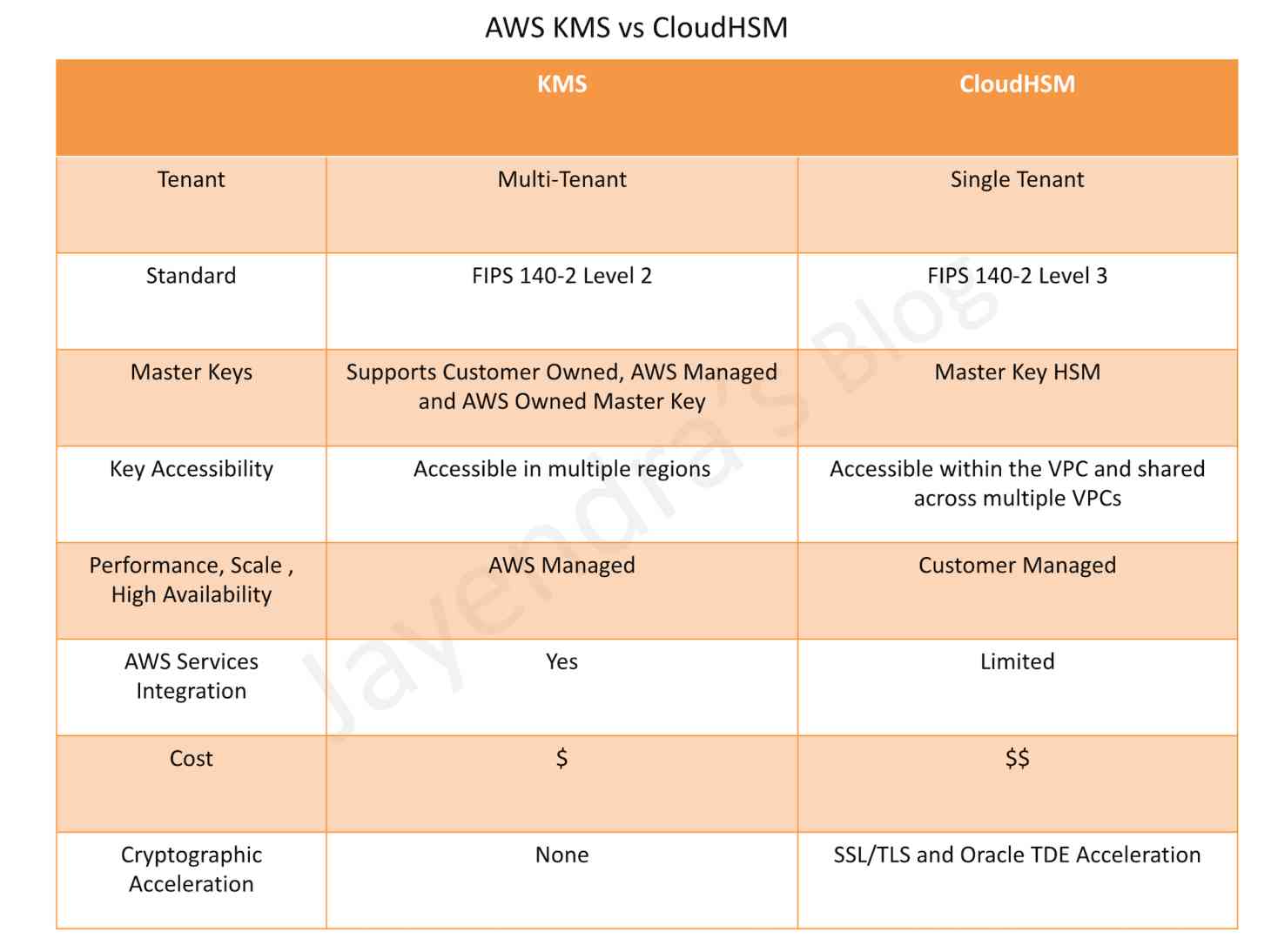
KMS vs CloudHSM
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- You are designing a personal document-archiving solution for your global enterprise with thousands of employee. Each employee has potentially gigabytes of data to be backed up in this archiving solution. The solution will be exposed to he employees as an application, where they can just drag and drop their files to the archiving system. Employees can retrieve their archives through a web interface. The corporate network has high bandwidth AWS DirectConnect connectivity to AWS. You have regulatory requirements that all data needs to be encrypted before being uploaded to the cloud. How do you implement this in a highly available and cost efficient way?
- Manage encryption keys on-premise in an encrypted relational database. Set up an on-premises server with sufficient storage to temporarily store files and then upload them to Amazon S3, providing a client-side master key. (Storing temporary increases cost and not a high availability option)
- Manage encryption keys in a Hardware Security Module (HSM) appliance on-premise server with sufficient storage to temporarily store, encrypt, and upload files directly into amazon Glacier. (Not cost effective)
- Manage encryption keys in amazon Key Management Service (KMS), upload to amazon simple storage service (s3) with client-side encryption using a KMS customer master key ID and configure Amazon S3 lifecycle policies to store each object using the amazon glacier storage tier. (With CSE-KMS the encryption happens at client side before the object is upload to S3 and KMS is cost effective as well)
- Manage encryption keys in an AWS CloudHSM appliance. Encrypt files prior to uploading on the employee desktop and then upload directly into amazon glacier (Not cost effective)
- An AWS customer is deploying an application that is composed of an Auto Scaling group of EC2 Instances. The customers security policy requires that every outbound connection from these instances to any other service within the customers Virtual Private Cloud must be authenticated using a unique x 509 certificate that contains the specific instance-id. In addition an x 509 certificates must be designed by the customer’s Key management service in order to be trusted for authentication.
Which of the following configurations will support these requirements?- Configure an IAM Role that grants access to an Amazon S3 object containing a signed certificate and configure the Auto Scaling group to launch instances with this role. Have the instances bootstrap get the certificate from Amazon S3 upon first boot.
- Embed a certificate into the Amazon Machine Image that is used by the Auto Scaling group Have the launched instances generate a certificate signature request with the instance’s assigned instance-id to the Key management service for signature.
- Configure the Auto Scaling group to send an SNS notification of the launch of a new instance to the trusted key management service. Have the Key management service generate a signed certificate and send it directly to the newly launched instance.
- Configure the launched instances to generate a new certificate upon first boot. Have the Key management service poll the AutoScaling group for associated instances and send new instances a certificate signature that contains the specific instance-id.
- A company has a customer master key (CMK) with imported key materials. Company policy requires that all encryption keys must be rotated every year. What can be done to implement the above policy?
- Enable automatic key rotation annually for the CMK.
- Use AWS Command Line interface to create an AWS Lambda function to rotate the existing CMK annually.
- Import new key material to the existing CMK and manually rotate the CMK.
- Create a new CMK, import new key material to it, and point the key alias to the new CMK.
- An organization policy states that all encryption keys must be automatically rotated every 12 months. Which AWS Key Management Service (KMS) key type should be used to meet this requirement? (Select TWO)
- AWS managed Customer Master Key (CMK) (Now supports every year. It was every 3 years before.)
- Customer managed CMK with AWS generated key material
- Customer managed CMK with imported key material
- AWS managed data key
- AWS managed Customer Master Key (CMK) (Now supports every year. It was every 3 years before.)
Hi,
ARE U Preparing for SA Pro???
yup preparing for SA pro currently …..
Gr8!!!
Have u cleared SysOps Associate? As I am preparing for that… If u have any material pls pass….
I have cleared Solution Architect Associate and Developer Associate recently….
Have cleared Sys Ops Associate and the Blog covers almost all topics for Sysops Associate.
Ok… Thank you!!! will definitely going through it…
What major services required for SysOps?
For Sys Ops, the services are same as Solution Architect but a bit of focus more on monitoring, troubleshooting, CloudWatch, CloudFormation and other deployment options etc.
Hi Jay,
Cleared, AWS SysOps Associate… With 87%…
With this , all 3 Associate done…
What next to be…SA Pro Or DevOps…
I Am not coming from AWS background or not currently working on AWS platform…
Depends what you want to concentrate on … devops stream or an architect stream …
SA Pro covers most of the topics so you may want to check that.
Hey..
I have booked SA Associate on 10th/Feb/2017..
So please help..all this questions will come in exam or not ???
And please provide me with the resources please..
there is no guarantee the questions with come in exam but quite are few are actual exam questions, but might not help you clear the exam. So read up the concepts for each blog topic, have a bits of hands on, reach whitepapers. You can use the blog as resource, covers SA Associate topics.
Can anyone explain which Answer is correct. A or B ?
Which option for the use of the AWS Key Management Service (KMS) supports key management best practices that focus on minimizing the potential scope of data exposed by a possible future key compromise?
A. Use KMS automatic key rotation to replace the master key, and use this new master key for future encryption operations without re-encrypting previously encrypted data.
B. Generate a new Customer Master Key (CMK), re-encrypt all existing data with the new CMK, and use it for all future encryption operations.
C. Change the CMK alias every 90 days, and update key-calling applications with the new key alias.
D. Change the CMK permissions to ensure that individuals who can provision keys are not the same individuals who can use the keys.
A should work with automatic rotation and encrypting the new data, so even if a key is compromised only limited data is exposed.
Thanks a lot.
Hi Jay,
First of all thanks for taking the time to collect all this material and sharing your knowledge.
Bit confused between options c and d for question 3. Is c better than d since it would not involve updating the alias? Also, for c, once we import new key material to an existing CMK, what else needs to be done to manually rotate the key?
Thanks,
Suresh
Question #3
It looks like D should be the correct answer.
You can’t import different key material into a CMK with imported key material – https://docs.aws.amazon.com/kms/latest/developerguide/importing-keys.html#reimport-key-material
Rotating a key with imported key material requires creating a new key and updating the alias – https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html#rotate-keys-manually
A company has a customer master key (CMK) with imported key materials. Company policy requires that all encryption keys must be rotated every year. What can be done to implement the above policy?
a.Enable automatic key rotation annually for the CMK.
b.Use AWS Command Line interface to create an AWS Lambda function to rotate the existing CMK annually.
c.Import new key material to the existing CMK and manually rotate the CMK.
d.Create a new CMK, import new key material to it, and point the key alias to the new CMK..
Hi,
In above question, the correct answer marked as “C”. But the AWS documentation says you cannot import new key material into existing CMK. You can only reimport existing key material. I believe the answer is ‘d’ for above question. Please clarify. thanks.
import-key-material
Description
Imports key material into an existing symmetric AWS KMS customer master key (CMK) that was created without key material. After you successfully import key material into a CMK, you can reimport the same key material into that CMK, but you cannot import different key material.
thanks Ahmed, agreed the answer must be D. Corrected the same.