AWS DDoS Resiliency Whitepaper
- Denial of Service (DoS) is an attack, carried out by a single attacker, which attempts to make a website or application unavailable to the end users.
- Distributed Denial of Service (DDoS) is an attack, carried out by multiple attackers either controlled or compromised by a group of collaborators, which generates a flood of requests to the application making in unavailable to the legitimate end users
Mitigation techniques
Minimize the Attack Surface Area
- This is all all about reducing the attack surface, the different Internet entry points, that allows access to your application
- Strategy to minimize the Attack surface area
- reduce the number of necessary Internet entry points,
- don’t expose back end servers,
- eliminate non-critical Internet entry points,
- separate end user traffic from management traffic,
- obfuscate necessary Internet entry points to the level that untrusted end users cannot access them, and
- decouple Internet entry points to minimize the effects of attacks.
- Benefits
- Minimizes the effective attack vectors and targets
- Less to monitor and protect
- Strategy can be achieved using AWS Virtual Private Cloud (VPC)
- helps define a logically isolated virtual network within the AWS
- provides ability to create Public & Private Subnets to launch the internet facing and non-public facing instances accordingly
- provides NAT gateway which allows instances in the private subnet to have internet access without the need to launch them in public subnets with Public IPs
- allows creation of Bastion host which can be used to connect to instances in the private subnets
- provides the ability to configure security groups for instances and NACLs for subnets, which act as a firewall, to control and limit outbound and inbound traffic
Be Ready to Scale to Absorb the Attack
- DDOS mainly targets to load the systems till the point they cannot handle the load and are rendered unusable.
- Scaling out Benefits
- help build a resilient architecture
- makes the attacker work harder
- gives you time to think, analyze and adapt
- AWS provided services :-
- Auto Scaling & ELB
- Horizontal scaling using Auto Scaling with ELB
- Auto Scaling allows instances to be added and removed as the demand changes
- ELB helps distribute the traffic across multiple EC2 instances while acting as a Single point of contact.
- Auto Scaling automatically registers and deregisters EC2 instances with the ELB during scale out and scale in events
- EC2 Instance
- Vertical scaling can be achieved by using appropriate EC2 instance types for e.g. EBS optimized or ones with 10 gigabyte network connectivity to handle the load
- Enhanced Networking
- Use Instances with Enhanced Networking capabilities which can provide high packet-per-second performance, low latency networking, and improved scalability
- Amazon CloudFront
- CloudFront is a CDN, acts as a proxy between end users and the Origin servers, and helps distribute content to the end users without sending traffic to the Origin servers.
- CloudFront has the inherent ability to help mitigate against both infrastructure and some application layer DDoS attacks by dispersing the traffic across multiple locations.
- AWS has multiple Internet connections for capacity and redundancy at each location, which allows it to isolate attack traffic while serving content to legitimate end users
- CloudFront also has filtering capabilities to ensure that only valid TCP connections and HTTP requests are made while dropping invalid requests. This takes the burden of handling invalid traffic (commonly used in UDP & SYN floods, and slow reads) off the origin.
- Route 53
- DDOS attacks are also targeted towards DNS, cause if the DNS is unavailable your application is effectively unavailable.
- AWS Route 53 is highly available and scalable DNS service and have capabilities to ensure access to the application even when under DDOS attack
- Shuffle Sharding – Shuffle sharding is similar to the concept of database sharding, where horizontal partitions of data are spread across separate database servers to spread load and provide redundancy. Similarly, Amazon Route 53 uses shuffle sharding to spread DNS requests over numerous PoPs, thus providing multiple paths and routes for your application.
- Anycast Routing – Anycast routing increases redundancy by advertising the same IP address from multiple PoPs. In the event that a DDoS attack overwhelms one endpoint, shuffle sharding isolate failures while providing additional routes to your infrastructure.
- Auto Scaling & ELB
Safeguard Exposed & Hard to Scale Expensive Resources
- If entry points cannot be limited, additional measures to restrict access and protect those entry points without interrupting legitimate end user traffic
- AWS provided services :-
- CloudFront
- CloudFront can restrict access to content using Geo Restriction and Origin Access Identity
- With Geo Restriction, access can be restricted to a set of whitelisted countries or prevent access from a set of black listed countries
- Origin Access Identity is the CloudFront special user which allows access to the resources only through CloudFront while denying direct access to the origin content for e.g. if S3 is the Origin for CloudFront, S3 can be configured to allow access only from OAI and hence deny direct access
- Route 53
- Route 53 provides two features Alias Record sets & Private DNS to make it easier to scale infrastructure and respond to DDoS attacks
- WAF
- WAFs act as filters that apply a set of rules to web traffic. Generally, these rules cover exploits like cross-site scripting (XSS) and SQL injection (SQLi) but can also help build resiliency against DDoS by mitigating HTTP GET or POST floods
- WAF provides a lot of features like
- OWASP Top 10
- HTTP rate limiting (where only a certain number of requests are allowed per user in a timeframe),
- Whitelist or blacklist (customizable rules)
- inspect and identify requests with abnormal patterns,
- CAPTCHA etc
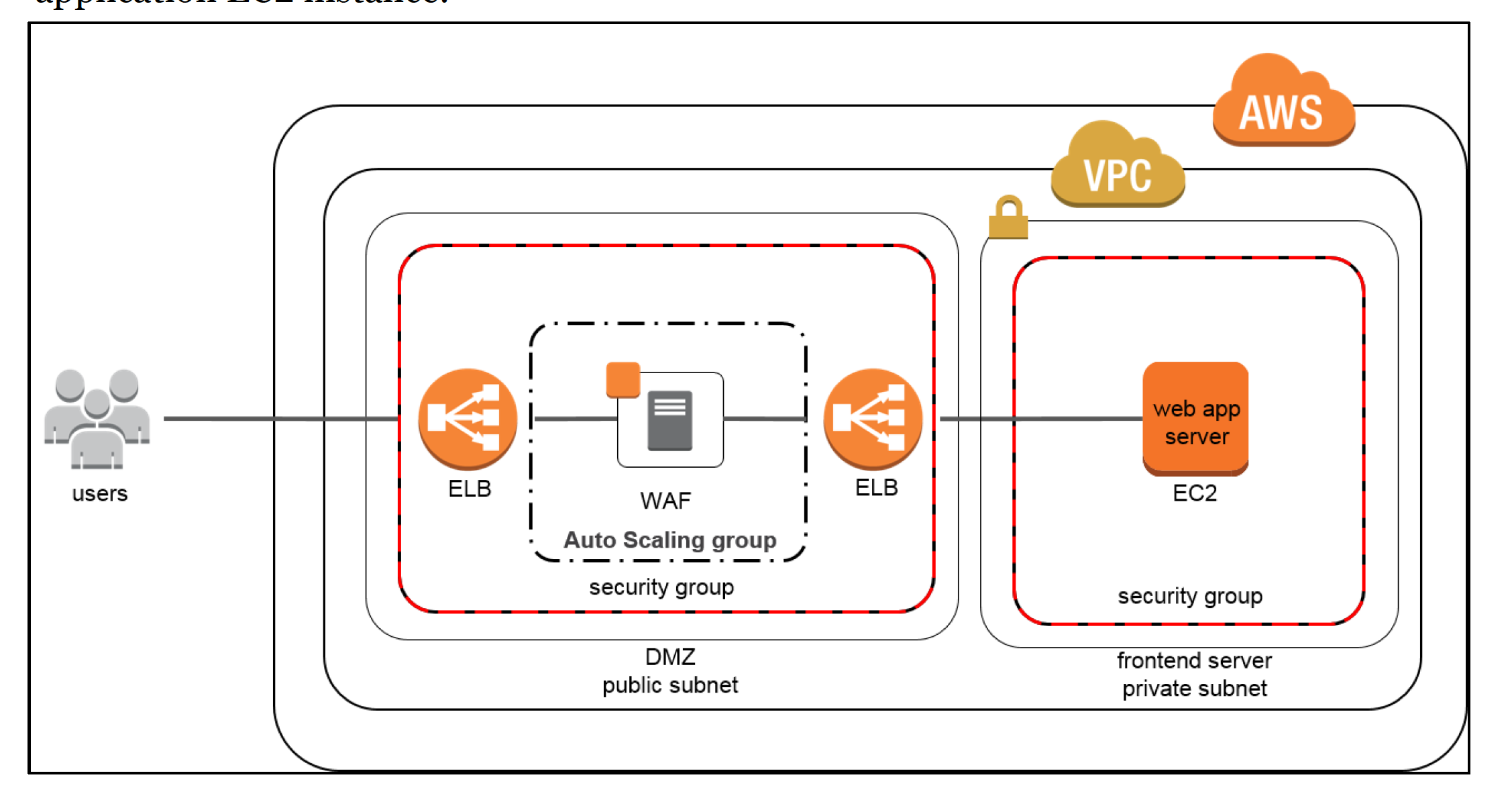
- To prevent WAF from being a Single point of failure, a WAF sandwich pattern can be implemented where an autoscaled WAF sits between the Internet and Internal Load Balancer
- CloudFront
Learn Normal Behavior
- Understand the normal usual levels and Patterns of traffic for your application and use that as a benchmark for identifying abnormal level of traffic or resource spikes patterns
- Benefits
- allows one to spot abnormalities
- configure Alarms with accurate thresholds
- assists with generating forensic data
- AWS provided services for tracking
- AWS CloudWatch monitoring
- CloudWatch can be used to monitor your infrastructure and applications running in AWS. Amazon CloudWatch can collect metrics, log files, and set alarms for when these metrics have passed predetermined thresholds
- VPC Flow Logs
- Flow logs helps capture traffic to the Instances in an VPC and can be used to understand the pattern
- AWS CloudWatch monitoring
Create a Plan for Attacks
- Have a plan in place before an attack, which ensures that:
- Architecture has been validated and techniques selected work for the infrastructure
- Costs for increased resiliency have been evaluated and the goals of your defense are understood
- Contact points have been identified
AWS Certification Exam Practice Questions
- Questions are collected from Internet and the answers are marked as per my knowledge and understanding (which might differ with yours).
- AWS services are updated everyday and both the answers and questions might be outdated soon, so research accordingly.
- AWS exam questions are not updated to keep up the pace with AWS updates, so even if the underlying feature has changed the question might not be updated
- Open to further feedback, discussion and correction.
- You are designing a social media site and are considering how to mitigate distributed denial-of-service (DDoS) attacks. Which of the below are viable mitigation techniques? (Choose 3 answers)
- Add multiple elastic network interfaces (ENIs) to each EC2 instance to increase the network bandwidth.
- Use dedicated instances to ensure that each instance has the maximum performance possible.
- Use an Amazon CloudFront distribution for both static and dynamic content.
- Use an Elastic Load Balancer with auto scaling groups at the web app and Amazon Relational Database Service (RDS) tiers
- Add alert Amazon CloudWatch to look for high Network in and CPU utilization.
- Create processes and capabilities to quickly add and remove rules to the instance OS firewall.
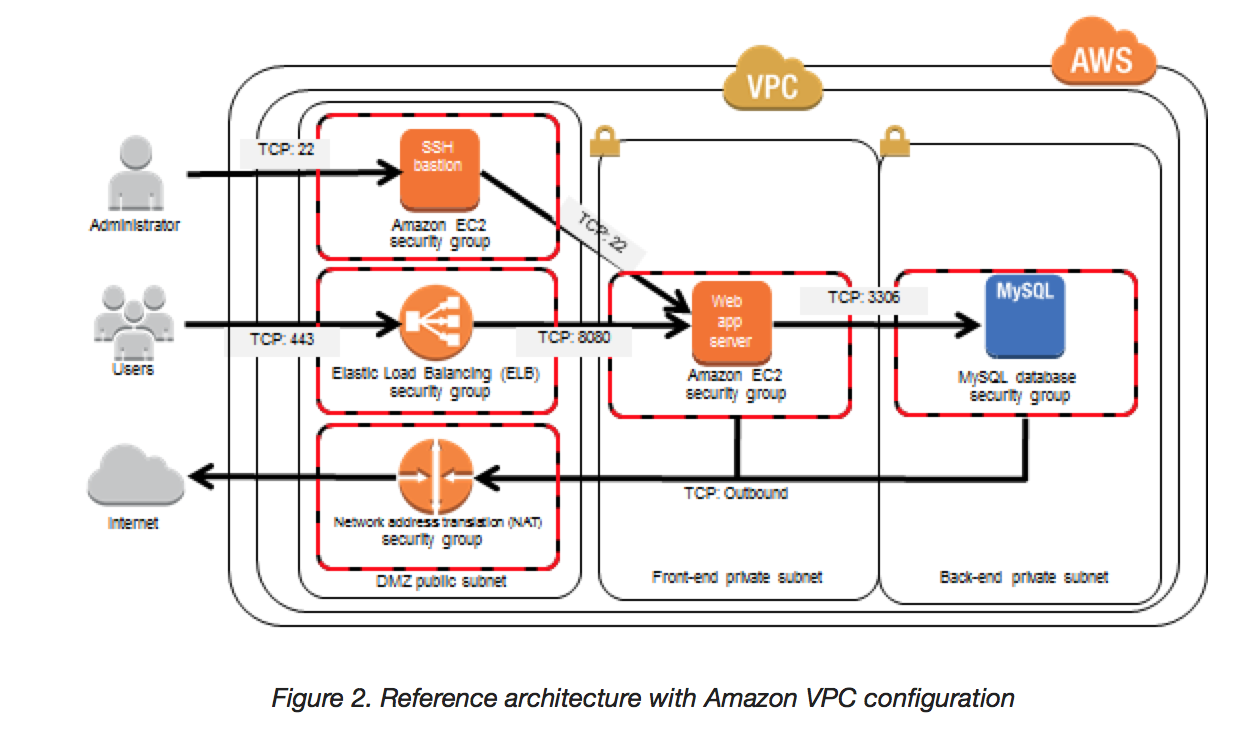
- You’ve been hired to enhance the overall security posture for a very large e-commerce site. They have a well architected multi-tier application running in a VPC that uses ELBs in front of both the web and the app tier with static assets served directly from S3. They are using a combination of RDS and DynamoDB for their dynamic data and then archiving nightly into S3 for further processing with EMR. They are concerned because they found questionable log entries and suspect someone is attempting to gain unauthorized access. Which approach provides a cost effective scalable mitigation to this kind of attack?
- Recommend that they lease space at a DirectConnect partner location and establish a 1G DirectConnect connection to their VPC they would then establish Internet connectivity into their space, filter the traffic in hardware Web Application Firewall (WAF). And then pass the traffic through the DirectConnect connection into their application running in their VPC. (Not cost effective)
- Add previously identified hostile source IPs as an explicit INBOUND DENY NACL to the web tier subnet. (does not protect against new source)
- Add a WAF tier by creating a new ELB and an AutoScaling group of EC2 Instances running a host-based WAF. They would redirect Route 53 to resolve to the new WAF tier ELB. The WAF tier would their pass the traffic to the current web tier The web tier Security Groups would be updated to only allow traffic from the WAF tier Security Group
- Remove all but TLS 1.2 from the web tier ELB and enable Advanced Protocol Filtering This will enable the ELB itself to perform WAF functionality. (No advanced protocol filtering in ELB)
References
Hello,
Use an Elastic Load Balancer with auto scaling groups at the web, App and Amazon Relational Database Service (RDS) tiers
->RDS doesn’t have ELB and ASG. Should be CEF?
Hi Ruoen,
Elastic Load Balancing and Auto Scaling for Web Application is a key for ddos resiliency.
Here the ELB and ASG options doesn’t apply to RDS, but you can use RDS scale out features with Read Replicas, Multi AZ feature for failover to minimize the impact.
Option F is more of an after attack option and with high frequency ddos attacks from multiple sources, this can hardly work.
CDE is correct:
Services that are available within AWS Regions, like Elastic Load Balancing and
Amazon Elastic Compute Cloud (EC2), allow you to build DDoS resiliency and
scale to handle unexpected volumes of traffic within a given region.
Ref :https://d0.awsstatic.com/whitepapers/DDoS_White_Paper_June2015.pdf
Might be correct for the test, but the idea of mitigating an attack with option D means that the bad guys force me to spend more money with spinning up instances. Hardly seems wise. It’s like saying we need more drive through banking lanes so that when robbers clog up the ones you have you can open up additional ones for real customers. I do understand in general ELB provides better security against individual instances.
To prevent WAF from being a Single point of failure, a WAF sandwich pattern can be implemented where an autoscaled WAF sits between the Internet and Internal Load Balancer
Can you explain more about this WAF sandwich pattern, please?
How can we put WAF service between Internet and Internal Load balancer?
The approach is similar to having a web server between the Internet and Internal Load balancer.
So instead of Web Server you would have an auto scaled WAF instances.
Remember this approach was applicable when and AWS WAF was not available and these are 3rd party WAF images which can scale and help route the requests to the internal load balancer.
I think the sandwich architecture is obsoleted, WAF now can associate with ALB or API Gateway, these all are high available service, so we don’t need setup the auto scaling WAF by ourselves
Thats right Aaron, sandwich pattern was before the AWS WAF was introduced.